Exam Details
Exam Code
:350-401Exam Name
:Implementing and Operating Cisco Enterprise Network Core Technologies (ENCOR)Certification
:CCNP EnterpriseVendor
:CiscoTotal Questions
:1407 Q&AsLast Updated
:Apr 13, 2025
Cisco CCNP Enterprise 350-401 Questions & Answers
-
Question 311:
Refer to the exhibit.
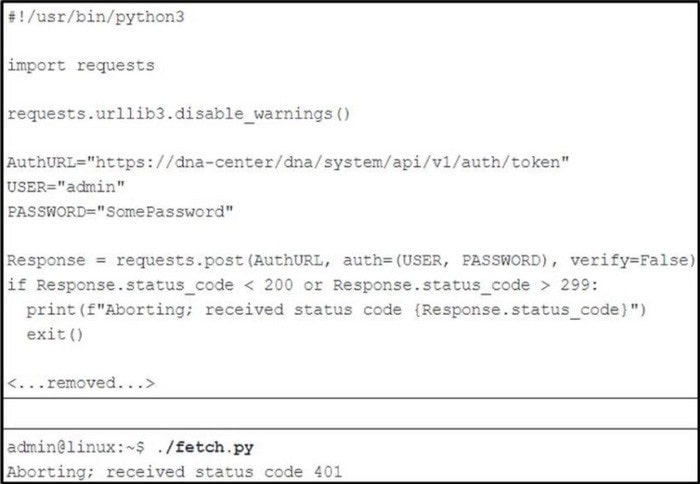
An administrator writes a script to fetch the list of devices that are registered with Cisco DNA Center. Why does the execution abort?
A. The TLS certificate of DNA Center is invalid
B. The username or the password is incorrect
C. The "dna-center" hostname cannot be resolved to an IP address
D. The authentication URL is incorrect
-
Question 312:
Refer to the exhibit.

