Exam Details
Exam Code
:312-50V12Exam Name
:EC-Council Certified Ethical Hacker (C|EH v12)Certification
:EC-COUNCIL CertificationsVendor
:EC-COUNCILTotal Questions
:596 Q&AsLast Updated
:Apr 16, 2025
EC-COUNCIL EC-COUNCIL Certifications 312-50V12 Questions & Answers
-
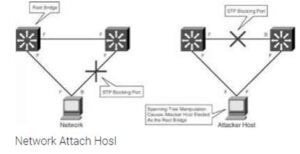
Question 551:
Robin, a professional hacker, targeted an organization's network to sniff all the traffic. During this process, Robin plugged in a rogue switch to an unused port in the LAN with a priority lower than any other switch in the network, making it the root bridge that would later allow him to sniff all the traffic in the network.
What is the attack performed by Robin in the above scenario?
A. ARP spoofing attack
B. VLAN hopping attack
C. DNS poisoning attack
D. STP attack
-
Question 552:
Hackers often raise the trust level of a phishing message by modeling the email to look similar to the internal email used by the target company. This includes using logos, formatting, and names of the target company. The phishing message will often use the name of the company CEO, President, or Managers. The time a hacker spends performing research to locate this information about a company is known as?
A. Exploration
B. Investigation
C. Reconnaissance
D. Enumeration
-
Question 553:
Which of the following tools is used to detect wireless LANs using the 802.11a/b/g/n WLAN standards on a linux platform?
A. Kismet
B. Abel
C. Netstumbler
D. Nessus
-
Question 554:
Which of the following commands checks for valid users on an SMTP server?
A. RCPT
B. CHK
C. VRFY
D. EXPN
-
Question 555:
What ports should be blocked on the firewall to prevent NetBIOS traffic from not coming through the firewall if your network is comprised of Windows NT, 2000, and XP?
A. 110
B. 135
C. 139
D. 161
E. 445
F. 1024
-
Question 556:
An attacker, using a rogue wireless AP, performed an MITM attack and injected an HTML code to embed a malicious applet in all HTTP connections. When users accessed any page, the applet ran and exploited many machines. Which one of the following tools the hacker probably used to inject HTML code?
A. Wireshark
B. Ettercap
C. Aircrack-ng
D. Tcpdump
-
Question 557:
Which file is a rich target to discover the structure of a website during web-server footprinting?
A. Document root
B. Robots.txt
C. domain.txt
D. index.html
-
Question 558:
What type of virus is most likely to remain undetected by antivirus software?
A. Cavity virus
B. Stealth virus
C. File-extension virus
D. Macro virus
-
Question 559:
What do Trinoo, TFN2k, WinTrinoo, T-Sight, and Stracheldraht have in common?
A. All are hacking tools developed by the legion of doom
B. All are tools that can be used not only by hackers, but also security personnel
C. All are DDOS tools
D. All are tools that are only effective against Windows
E. All are tools that are only effective against Linux
-
Question 560:
Jim's company regularly performs backups of their critical servers. But the company cannot afford to send backup tapes to an off-site vendor for long-term storage and archiving. Instead, Jim's company keeps the backup tapes in a safe in the office. Jim's company is audited each year, and the results from this year's audit show a risk because backup tapes are not stored off-site. The Manager of Information Technology has a plan to take the backup tapes home with him and wants to know what two things he can do to secure the backup tapes while in transit?
A. Encrypt the backup tapes and transport them in a lock box.
B. Degauss the backup tapes and transport them in a lock box.
C. Hash the backup tapes and transport them in a lock box.
D. Encrypt the backup tapes and use a courier to transport them.
Related Exams:
112-51
EC-Council Certified Network Defense Essentials (NDE)212-77
EC-Council Certified Linux Security212-81
EC-Council Certified Encryption Specialist (ECES)212-82
EC-Council Certified Cybersecurity Technician (C|CT)212-89
EC-Council Certified Incident Handler (ECIH)312-38
EC-Council Certified Network Defender (CND)312-39
EC-Council Certified SOC Analyst (CSA)312-40
EC-Council Certified Cloud Security Engineer (CCSE)312-49
ECCouncil Computer Hacking Forensic Investigator (V9)312-49V10
EC-Council Certified Computer Hacking Forensic Investigator (V10)
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only EC-COUNCIL exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your 312-50V12 exam preparations and EC-COUNCIL certification application, do not hesitate to visit our Vcedump.com to find your solutions here.