Exam Details
Exam Code
:312-50V11Exam Name
:EC-Council Certified Ethical Hacker (C|EH v11)Certification
:EC-COUNCIL CertificationsVendor
:EC-COUNCILTotal Questions
:528 Q&AsLast Updated
:Apr 17, 2025
EC-COUNCIL EC-COUNCIL Certifications 312-50V11 Questions & Answers
-
Question 301:
While using your bank's online servicing you notice the following string in the URL bar:
"http: // www. MyPersonalBank.com/account?id=368940911028389andDamount=10980andCamount=21"
You observe that if you modify the Damount and Camount values and submit the request, that data on the web page reflects the changes.
Which type of vulnerability is present on this site?
A. Cookie Tampering
B. SQL Injection
C. Web Parameter Tampering
D. XSS Reflection
-
Question 302:
Bob, an attacker, has managed to access a target loT device. He employed an online tool to gather information related to the model of the loT device and the certifications granted to it. Which of the following tools did Bob employ to gather the above Information?
A. search.com
B. EarthExplorer
C. Google image search
D. FCC ID search
-
Question 303:
Tony wants to integrate a 128-bit symmetric block cipher with key sizes of 128,192, or 256 bits into a software program, which involves 32 rounds of computational operations that include substitution and permutation operations on four 32-bit word blocks using 8-variable S-boxes with 4-bit entry and 4-bit exit. Which of the following algorithms includes all the above features and can be integrated by Tony into the software program?
A. TEA
B. CAST-128
C. RC5
D. serpent
-
Question 304:
As a Certified Ethical Hacker, you were contracted by a private firm to conduct an external security assessment through penetration testing.
What document describes the specifics of the testing, the associated violations, and essentially protects both the organization's interest and your liabilities as a tester?
A. Service Level Agreement
B. Project Scope
C. Rules of Engagement
D. Non-Disclosure Agreement
-
Question 305:
At what stage of the cyber kill chain theory model does data exfiltration occur?
A. Actions on objectives
B. Weaponization
C. installation
D. Command and control
-
Question 306:
A group of hackers were roaming around a bank office building in a city, driving a luxury car. They were using hacking tools on their laptop with the intention to find a free-access wireless network. What is this hacking process known as?
A. GPS mapping
B. Spectrum analysis
C. Wardriving
D. Wireless sniffing
-
Question 307:
env x='(){ :;};echo exploit' bash -c `cat/etc/passwd'
What is the Shellshock bash vulnerability attempting to do on a vulnerable Linux host?
A. Removes the passwd file
B. Changes all passwords in passwd
C. Add new user to the passwd file
D. Display passwd content to prompt
-
Question 308:
The network in ABC company is using the network address 192.168.1.64 with mask 255.255.255.192. In the network the servers are in the addresses 192.168.1.122, 192.168.1.123 and 192.168.1.124. An attacker is trying to find those servers but he cannot see them in his scanning. The command he is using is: nmap 192.168.1.64/28.
Why he cannot see the servers?
A. He needs to add the command ""ip address"" just before the IP address
B. He needs to change the address to 192.168.1.0 with the same mask
C. He is scanning from 192.168.1.64 to 192.168.1.78 because of the mask /28 and the servers are not in that range
D. The network must be dawn and the nmap command and IP address are ok
-
Question 309:
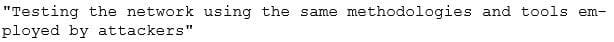
Identify the correct terminology that defines the above statement.
A. Vulnerability Scanning
B. Penetration Testing
C. Security Policy Implementation
D. Designing Network Security
-
Question 310:
An attacker changes the profile information of a particular user (victim) on the target website. The attacker uses this string to update the victim's profile to a text file and then submit the data to the attacker's database.
< iframe src=""http://www.vulnweb.com/updateif.php"" style=""display:none"" > < /iframe >
What is this type of attack (that can use either HTTP GET or HTTP POST) called?
A. Browser Hacking
B. Cross-Site Scripting
C. SQL Injection
D. Cross-Site Request Forgery
Related Exams:
112-51
EC-Council Certified Network Defense Essentials (NDE)212-77
EC-Council Certified Linux Security212-81
EC-Council Certified Encryption Specialist (ECES)212-82
EC-Council Certified Cybersecurity Technician (C|CT)212-89
EC-Council Certified Incident Handler (ECIH)312-38
EC-Council Certified Network Defender (CND)312-39
EC-Council Certified SOC Analyst (CSA)312-40
EC-Council Certified Cloud Security Engineer (CCSE)312-49
ECCouncil Computer Hacking Forensic Investigator (V9)312-49V10
EC-Council Certified Computer Hacking Forensic Investigator (V10)
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only EC-COUNCIL exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your 312-50V11 exam preparations and EC-COUNCIL certification application, do not hesitate to visit our Vcedump.com to find your solutions here.