Exam Details
Exam Code
:312-50V8Exam Name
:Certified Ethical Hacker v8Certification
:EC-COUNCIL CertificationsVendor
:EC-COUNCILTotal Questions
:1008 Q&AsLast Updated
:Apr 15, 2025
EC-COUNCIL EC-COUNCIL Certifications 312-50V8 Questions & Answers
-
Question 501:
A Certificate Authority (CA) generates a key pair that will be used for encryption and decryption of email. The integrity of the encrypted email is dependent on the security of which of the following?
A. Public key
B. Private key
C. Modulus length
D. Email server certificate
-
Question 502:
Which of the following is a hardware requirement that either an IDS/IPS system or a proxy server must have in order to properly function?
A. Fast processor to help with network traffic analysis
B. They must be dual-homed
C. Similar RAM requirements
D. Fast network interface cards
-
Question 503:
Which of the following business challenges could be solved by using a vulnerability scanner?
A. Auditors want to discover if all systems are following a standard naming convention.
B. A web server was compromised and management needs to know if any further systems were compromised.
C. There is an emergency need to remove administrator access from multiple machines for an employee that quit.
D. There is a monthly requirement to test corporate compliance with host application usage and security policies.
-
Question 504:
While checking the settings on the internet browser, a technician finds that the proxy server settings have been checked and a computer is trying to use itself as a proxy server.
What specific octet within the subnet does the technician see?
A. 10.10.10.10
B. 127.0.0.1
C. 192.168.1.1
D. 192.168.168.168
-
Question 505:
What are the three types of authentication?
A. Something you: know,remember,prove
B. Something you: have,know,are
C. Something you: show,prove,are
D. Something you: show,have,prove
-
Question 506:
What are the three types of compliance that the Open Source Security Testing Methodology Manual (OSSTMM) recognizes?
A. Legal,performance,audit
B. Audit,standards based,regulatory
C. Contractual,regulatory,industry
D. Legislative,contractual,standards based
-
Question 507:
A newly discovered flaw in a software application would be considered which kind of security vulnerability?
A. Input validation flaw
B. HTTP header injection vulnerability
C. 0-day vulnerability
D. Time-to-check to time-to-use flaw
-
Question 508:
A tester is attempting to capture and analyze the traffic on a given network and realizes that the network has several switches.
What could be used to successfully sniff the traffic on this switched network? (Choose three.)
A. ARP spoofing
B. MAC duplication
C. MAC flooding
D. SYN flood
E. Reverse smurf attack
F. ARP broadcasting
-
Question 509:
The following is a sample of output from a penetration tester's machine targeting a machine with the IP address of 192.168.1.106:
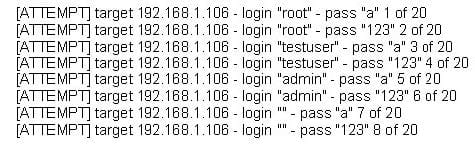
What is most likely taking place?
A. Ping sweep of the 192.168.1.106 network
B. Remote service brute force attempt
C. Port scan of 192.168.1.106
D. Denial of service attack on 192.168.1.106
-
Question 510:
A pentester gains acess to a Windows application server and needs to determine the settings of the built-in Windows firewall.
Which command would be used?
A. Netsh firewall show config
B. WMIC firewall show config
C. Net firewall show config
D. Ipconfig firewall show config
Related Exams:
112-51
EC-Council Certified Network Defense Essentials (NDE)212-77
EC-Council Certified Linux Security212-81
EC-Council Certified Encryption Specialist (ECES)212-82
EC-Council Certified Cybersecurity Technician (C|CT)212-89
EC-Council Certified Incident Handler (ECIH)312-38
EC-Council Certified Network Defender (CND)312-39
EC-Council Certified SOC Analyst (CSA)312-40
EC-Council Certified Cloud Security Engineer (CCSE)312-49
ECCouncil Computer Hacking Forensic Investigator (V9)312-49V10
EC-Council Certified Computer Hacking Forensic Investigator (V10)
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only EC-COUNCIL exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your 312-50V8 exam preparations and EC-COUNCIL certification application, do not hesitate to visit our Vcedump.com to find your solutions here.