Exam Details
Exam Code
:350-401Exam Name
:Implementing and Operating Cisco Enterprise Network Core Technologies (ENCOR)Certification
:CCNP EnterpriseVendor
:CiscoTotal Questions
:1407 Q&AsLast Updated
:Apr 13, 2025
Cisco CCNP Enterprise 350-401 Questions & Answers
-
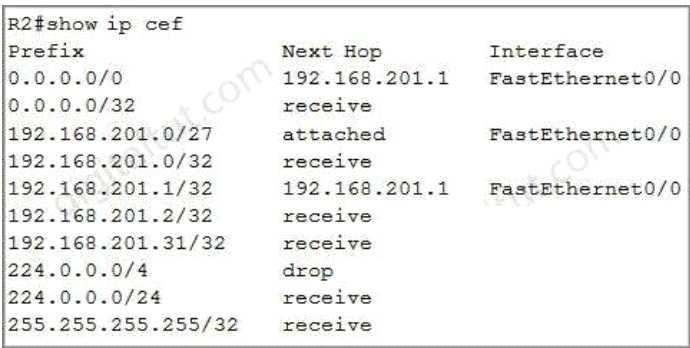
Question 401:
Which statement about Cisco Express Forwarding is true?
A. It uses a fast cache that is maintained in a router data plane.
B. It maintains two tables in the data plane: the FIB and adjacency table.
C. It makes forwarding decisions by a process that is scheduled through the IOS scheduler.
D. The CPU of a router becomes directly involved with packet-switching decisions.
-
Question 402:
Which access controls list allows only TCP traffic with a destination port range of 22-433, excluding port 80?
A. deny tcp any any eq 80 permit tcp any any gt 21 lt 444
B. permit tcp any any range 22 443 deny tcp any any eq 80
C. permit tcp any any eq 80
D. deny tcp any any eq 80 permit tcp any any range 22 443
-
Question 403:
Which statement about VXLAN is true?
A. VXLAN uses TCP 35 the transport protocol over the physical data cento network.
B. VXLAN extends the Layer 2 Segment ID field to 24-bits. which allows up to 4094 unique Layer 2 segments over the same network.
C. VXLAN encapsulates a Layer 2 frame in an IP-UDP header, which allows Layer 2 adjacency across router boundaries.
D. VXLAN uses the Spanning Tree Protocol for loop prevention.
-
Question 404:
What is the correct EBGP path attribute list, ordered from most preferred to the least preferred, that the BGP best-path algorithm uses?
A. weight. AS path, local preference. MED
B. weight, local preference AS path, MED
C. local preference weight AS path, MED
D. local preference, weight MED, AS path
-
Question 405:
Refer to the exhibit.
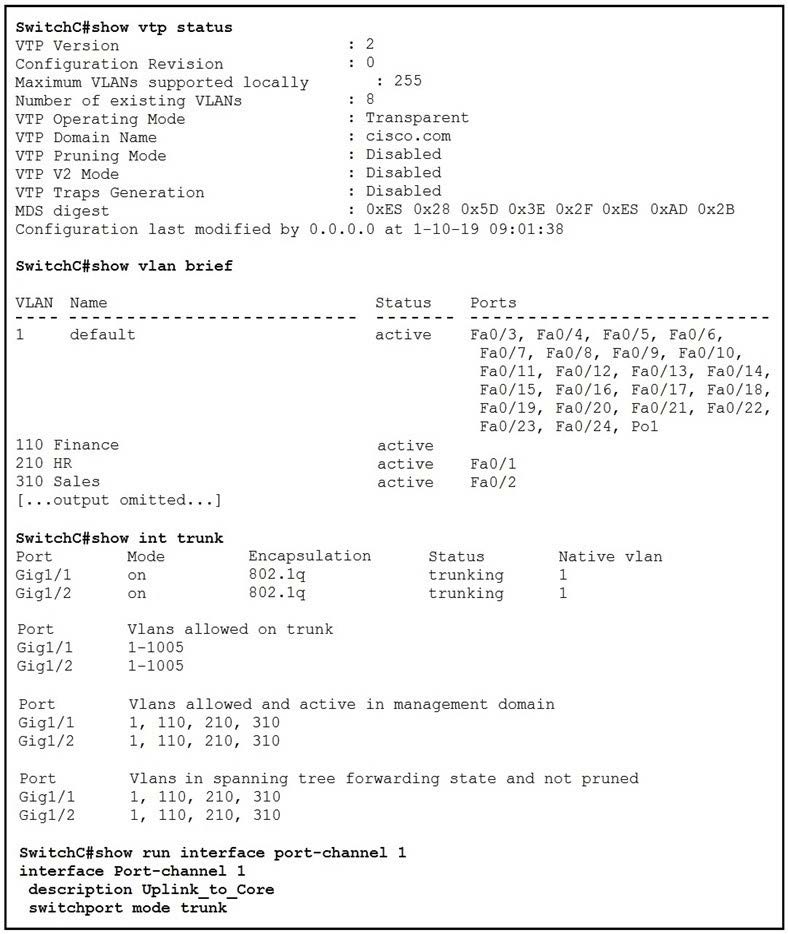
SwitchC connects HR and Sales to the Core switch. However, business needs require that no traffic from the Finance VLAN traverse this switch.
Which command meets this requirement?
A. SwitchC(config)#vtp pruning vlan 110
B. SwitchC(config)#vtp pruning
C. SwitchC(config)#interface port-channel 1 SwitchC(config-if)#switchport trunk allowed vlan add 210,310
