Exam Details
Exam Code
:350-501Exam Name
:Implementing and Operating Cisco Service Provider Network Core Technologies (SPCOR)Certification
:CCNP Service ProviderVendor
:CiscoTotal Questions
:509 Q&AsLast Updated
:Mar 25, 2025
Cisco CCNP Service Provider 350-501 Questions & Answers
-
Question 1:
DRAG DROP
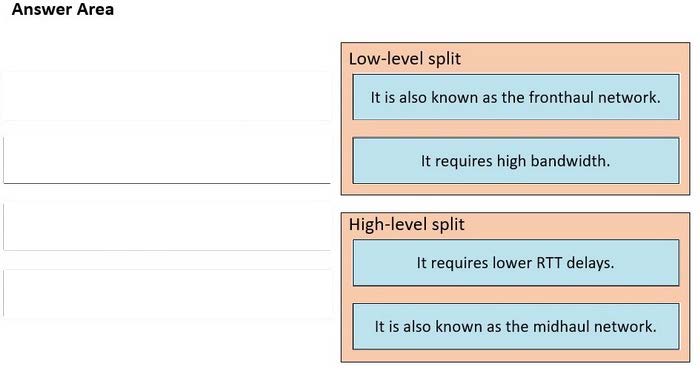
Drag and drop the characteristics from the left onto the corresponding radio splitting approaches on the right.
Select and Place:

-
Question 2:
Which set of facts must the network architect consider when deciding whether to implement SaltStack or Chef?
A. Chef is an agent-based tool based on Ruby and SaltStack is a module tool based on Python
B. Chef refers to its automation instructions as manifests and SaltStack refers to its instructions as a playbook
C. Chef uses a message-based system and SaltStack uses an agent to deliver messages.
D. Chef is written in Python and SaltStack is written in Ruby.
-
Question 3:
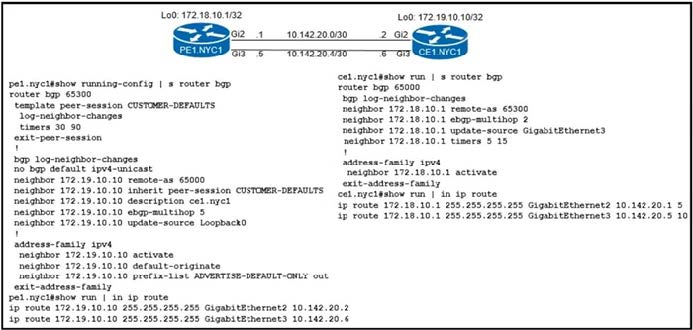
Refer to the exhibit. An engineer started to configure a router for BGP. Which configuration must the network engineer apply to router CE1.NYC1 so that it establishes an eBGP multihop session with PE1.NYC1?
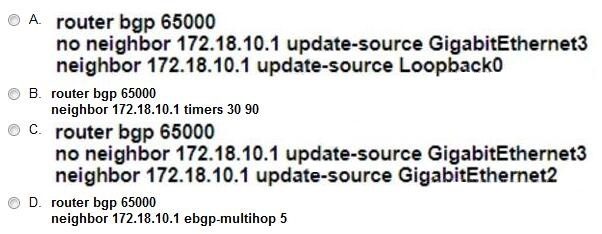
A. Option A
B. Option B
C. Option C
D. Option D
-
Question 4:
What is a feature of mVPN?
A. It requires unicast to be disabled on the multicast domain
B. It provides the ability to support multicast over a Layer 3 VPN
C. It establishes multiple static MDTs for each multicast domain
D. It requires the no ip mroute-cache command to be configured on the loopback interface of each BGP peer
-
Question 5:
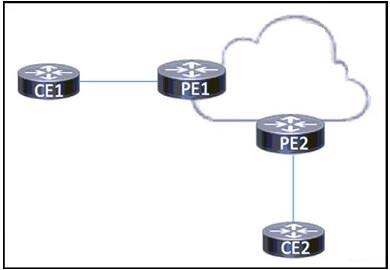
Refer to the exhibit. BGP is running in the core of the service provider to exchange routes for its customers, and OSPF serves as the PE-CE routing protocol. The service provider's existing customer at CE1 is opening a new office in a different geographical location connected via CE2. A network engineer must update the BGP implementation so that PE1 and PE2 will share routes and provide communication between CE1 and CE2. Which action must the engineer take?
