Exam Details
Exam Code
:350-401Exam Name
:Implementing and Operating Cisco Enterprise Network Core Technologies (ENCOR)Certification
:CCNP EnterpriseVendor
:CiscoTotal Questions
:1407 Q&AsLast Updated
:Apr 13, 2025
Cisco CCNP Enterprise 350-401 Questions & Answers
-
Question 501:
Which method ensures the confidentiality of data exchanged over a REST API?
A. Use the POST method instead of URL-encoded GET to pass parameters.
B. Encode sensitive data using Base64 encoding.
C. Deploy digest-based authentication to protect the access to the API.
D. Use TLS to secure the underlying HTTP session.
-
Question 502:
Users have reported an issue connecting to a server over the network. A workstation was recently added to the network and configured with a shared USB printer. Which of the following is most likely causing the issue?
A. The switch is oversubscribed and cannot handle the additional throughput.
B. The printer is tying up the server with DHCP discover messages.
C. The web server's back end was designed for only single-threaded applications.
D. The workstation was configured with a static IP that is the same as the server.
-
Question 503:
What is a characteristic of the Cisco DMA Center Template Editor feature?
A. It facilitates software upgrades lo network devices from a central point.
B. It facilitates a vulnerability assessment of the network devices.
C. It provides a high-level overview of the health of every network device.
D. It uses a predefined configuration through parameterized elements or variables.
-
Question 504:
Refer to the exhibit.
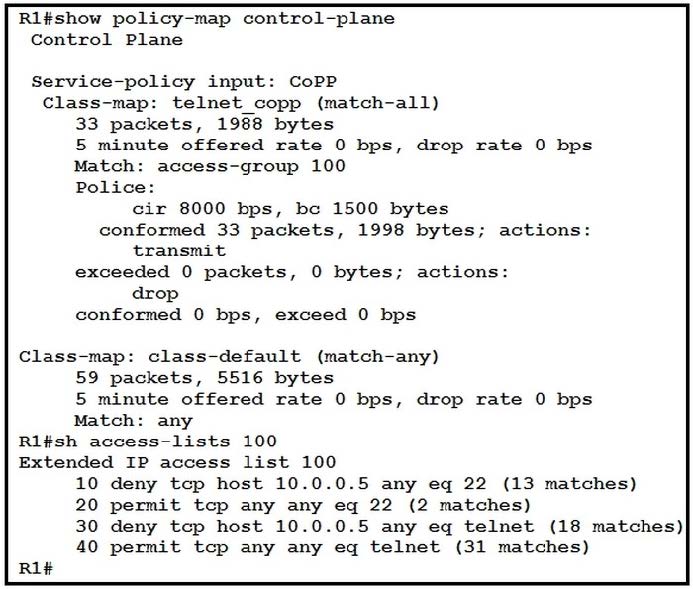
Which result Is achieved by the CoPP configuration?
A. Traffic that matches entry 10 of ACL 100 is always allowed.
B. Class-default traffic is dropped.
C. Traffic that matches entry 10 of ACL 100 is always allowed with a limited CIR.
D. Traffic that matches entry 10 of ACL 100 is always dropped.
-
Question 505:
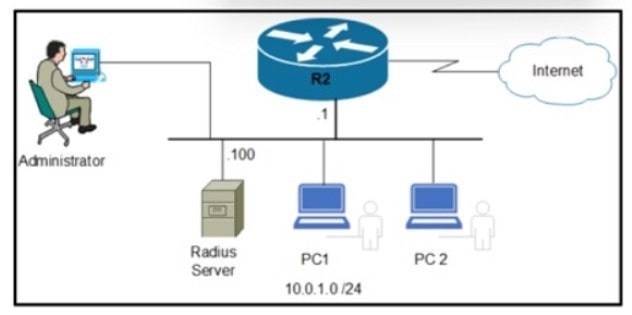
Refer to the exhibit. An engineer must save the configuration of router R2 using the NETCONF protocol. Which script must be used?

A. Option A
B. Option B
C. Option C
D. Option D
-
Question 506:
Which configuration enables a device to be configured via NETCONF over SSHv2?
