Exam Details
Exam Code
:312-50V9Exam Name
:EC-Council Certified Ethical Hacker (C|EH v9)Certification
:EC-COUNCIL CertificationsVendor
:EC-COUNCILTotal Questions
:614 Q&AsLast Updated
:Apr 14, 2025
EC-COUNCIL EC-COUNCIL Certifications 312-50V9 Questions & Answers
-
Question 211:
Which of the following techniques will identify if computer files have been changed?
A. Network sniffing
B. Permission sets
C. Integrity checking hashes
D. Firewall alerts
-
Question 212:
A company has publicly hosted web applications and an internal Intranet protected by a firewall. Which technique will help protect against enumeration?
A. Reject all invalid email received via SMTP.
B. Allow full DNS zone transfers.
C. Remove A records for internal hosts.
D. Enable null session pipes.
-
Question 213:
Which of the following is a component of a risk assessment?
A. Physical security
B. Administrative safeguards
C. DMZ
D. Logical interface
-
Question 214:
When utilizing technical assessment methods to assess the security posture of a network, which of the following techniques would be most effective in determining whether end-user security training would be beneficial?
A. Vulnerability scanning
B. Social engineering
C. Application security testing
D. Network sniffing
-
Question 215:
Which of the following is a detective control?
A. Smart card authentication
B. Security policy
C. Audit trail
D. Continuity of operations plan
-
Question 216:
A penetration tester is hired to do a risk assessment of a company's DMZ. The rules of engagement states that the penetration test be done from an external IP address with no prior knowledge of the internal IT systems. What kind of test is being performed?
A. white box
B. grey box
C. red box
D. black box
-
Question 217:
Which of the following lists are valid data-gathering activities associated with a risk assessment?
A. Threat identification, vulnerability identification, control analysis
B. Threat identification, response identification, mitigation identification
C. Attack profile, defense profile, loss profile
D. System profile, vulnerability identification, security determination
-
Question 218:
What type of OS fingerprinting technique sends specially crafted packets to the remote OS and analyzes the received response?
A. Passive
B. Reflective
C. Active
D. Distributive
-
Question 219:
A penetration tester is conducting a port scan on a specific host. The tester found several ports opened that were confusing in concluding the Operating System (OS) version installed. Considering the NMAP result below, which of the following is likely to be installed on the target machine by the OS?
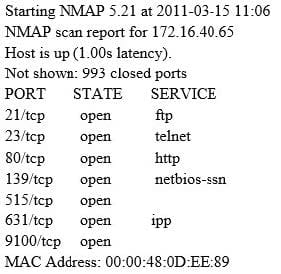
A. The host is likely a Windows machine.
B. The host is likely a Linux machine.
C. The host is likely a router.
D. The host is likely a printer.
-
Question 220:
An NMAP scan of a server shows port 25 is open. What risk could this pose?
A. Open printer sharing
B. Web portal data leak
C. Clear text authentication
D. Active mail relay
Related Exams:
112-51
EC-Council Certified Network Defense Essentials (NDE)212-77
EC-Council Certified Linux Security212-81
EC-Council Certified Encryption Specialist (ECES)212-82
EC-Council Certified Cybersecurity Technician (C|CT)212-89
EC-Council Certified Incident Handler (ECIH)312-38
EC-Council Certified Network Defender (CND)312-39
EC-Council Certified SOC Analyst (CSA)312-40
EC-Council Certified Cloud Security Engineer (CCSE)312-49
ECCouncil Computer Hacking Forensic Investigator (V9)312-49V10
EC-Council Certified Computer Hacking Forensic Investigator (V10)
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only EC-COUNCIL exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your 312-50V9 exam preparations and EC-COUNCIL certification application, do not hesitate to visit our Vcedump.com to find your solutions here.