Exam Details
Exam Code
:312-50V11Exam Name
:EC-Council Certified Ethical Hacker (C|EH v11)Certification
:EC-COUNCIL CertificationsVendor
:EC-COUNCILTotal Questions
:528 Q&AsLast Updated
:Apr 09, 2025
EC-COUNCIL EC-COUNCIL Certifications 312-50V11 Questions & Answers
-
Question 471:
You are a penetration tester working to test the user awareness of the employees of the client xyz. You
harvested two employees' emails from some public sources and are creating a client-side backdoor to
send it to the employees via email.
Which stage of the cyber kill chain are you at?
A. Reconnaissance
B. Command and control
C. Weaponization
D. Exploitation
-
Question 472:
An Intrusion Detection System (IDS) has alerted the network administrator to a possibly malicious
sequence of packets sent to a Web server in the network's external DMZ. The packet traffic was captured
by the IDS and saved to a PCAP file.
What type of network tool can be used to determine if these packets are genuinely malicious or simply a
false positive?
A. Protocol analyzer
B. Network sniffer
C. Intrusion Prevention System (IPS)
D. Vulnerability scanner
-
Question 473:
Harris is attempting to identify the OS running on his target machine. He inspected the initial TTL in the IP header and the related TCP window size and obtained the following results:
TTL: 64 Window Size: 5840
What is the OS running on the target machine?
A. Solaris OS
B. Windows OS
C. Mac OS
D. Linux OS
-
Question 474:
Which type of security feature stops vehicles from crashing through the doors of a building?
A. Bollards
B. Receptionist
C. Mantrap
D. Turnstile
-
Question 475:
A new wireless client is configured to join a 802.11 network. This client uses the same hardware and
software as many of the other clients on the network. The client can see the network, but cannot connect.
A wireless packet sniffer shows that the Wireless Access Point (WAP) is not responding to the association
requests being sent by the wireless client.
What is a possible source of this problem?
A. The WAP does not recognize the client's MAC address
B. The client cannot see the SSID of the wireless network
C. Client is configured for the wrong channel
D. The wireless client is not configured to use DHCP
-
Question 476:
A DDOS attack is performed at layer 7 to take down web infrastructure. Partial HTTP requests are sent to
the web infrastructure or applications. Upon receiving a partial request, the target servers opens multiple
connections and keeps waiting for the requests to complete.
Which attack is being described here?
A. Desynchronization
B. Slowloris attack
C. Session splicing
D. Phlashing
-
Question 477:
Which of the following viruses tries to hide from anti-virus programs by actively altering and corrupting the chosen service call interruptions when they are being run?
A. Macro virus
B. Stealth/Tunneling virus
C. Cavity virus
D. Polymorphic virus
-
Question 478:
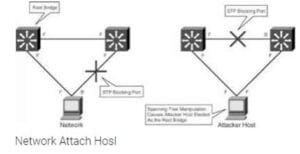
Robin, a professional hacker, targeted an organization's network to sniff all the traffic. During this process.
Robin plugged in a rogue switch to an unused port in the LAN with a priority lower than any other switch in the network so that he could make it a root bridge that will later allow him to sniff all the traffic in the network.
What is the attack performed by Robin in the above scenario?
A. ARP spoofing attack
B. VLAN hopping attack
C. DNS poisoning attack
D. STP attack
-
Question 479:
Bob is acknowledged as a hacker of repute and is popular among visitors of "underground" sites.
Bob is willing to share his knowledge with those who are willing to learn, and many have expressed their interest in learning from him. However, this knowledge has a risk associated with it, as it can be used for malevolent attacks as well. In this context, what would be the most effective method to bridge the knowledge gap between the "black" hats or crackers and the "white" hats or computer security professionals? (Choose the test answer.)
A. Educate everyone with books, articles and training on risk analysis, vulnerabilities and safeguards.
B. Hire more computer security monitoring personnel to monitor computer systems and networks.
C. Make obtaining either a computer security certification or accreditation easier to achieve so more individuals feel that they are a part of something larger than life.
D. Train more National Guard and reservist in the art of computer security to help out in times of emergency or crises.
-
Question 480:
Daniel Is a professional hacker who Is attempting to perform an SQL injection attack on a target website. www.movlescope.com. During this process, he encountered an IDS that detects SQL Injection attempts based on predefined signatures. To evade any comparison statement, he attempted placing characters such as `'or '1'='1" In any bask injection statement such as "or 1=1." Identify the evasion technique used by Daniel in the above scenario.
A. Null byte
B. IP fragmentation
C. Char encoding
D. Variation
Related Exams:
112-51
EC-Council Certified Network Defense Essentials (NDE)212-77
EC-Council Certified Linux Security212-81
EC-Council Certified Encryption Specialist (ECES)212-82
EC-Council Certified Cybersecurity Technician (C|CT)212-89
EC-Council Certified Incident Handler (ECIH)312-38
EC-Council Certified Network Defender (CND)312-39
EC-Council Certified SOC Analyst (CSA)312-40
EC-Council Certified Cloud Security Engineer (CCSE)312-49
ECCouncil Computer Hacking Forensic Investigator (V9)312-49V10
EC-Council Certified Computer Hacking Forensic Investigator (V10)
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only EC-COUNCIL exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your 312-50V11 exam preparations and EC-COUNCIL certification application, do not hesitate to visit our Vcedump.com to find your solutions here.