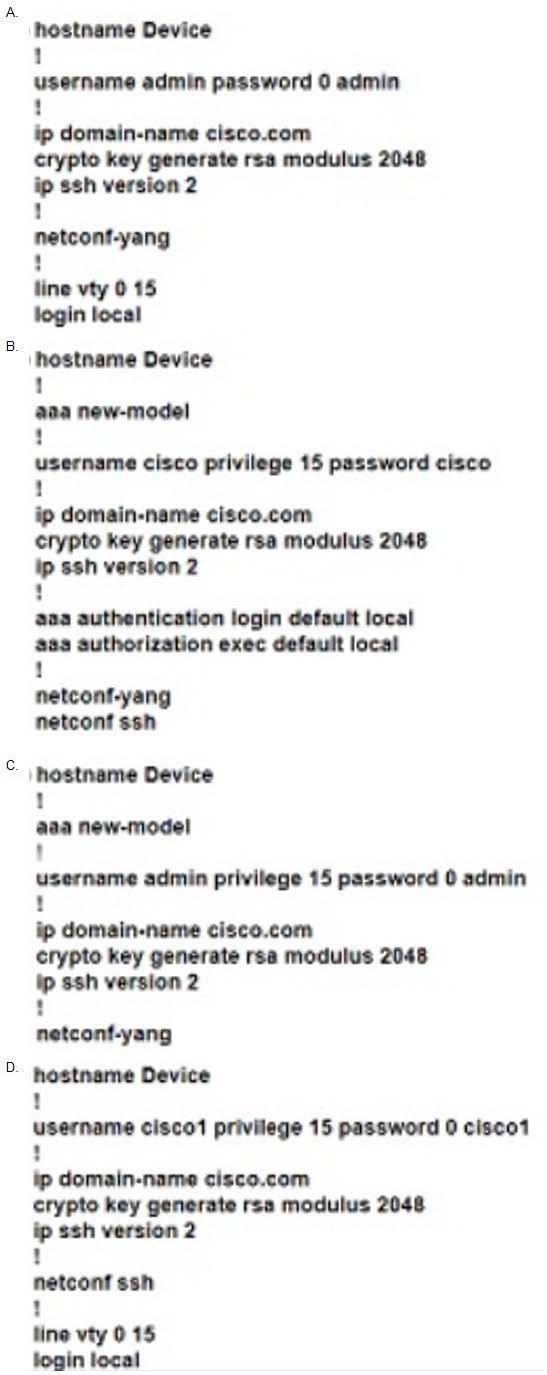
A. Option A
B. Option B
C. Option C
D. Option D
-
Question 507:
A company's office has publicly accessible meeting rooms equipped with network ports. A recent audit revealed that visitors were able to access the corporate network by plugging personal laptops into open network ports. Which of the following should the company implement to prevent this in the future?
A. URL filters
B. VPN
C. ACLs
D. NAC
-
Question 508:
What is a benefit of YANG modules?
A. tightly coupled models with encoding to improve performance
B. easier multivendor interoperability provided by common or industry models
C. avoidance of ecosystem fragmentation by having fixed that cannot be changed D. single protocol and model couple to simplify maintenance and supported
-
Question 509:
Refer to the exhibit.
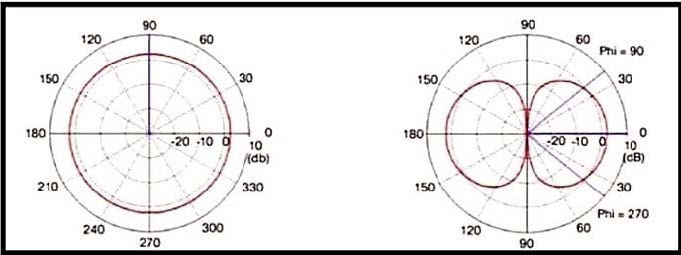
Which type of antenna is show on the radiation patterns?
A. Dipole
B. Yagi
C. Patch
D. Omnidirectional
-
Question 510:
Which of the following should a junior security administrator recommend implementing to mitigate malicious network activity?
A. Intrusion prevention system
B. Load balancer
C. Access logging
D. Endpoint encryption
Related Exams:
300-410
Implementing Cisco Enterprise Advanced Routing and Services (ENARSI)300-415
Implementing Cisco SD-WAN Solutions (ENSDWI)300-420
Designing Cisco Enterprise Networks (ENSLD)300-425
Designing Cisco Enterprise Wireless Networks (ENWLSD)300-430
Implementing Cisco Enterprise Wireless Networks (ENWLSI)300-435
Automating and Programming Cisco Enterprise Solutions (ENAUTO)300-440
Designing and Implementing Cloud Connectivity (ENCC)350-401
Implementing and Operating Cisco Enterprise Network Core Technologies (ENCOR)
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only Cisco exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your 350-401 exam preparations and Cisco certification application, do not hesitate to visit our Vcedump.com to find your solutions here.