Exam Details
Exam Code
:350-401Exam Name
:Implementing and Operating Cisco Enterprise Network Core Technologies (ENCOR)Certification
:CCNP EnterpriseVendor
:CiscoTotal Questions
:1407 Q&AsLast Updated
:Apr 13, 2025
Cisco CCNP Enterprise 350-401 Questions & Answers
-
Question 621:
Refer to the exhibit.

Which command set completes the ERSPAN session configuration?

A. Option A
B. Option B
C. Option C
D. Option D
-
Question 622:
Which authorization framework gives third-party applications limited access to HTTP services?
A. iPsec
B. Basic Auth
C. GRE
D. OAuth 2.0
-
Question 623:
An engineer receives a report that an application exhibits poor performance. On the switch where the server is connected, this syslog message is visible: SW_MATM-4-MACFLAP_NOTIF: Host 0054.3962.7651 in vlan 14 is flapping between port Gi1/0/1 and port Gi1/0/2.
What is causing the problem?
A. undesirable load-balancing configuration on the switch
B. invalid port channel configuration on the switch
C. wrong SFP+ and cable connected between the server and the switch
D. failed NIC on the server
-
Question 624:
Which technology is used to provide Layer 2 and Layer 3 logical networks in the Cisco SD-Access architecture?
A. underlay network
B. VPN routing/forwarding
C. easy virtual network
D. overlay network
-
Question 625:

What is a benefit of using segmentation with TrustSec?
A. Integrity checks prevent data from being modified in transit.
B. Packets sent between endpoints on a LAN are encrypted using symmetric key cryptography.
C. Security group tags enable network segmentation.
D. Firewall rules are streamlined by using business-level profiles.
-
Question 626:
A network engineer wants to configure console access to a router without using AAA so that the privileged exec mode is entered directly after a user provides the correct login credentials. Which action achieves this goal?
A. Configure login authentication privileged on line con 0.
B. Configure a local username with privilege level 15.
C. Configure privilege level 15 on line con 0.
D. Configure a RADIUS or TACACS+ server and use it to send the privilege level.
-
Question 627:
What is one method for achieving REST API security?
A. using a combination of XML encryption and XML signatures
B. using HTTPS and TLS encryption
C. using a MDS hash to verify the integrity
D. using built-in protocols known as Web Services Security
-
Question 628:
Which solution simplifies management of secure access to network resources?
A. RFC 3580-based solution to enable authenticated access leveraging RADIUS and AV pairs
B. 802.1AE to secure communication in the network domain
C. ISE to automate network access control leveraging RADIUS AV pairs
D. TrustSec to logically group internal user environments and assign policies
-
Question 629:
Refer to the exhibit Which two commands are required on route?R1 to block FTP and allow all other traffic from the Branch 2 network? (Choose two)

A. access-list 101 deny tcp 10.0.2.0 0.0.0.255 host 10.0.101.3 eq ftp access-list 101 deny tcp 10.0.2.0 0.0.0.255 host 10.0.101.3 eq ftp-data access-list 101 permit ip any any
B. access-list 101 deny tcp 10.0.2.0 0.0.0.255 host 10.0.101.3 eq ftp-data access-list 101 permit ip any any
C. interface GigabitEthernet0/0 ip address 10.0.0.1 255.255.255.252 ip access-group 101 out
D. access-list 101 deny tcp 10.0.2.0 0.0.0.255 host 10.0.101.3 eq ftp access-list 101 permit ip any any
E. interface GigabitEthernet0/0 ip address 10.0.101.1 255.255.255.252 ip access-group 101 in
-
Question 630:
Refer to the exhibit.
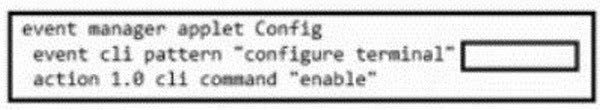
An engineer constructs an EEM applet to prevent anyone from entering configuration mode on a switch. Which snippet is required to complete the EEM applet?
A. sync yes skip yes
B. sync no skip yes
C. sync no skip no
D. sync yes skip no
Related Exams:
300-410
Implementing Cisco Enterprise Advanced Routing and Services (ENARSI)300-415
Implementing Cisco SD-WAN Solutions (ENSDWI)300-420
Designing Cisco Enterprise Networks (ENSLD)300-425
Designing Cisco Enterprise Wireless Networks (ENWLSD)300-430
Implementing Cisco Enterprise Wireless Networks (ENWLSI)300-435
Automating and Programming Cisco Enterprise Solutions (ENAUTO)300-440
Designing and Implementing Cloud Connectivity (ENCC)350-401
Implementing and Operating Cisco Enterprise Network Core Technologies (ENCOR)
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only Cisco exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your 350-401 exam preparations and Cisco certification application, do not hesitate to visit our Vcedump.com to find your solutions here.