Exam Details
Exam Code
:312-50V9Exam Name
:EC-Council Certified Ethical Hacker (C|EH v9)Certification
:EC-COUNCIL CertificationsVendor
:EC-COUNCILTotal Questions
:614 Q&AsLast Updated
:Apr 14, 2025
EC-COUNCIL EC-COUNCIL Certifications 312-50V9 Questions & Answers
-
Question 181:
When analyzing the IDS logs, the system administrator noticed an alert was logged when the external router was accessed from the administrator's computer to update the router configuration. What type of an alert is this?
A. False positive
B. False negative
C. True positve
D. True negative
-
Question 182:
Low humidity in a data center can cause which of the following problems?
A. Heat
B. Corrosion
C. Static electricity
D. Airborne contamination
-
Question 183:
A consultant is hired to do physical penetration testing at a large financial company. In the first day of his assessment, the consultant goes to the company`s building dressed like an electrician and waits in the lobby for an employee to pass through the main access gate, then the consultant follows the employee behind to get into the restricted area. Which type of attack did the consultant perform?
A. Man trap
B. Tailgating
C. Shoulder surfing
D. Social engineering
-
Question 184:
Which property ensures that a hash function will not produce the same hashed value for two different messages?
A. Collision resistance
B. Bit length
C. Key strength
D. Entropy
-
Question 185:
How can telnet be used to fingerprint a web server?
A. telnet webserverAddress 80 HEAD / HTTP/1.0
B. telnet webserverAddress 80 PUT / HTTP/1.0
C. telnet webserverAddress 80 HEAD / HTTP/2.0
D. telnet webserverAddress 80 PUT / HTTP/2.0
-
Question 186:
A computer science student needs to fill some information into a secured Adobe PDF job application that was received from a prospective employer. Instead of requesting a new document that allowed the forms to be completed, the student decides to write a script that pulls passwords from a list of commonly used passwords to try against the secured PDF until the correct password is found or the list is exhausted.
Which cryptography attack is the student attempting?
A. Man-in-the-middle attack
B. Brute-force attack
C. Dictionary attack
D. Session hijacking
-
Question 187:
Which of the following is a symmetric cryptographic standard?
A. DSA
B. PKI
C. RSA
D. 3DES
-
Question 188:
A circuit level gateway works at which of the following layers of the OSI Model?
A. Layer 5 - Application
B. Layer 4 ?TCP
C. Layer 3 ?Internet protocol
D. Layer 2 ?Data link
-
Question 189:
A company firewall engineer has configured a new DMZ to allow public systems to be located away from the internal network. The engineer has three security zones set:
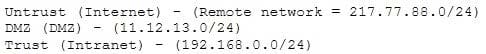
The engineer wants to configure remote desktop access from a fixed IP on the remote network to a remote desktop server in the DMZ. Which rule would best fit this requirement?
A. Permit 217.77.88.0/24 11.12.13.0/24 RDP 3389
B. Permit 217.77.88.12 11.12.13.50 RDP 3389
C. Permit 217.77.88.12 11.12.13.0/24 RDP 3389
D. Permit 217.77.88.0/24 11.12.13.50 RDP 3389
-
Question 190:
Windows file servers commonly hold sensitive files, databases, passwords and more. Which of the following choices would be a common vulnerability that usually exposes them?
A. Cross-site scripting
B. SQL injection
C. Missing patches
D. CRLF injection
Related Exams:
112-51
EC-Council Certified Network Defense Essentials (NDE)212-77
EC-Council Certified Linux Security212-81
EC-Council Certified Encryption Specialist (ECES)212-82
EC-Council Certified Cybersecurity Technician (C|CT)212-89
EC-Council Certified Incident Handler (ECIH)312-38
EC-Council Certified Network Defender (CND)312-39
EC-Council Certified SOC Analyst (CSA)312-40
EC-Council Certified Cloud Security Engineer (CCSE)312-49
ECCouncil Computer Hacking Forensic Investigator (V9)312-49V10
EC-Council Certified Computer Hacking Forensic Investigator (V10)
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only EC-COUNCIL exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your 312-50V9 exam preparations and EC-COUNCIL certification application, do not hesitate to visit our Vcedump.com to find your solutions here.