Exam Details
Exam Code
:312-50V11Exam Name
:EC-Council Certified Ethical Hacker (C|EH v11)Certification
:EC-COUNCIL CertificationsVendor
:EC-COUNCILTotal Questions
:528 Q&AsLast Updated
:Apr 17, 2025
EC-COUNCIL EC-COUNCIL Certifications 312-50V11 Questions & Answers
-
Question 211:
Jim, a professional hacker, targeted an organization that is operating critical Industrial Infrastructure. Jim used Nmap to scan open pons and running services on systems connected to the organization's OT network. He used an Nmap command to identify Ethernet/IP devices connected to the Internet and further gathered Information such as the vendor name, product code and name, device name, and IP address. Which of the following Nmap commands helped Jim retrieve the required information?
A. nmap -Pn -sT --scan-delay 1s --max-parallelism 1 -p < Port List > < Target IP >
B. nmap -Pn -sU -p 44818 --script enip-info < Target IP >
C. nmap -Pn -sT -p 46824 < Target IP >
D. nmap -Pn -sT -p 102 --script s7-info < Target IP >
-
Question 212:
Due to a slowdown of normal network operations, the IT department decided to monitor internet traffic for all of the employees. From a legal standpoint, what would be troublesome to take this kind of measure?
A. All of the employees would stop normal work activities
B. IT department would be telling employees who the boss is
C. Not informing the employees that they are going to be monitored could be an invasion of privacy.
D. The network could still experience traffic slow down.
-
Question 213:
Which of the following tools are used for enumeration? (Choose three.)
A. SolarWinds
B. USER2SID
C. Cheops
D. SID2USER
E. DumpSec
-
Question 214:
You are tasked to configure the DHCP server to lease the last 100 usable IP addresses in subnet to. 1.4.0/23. Which of the following IP addresses could be teased as a result of the new configuration?
A. 210.1.55.200
B. 10.1.4.254
C. 10..1.5.200
D. 10.1.4.156
-
Question 215:
Which of the following is a passive wireless packet analyzer that works on Linux-based systems?
A. Burp Suite
B. OpenVAS
C. tshark
D. Kismet
-
Question 216:
Which service in a PKI will vouch for the identity of an individual or company?
A. KDC
B. CR
C. CBC
D. CA
-
Question 217:
Which tier in the N-tier application architecture is responsible for moving and processing data between the tiers?
A. Presentation tier
B. Application Layer
C. Logic tier
D. Data tier
-
Question 218:
Bob, your senior colleague, has sent you a mail regarding a deal with one of the clients. You are requested to accept the offer and you oblige. After 2 days. Bob denies that he had ever sent a mail. What do you want to ""know"" to prove yourself that it was Bob who had send a mail?
A. Authentication
B. Confidentiality
C. Integrity
D. Non-Repudiation
-
Question 219:
What is correct about digital signatures?
A. A digital signature cannot be moved from one signed document to another because it is the hash of the original document encrypted with the private key of the signing party.
B. Digital signatures may be used in different documents of the same type.
C. A digital signature cannot be moved from one signed document to another because it is a plain hash of the document content.
D. Digital signatures are issued once for each user and can be used everywhere until they expire.
-
Question 220:
ViruXine.W32 virus hides their presence by changing the underlying executable code.
This Virus code mutates while keeping the original algorithm intact, the code changes itself each time it runs, but the function of the code (its semantics) will not change at all.
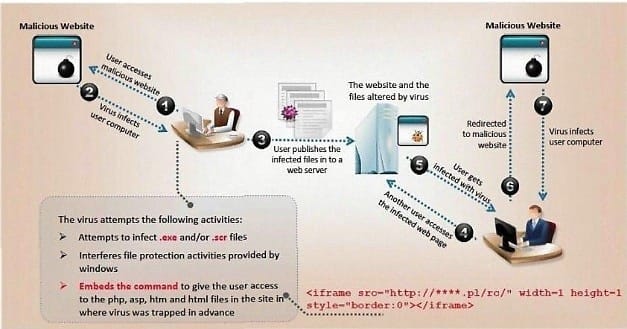
Here is a section of the Virus code:
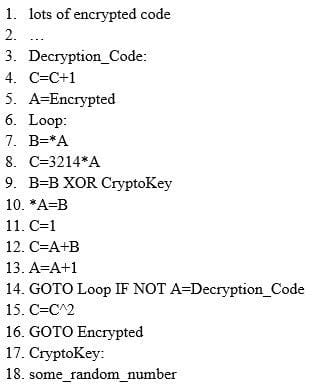
What is this technique called?
A. Polymorphic Virus
B. Metamorphic Virus
C. Dravidic Virus
D. Stealth Virus
Related Exams:
112-51
EC-Council Certified Network Defense Essentials (NDE)212-77
EC-Council Certified Linux Security212-81
EC-Council Certified Encryption Specialist (ECES)212-82
EC-Council Certified Cybersecurity Technician (C|CT)212-89
EC-Council Certified Incident Handler (ECIH)312-38
EC-Council Certified Network Defender (CND)312-39
EC-Council Certified SOC Analyst (CSA)312-40
EC-Council Certified Cloud Security Engineer (CCSE)312-49
ECCouncil Computer Hacking Forensic Investigator (V9)312-49V10
EC-Council Certified Computer Hacking Forensic Investigator (V10)
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only EC-COUNCIL exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your 312-50V11 exam preparations and EC-COUNCIL certification application, do not hesitate to visit our Vcedump.com to find your solutions here.