Exam Details
Exam Code
:312-50V9Exam Name
:EC-Council Certified Ethical Hacker (C|EH v9)Certification
:EC-COUNCIL CertificationsVendor
:EC-COUNCILTotal Questions
:614 Q&AsLast Updated
:Apr 14, 2025
EC-COUNCIL EC-COUNCIL Certifications 312-50V9 Questions & Answers
-
Question 451:
Within the context of Computer Security, which of the following statements describes Social Engineering best?
A. Social Engineering is the act of publicly disclosing information
B. Social Engineering is the means put in place by human resource to perform time accounting
C. Social Engineering is the act of getting needed information from a person rather than breaking into a system
D. Social Engineering is a training program within sociology studies
-
Question 452:
You are programming a buffer overflow exploit and you want to create a NOP sled of 200 bytes in the program exploit.c
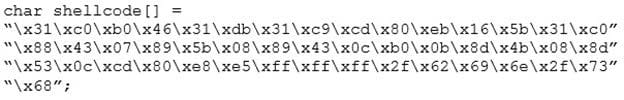
What is the hexadecimal value of NOP instruction?
A. 0x60
B. 0x80
C. 0x70
D. 0x90
-
Question 453:
This TCP flag instructs the sending system to transmit all buffered data immediately.
A. SYN
B. RST
C. PSH
D. URG
E. FIN
-
Question 454:
The network administrator at Spears Technology, Inc has configured the default gateway Cisco router's
access-list as below:
You are hired to conduct security testing on their network.
You successfully brute-force the SNMP community string using a SNMP crack tool.
The access-list configured at the router prevents you from establishing a successful connection.
You want to retrieve the Cisco configuration from the router. How would you proceed?
A. Use the Cisco's TFTP default password to connect and download the configuration file
B. Run a network sniffer and capture the returned traffic with the configuration file from the router
C. Run Generic Routing Encapsulation (GRE) tunneling protocol from your computer to the router masking your IP address
D. Send a customized SNMP set request with a spoofed source IP address in the range -192.168.1.0
-
Question 455:

Identify the correct terminology that defines the above statement.
A. Vulnerability Scanning
B. Penetration Testing
C. Security Policy Implementation
D. Designing Network Security
-
Question 456:
Nathan is testing some of his network devices. Nathan is using Macof to try and flood the ARP cache of
these switches.
If these switches' ARP cache is successfully flooded, what will be the result?
A. The switches will drop into hub mode if the ARP cache is successfully flooded.
B. If the ARP cache is flooded, the switches will drop into pix mode making it less susceptible to attacks.
C. Depending on the switch manufacturer, the device will either delete every entry in its ARP cache or reroute packets to the nearest switch.
D. The switches will route all traffic to the broadcast address created collisions.
-
Question 457:
ViruXine.W32 virus hides their presence by changing the underlying executable code.
This Virus code mutates while keeping the original algorithm intact, the code changes itself each time it
runs, but the function of the code (its semantics) will not change at all.
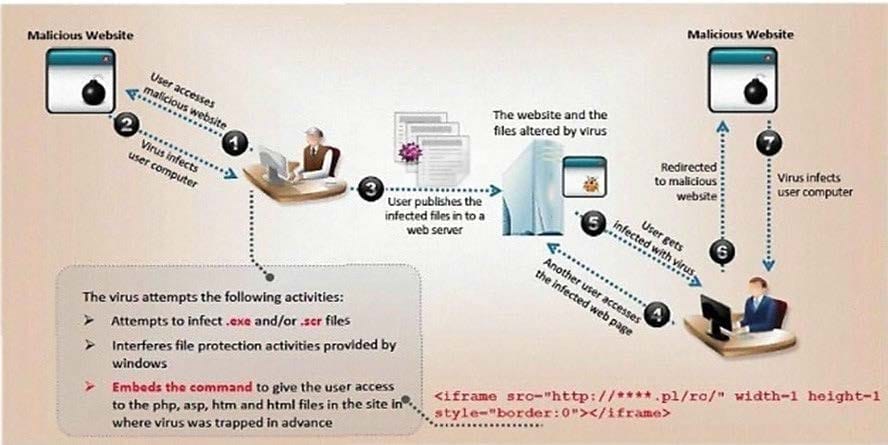
Here is a section of the Virus code:
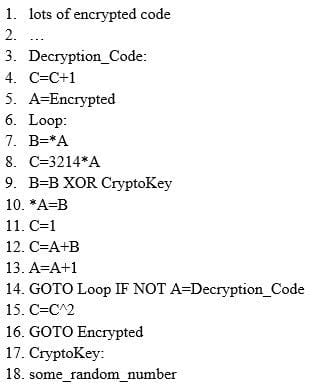
What is this technique called?
A. Polymorphic Virus B. Metamorphic Virus
C. Dravidic Virus
D. Stealth Virus
-
Question 458:
Bob is going to perform an active session hijack against Brownies Inc. He has found a target that allows session oriented connections (Telnet) and performs the sequence prediction on the target operating system. He manages to find an active session due to the high level of traffic on the network. What is Bob supposed to do next?
A. Take over the session
B. Reverse sequence prediction
C. Guess the sequence numbers
D. Take one of the parties offline
-
Question 459:
What hacking attack is challenge/response authentication used to prevent?
A. Replay attacks
B. Scanning attacks
C. Session hijacking attacks
D. Password cracking attacks
-
Question 460:
In this attack, a victim receives an e-mail claiming from PayPal stating that their account has been disabled and confirmation is required before activation. The attackers then scam to collect not one but two credit card numbers, ATM PIN number and other personal details. Ignorant users usually fall prey to this scam. Which of the following statement is incorrect related to this attack?
A. Do not reply to email messages or popup ads asking for personal or financial information
B. Do not trust telephone numbers in e-mails or popup ads
C. Review credit card and bank account statements regularly
D. Antivirus, anti-spyware, and firewall software can very easily detect these type of attacks
E. Do not send credit card numbers, and personal or financial information via e-mail
Related Exams:
112-51
EC-Council Certified Network Defense Essentials (NDE)212-77
EC-Council Certified Linux Security212-81
EC-Council Certified Encryption Specialist (ECES)212-82
EC-Council Certified Cybersecurity Technician (C|CT)212-89
EC-Council Certified Incident Handler (ECIH)312-38
EC-Council Certified Network Defender (CND)312-39
EC-Council Certified SOC Analyst (CSA)312-40
EC-Council Certified Cloud Security Engineer (CCSE)312-49
ECCouncil Computer Hacking Forensic Investigator (V9)312-49V10
EC-Council Certified Computer Hacking Forensic Investigator (V10)
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only EC-COUNCIL exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your 312-50V9 exam preparations and EC-COUNCIL certification application, do not hesitate to visit our Vcedump.com to find your solutions here.