D. SwitchC(config)#interface port-channel 1 SwitchC(config-if)#switchport trunk allowed vlan remove 110
-
Question 406:
Which QoS component alters a packet to change the way that traffic is treated in the network?
A. Marking
B. Classification
C. Shaping
D. Policing
-
Question 407:
If a VRRP master router fails, which router is selected as the new master router?
A. router with the highest priority
B. router with the highest loopback address
C. router with the lowest loopback address
D. router with the lowest priority
-
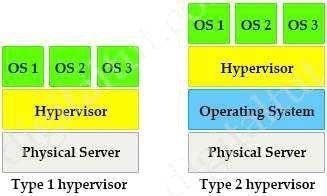
Question 408:
Which statement explains why Type 1 hypervisor is considered more efficient than Type 2 hypervisor?
A. Type 1 hypervisor runs directly on the physical hardware of the host machine without relying on the underlying OS.
B. Type 1 hypervisor enables other operating systems to run on it.
C. Type 1 hypervisor relics on the existing OS of the host machine to access CPU, memory, storage, and network resources.
D. Type 1 hypervisor is the only type of hypervisor that supports hardware acceleration techniques.
-
Question 409:
To increase total throughput and redundancy on the links between the wireless controller and switch, the customer enabled LAG on the wireless controller. Which EtherChannel mode must be configured on the switch to allow the WLC to connect?
A. Auto
B. Active
C. On
D. Passive
-
Question 410:
On which protocol or technology is the fabric data plane based in Cisco SD-Access fabric?
A. LISP
B. IS-IS
C. Cisco TrustSec
D. VXLAN
Related Exams:
300-410
Implementing Cisco Enterprise Advanced Routing and Services (ENARSI)300-415
Implementing Cisco SD-WAN Solutions (ENSDWI)300-420
Designing Cisco Enterprise Networks (ENSLD)300-425
Designing Cisco Enterprise Wireless Networks (ENWLSD)300-430
Implementing Cisco Enterprise Wireless Networks (ENWLSI)300-435
Automating and Programming Cisco Enterprise Solutions (ENAUTO)300-440
Designing and Implementing Cloud Connectivity (ENCC)350-401
Implementing and Operating Cisco Enterprise Network Core Technologies (ENCOR)
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only Cisco exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your 350-401 exam preparations and Cisco certification application, do not hesitate to visit our Vcedump.com to find your solutions here.