Exam Details
Exam Code
:312-50V8Exam Name
:Certified Ethical Hacker v8Certification
:EC-COUNCIL CertificationsVendor
:EC-COUNCILTotal Questions
:1008 Q&AsLast Updated
:Apr 15, 2025
EC-COUNCIL EC-COUNCIL Certifications 312-50V8 Questions & Answers
-
Question 241:
File extensions provide information regarding the underlying server technology. Attackers can use this information to search vulnerabilities and launch attacks.
How would you disable file extensions in Apache servers?
A. Use disable-eXchange
B. Use mod_negotiation
C. Use Stop_Files
D. Use Lib_exchanges
-
Question 242:
In which location, SAM hash passwords are stored in Windows 7?
A. c:\windows\system32\config\SAM
B. c:\winnt\system32\machine\SAM
C. c:\windows\etc\drivers\SAM
D. c:\windows\config\etc\SAM
-
Question 243:
How do you defend against MAC attacks on a switch?
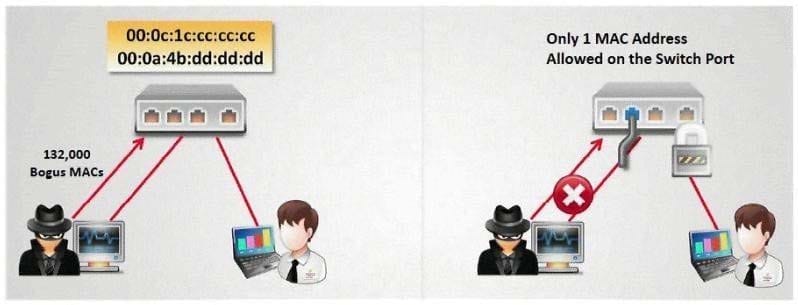
A. Disable SPAN port on the switch
B. Enable SNMP Trap on the switch
C. Configure IP security on the switch
D. Enable Port Security on the switch
-
Question 244:
You have successfully gained access to a victim's computer using Windows 2003 Server SMB Vulnerability.
Which command will you run to disable auditing from the cmd?
A. stoplog stoplog ?
B. EnterPol /nolog
C. EventViewer o service
D. auditpol.exe /disable
-
Question 245:
Your company has blocked all the ports via external firewall and only allows port 80/443 to connect to the Internet. You want to use FTP to connect to some remote server on the Internet.
How would you accomplish this?
A. Use HTTP Tunneling
B. Use Proxy Chaining
C. Use TOR Network
D. Use Reverse Chaining
-
Question 246:
_____________ is a type of symmetric-key encryption algorithm that transforms a fixed-length block of plaintext (unencrypted text) data into a block of ciphertext (encrypted text) data of the same length.
A. Stream Cipher
B. Block Cipher
C. Bit Cipher
D. Hash Cipher
-
Question 247:
E-mail tracking is a method to monitor and spy the delivered e-mails to the intended recipient.
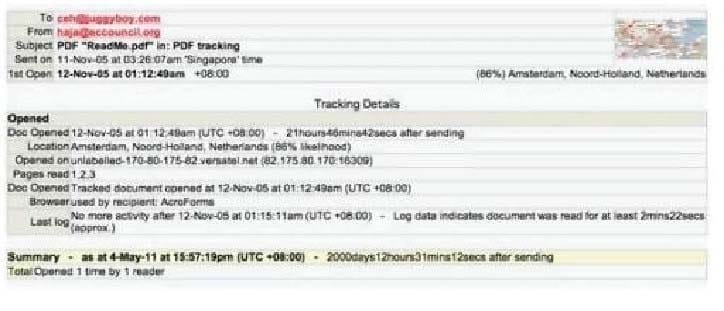
Select a feature, which you will NOT be able to accomplish with this probe?
A. When the e-mail was received and read
B. Send destructive e-mails
C. GPS location and map of the recipient
D. Time spent on reading the e-mails
E. Whether or not the recipient visited any links sent to them
F. Track PDF and other types of attachments
G. Set messages to expire after specified time
H. Remote control the User's E-mail client application and hijack the traffic
-
Question 248:
Which of the following Trojans would be considered 'Botnet Command Control Center'?
A. YouKill DOOM
B. Damen Rock
C. Poison Ivy
D. Matten Kit
-
Question 249:
What type of Virus is shown here?
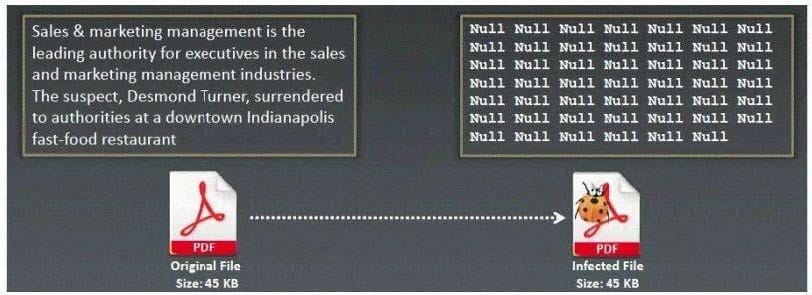
A. Macro Virus
B. Cavity Virus
C. Boot Sector Virus
D. Metamorphic Virus
E. Sparse Infector Virus
-
Question 250:
John is using a special tool on his Linux platform that has a database containing signatures to be able to detect hundreds of vulnerabilities in UNIX, Windows, and commonly used web CGI/ASPX scripts. Moreover, the database detects DDoS zombies and Trojans as well.
What would be the name of this tool?
A. hping2
B. nessus
C. nmap
D. make
Related Exams:
112-51
EC-Council Certified Network Defense Essentials (NDE)212-77
EC-Council Certified Linux Security212-81
EC-Council Certified Encryption Specialist (ECES)212-82
EC-Council Certified Cybersecurity Technician (C|CT)212-89
EC-Council Certified Incident Handler (ECIH)312-38
EC-Council Certified Network Defender (CND)312-39
EC-Council Certified SOC Analyst (CSA)312-40
EC-Council Certified Cloud Security Engineer (CCSE)312-49
ECCouncil Computer Hacking Forensic Investigator (V9)312-49V10
EC-Council Certified Computer Hacking Forensic Investigator (V10)
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only EC-COUNCIL exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your 312-50V8 exam preparations and EC-COUNCIL certification application, do not hesitate to visit our Vcedump.com to find your solutions here.