Exam Details
Exam Code
:312-50V9Exam Name
:EC-Council Certified Ethical Hacker (C|EH v9)Certification
:EC-COUNCIL CertificationsVendor
:EC-COUNCILTotal Questions
:614 Q&AsLast Updated
:Apr 14, 2025
EC-COUNCIL EC-COUNCIL Certifications 312-50V9 Questions & Answers
-
Question 291:
Cryptography is the practice and study of techniques for secure communication in the presence of third parties (called adversaries.) More generally, it is about constructing and analyzing protocols that overcome the influence of adversaries and that are related to various aspects in information security such as data confidentiality, data integrity, authentication, and non-repudiation. Modern cryptography intersects the disciplines of mathematics, computer science, and electrical engineering. Applications of cryptography include ATM cards, computer passwords, and electronic commerce.
Basic example to understand how cryptography works is given below:

Which of the following choices is true about cryptography?
A. Algorithm is not the secret, key is the secret.
B. Symmetric-key algorithms are a class of algorithms for cryptography that use the different cryptographic keys for both encryption of plaintext and decryption of ciphertext.
C. Secure Sockets Layer (SSL) use the asymmetric encryption both (public/private key pair) to deliver the shared session key and to achieve a communication way.
D. Public-key cryptography, also known as asymmetric cryptography, public key is for decrypt, private key is for encrypt.
-
Question 292:
In both pharming and phishing attacks an attacker can create websites that look similar to legitimate sites with the intent of collecting personal identifiable information from its victims. What is the difference between pharming and phishing attacks?
A. In a pharming attack a victim is redirected to a fake website by modifying their host configuration file or by exploiting vulnerabilities in DNS. In a phishing attack an attacker provides the victim with a URL that is either misspelled or looks similar to the actual websites domain name.
B. Both pharming and phishing attacks are purely technical and are not considered forms of social engineering.
C. Both pharming and phishing attacks are identical.
D. In a phishing attack a victim is redirected to a fake website by modifying their host configuration file or by exploiting vulnerabilities in DNS. In a pharming attack an attacker provides the victim with a URL that is either misspelled or looks very similar to the actual websites domain name.
-
Question 293:
A well-intentioned researcher discovers a vulnerability on the web site of a major corporation. What should he do?
A. Ignore it.
B. Try to sell the information to a well-paying party on the dark web.
C. Notify the web site owner so that corrective action be taken as soon as possible to patch the vulnerability.
D. Exploit the vulnerability without harming the web site owner so that attention be drawn to the problem.
-
Question 294:
An IT employee got a call from one of our best customers. The caller wanted to know about the company's network infrastructure, systems, and team. New opportunities of integration are in sight for both company and customer. What should this employee do?
A. Since the company's policy is all about Customer Service, he/she will provide information.
B. Disregarding the call, the employee should hang up.
C. The employee should not provide any information without previous management authorization.
D. The employees can not provide any information; but, anyway, he/she will provide the name of the person in charge.
-
Question 295:
Sid is a judge for a programming contest. Before the code reaches him it goes through a restricted OS and is tested there. If it passes, then it moves onto Sid. What is this middle step called?
A. Fuzzy-testing the code
B. Third party running the code
C. Sandboxing the code
D. String validating the code
-
Question 296:
_________ is a set of extensions to DNS that provide to DNS clients (resolvers) origin authentication of DNS data to reduce the threat of DNS poisoning, spoofing, and similar attacks types.
A. DNSSEC
B. Zone transfer
C. Resource transfer
D. Resource records
-
Question 297:
An attacker tries to do banner grabbing on a remote web server and executes the following command.
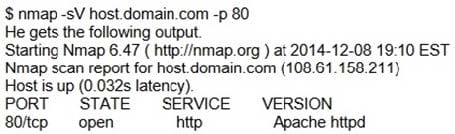
Service detection performed. Please report any incorrect results at http://nmap.org/submit/. Nmap done: 1 IP address (1 host up) scanned in 6.42 seconds
What did the hacker accomplish?
A. nmap can't retrieve the version number of any running remote service.
B. The hacker successfully completed the banner grabbing.
C. The hacker should've used nmap -O host.domain.com.
D. The hacker failed to do banner grabbing as he didn't get the version of the Apache web server.
-
Question 298:
Which tier in the N-tier application architecture is responsible for moving and processing data between the tiers?
A. Application Layer
B. Data tier
C. Presentation tier
D. Logic tier
-
Question 299:
Seth is starting a penetration test from inside the network. He hasn't been given any information about the network. What type of test is he conducting?
A. Internal Whitebox
B. External, Whitebox
C. Internal, Blackbox
D. External, Blackbox
-
Question 300:
What is the way to decide how a packet will move from an untrusted outside host to a protected inside that is behind a firewall, which permits the hacker to determine which ports are open and if the packets can pass through the packet- filtering of the firewall.
A. Firewalking
B. Session hijacking
C. Network sniffing
D. Man-in-the-middle attack
Related Exams:
112-51
EC-Council Certified Network Defense Essentials (NDE)212-77
EC-Council Certified Linux Security212-81
EC-Council Certified Encryption Specialist (ECES)212-82
EC-Council Certified Cybersecurity Technician (C|CT)212-89
EC-Council Certified Incident Handler (ECIH)312-38
EC-Council Certified Network Defender (CND)312-39
EC-Council Certified SOC Analyst (CSA)312-40
EC-Council Certified Cloud Security Engineer (CCSE)312-49
ECCouncil Computer Hacking Forensic Investigator (V9)312-49V10
EC-Council Certified Computer Hacking Forensic Investigator (V10)
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only EC-COUNCIL exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your 312-50V9 exam preparations and EC-COUNCIL certification application, do not hesitate to visit our Vcedump.com to find your solutions here.