An administrator must collect basic statistics about the approximate amount of IPv4 and IPv6 flows entering Gi0/0 using NetFlow. However, the administrator is concerned that NetFlow processing during periods of high utilization on Gi0/0 will overwhelm the router CPU.
Which configuration minimizes CPU impact and keeps the data flows across Gi0/0 intact?
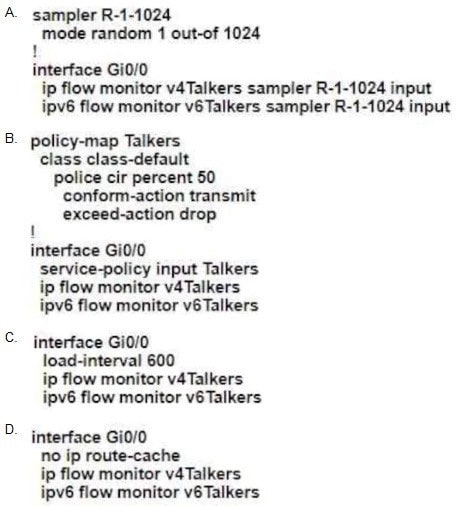
A. Option A
B. Option B
C. Option C
D. Option D
-
Question 313:
Refer to the exhibit.
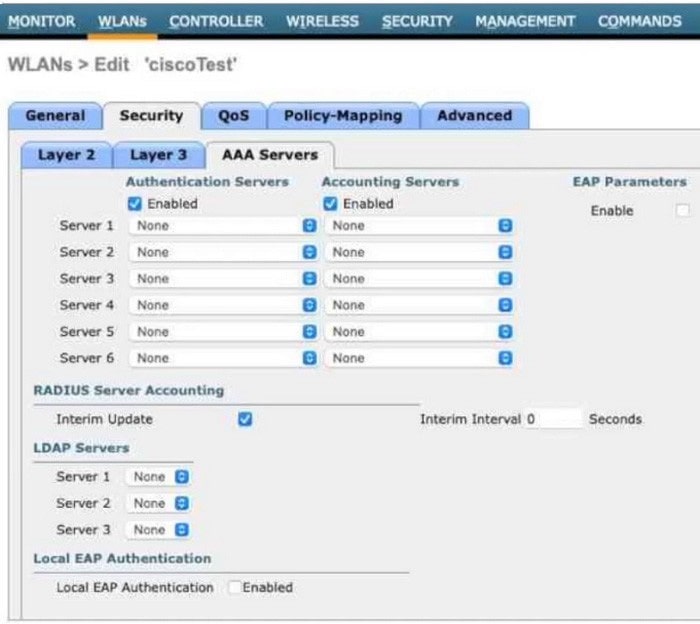
An engineer must configure a Cisco WLC with WPA2 Enterprise mode and avoid global server lists. Which action is required?
A. Enable EAP parameters
B. Apply CISCO ISE default settings
C. Select a RADIUS authentication server
D. Disable the RADIUS server accounting interim update
-
Question 314:
Refer to the exhibit.
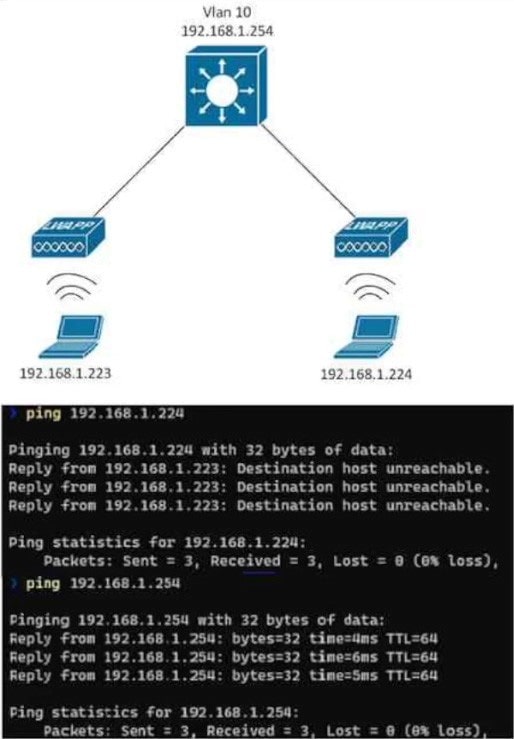
An SSID is configured and both clients can reach their gateways on the Layer 3 switch, but they cannot communicate with each other. Which action resolves this issue?
A. Set the WMM Policy to Allowed
B. Set the P2P Blocking Action to Disabled
C. Set the WMM Policy to Required
D. Set the P2P Blocking Action to Forward-UpStream
-
Question 315:
Where are operations related to software images located in the Cisco DNA Center GUI?
A. Services
B. Provisioning
C. Assurance
D. Design
-
Question 316:
Which JSON script is properly formatted?
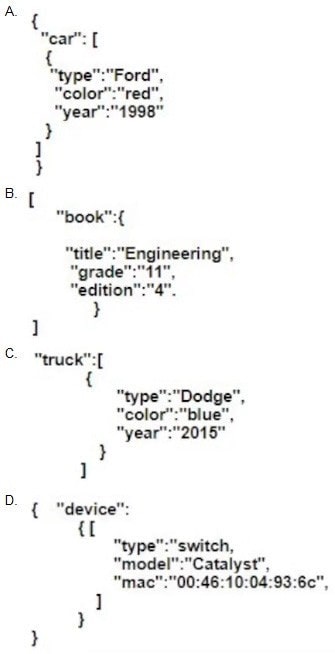
A. Option A
B. Option B
C. Option C
D. Option D
-
Question 317:
Refer to the exhibit.

What does the Python code accomplish?
A. It configures interface e1/32 to be in an admin down state
B. It generates a status code of 403 because the type is incorrect.
C. It configures interface e1/32 to be in an err-disable state.
D. It returns data in JSON-RPC format.
-
Question 318:
Refer to the exhibit.

Which action must be performed to allow RESTCONF access to the device?
A. Enable the NETCONF service.
B. Enable the SSH service.
C. Enable the IOX service.
D. Enable the HTTPS service.
-
Question 319:
Which two security mechanisms are used by Cisco Threat Defense to gain visibility into the most dangerous cyber threats? (Choose two.)
A. virtual private networks
B. file reputation
C. VLAN segmentation
D. Traffic Telemetry
E. dynamic enforce policy
-
Question 320:
Which action is a LISP ITR responsible for?
A. responding to map-request messages
B. forwarding user data traffic
C. finding EID-to-RLOC mappings
D. accepting registration requests from ETRs
Related Exams:
300-410
Implementing Cisco Enterprise Advanced Routing and Services (ENARSI)300-415
Implementing Cisco SD-WAN Solutions (ENSDWI)300-420
Designing Cisco Enterprise Networks (ENSLD)300-425
Designing Cisco Enterprise Wireless Networks (ENWLSD)300-430
Implementing Cisco Enterprise Wireless Networks (ENWLSI)300-435
Automating and Programming Cisco Enterprise Solutions (ENAUTO)300-440
Designing and Implementing Cloud Connectivity (ENCC)350-401
Implementing and Operating Cisco Enterprise Network Core Technologies (ENCOR)
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only Cisco exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your 350-401 exam preparations and Cisco certification application, do not hesitate to visit our Vcedump.com to find your solutions here.