A. Configure PE1 and PE2 to mutually redistribute BGP and OSPF in the VRF for the customer
B. Configure CE1 and CE2 with a pseudowire that will run over the service provider core
C. Configure PE1 and PE2 to redistribute OSPF from the VRF for the customer into BGP
D. Configure CE1 and CE2 to establish a BGP relationship with PE1 and PE2
-
Question 6:
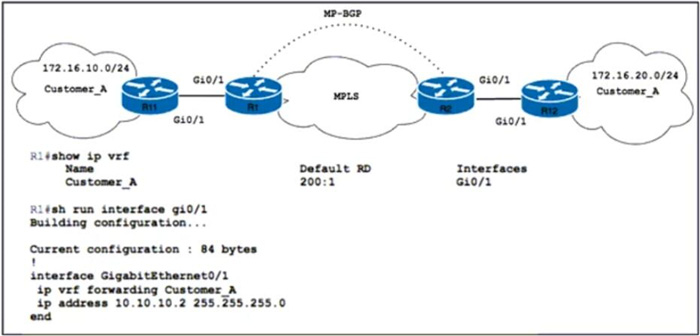
Refer to the exhibit. Customer_A asked ISP_A to connect two offices via an MPLS L3 VPN. Customer_A is currently using only the default route toward ISP_A. The engineer at ISP_A already configured the ip route vrf Customer_A
172.16.10.0 255.255.255.0 10.10.10.1 command on R1. Which action completes the configuration?
A. Configure the redistribute static and redistribute connected commands on R1.
B. Enable the bgp default route-target filter and default-information originate commands under the global BGP configuration on R2.
C. Configure the route-target both 200:1 and route-replicate vrf Customer_A commands under the ip vrf configuration on R2.
D. Configure the network 172.16.10.0 and redistribute-internal static commands under the BGP address family for Customer_A in the global BGP configuration on R1.
-
Question 7:
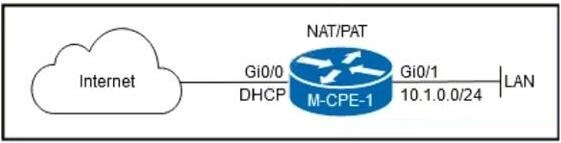
Refer to the exhibit. An engineer working for a service provider with an employee ID: 1234:56:789 notices that malicious traffic with a source IP in the RFC1918 range is arriving on the WAN connection to the internet and impacting customer resources on the LAN. Which ACL configuration must the engineer implement on M-CPE-1 to block the malicious traffic?
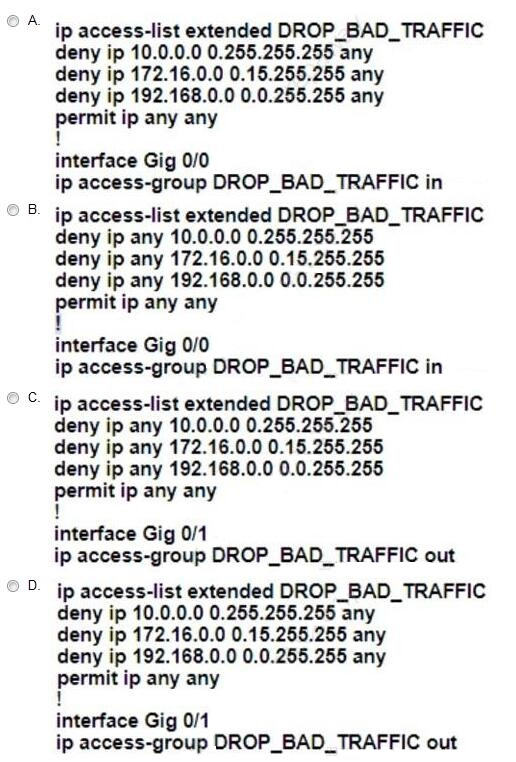
A. Option A
B. Option B
C. Option C
D. Option D
-
Question 8:
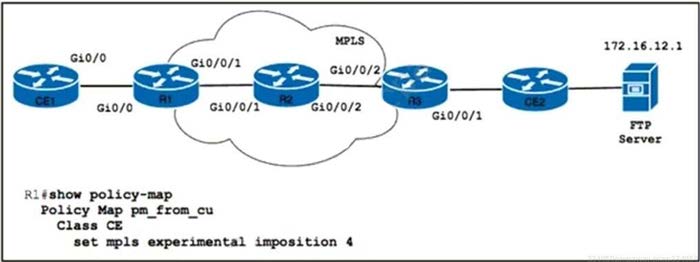
Refer to the exhibit Router R1 is configured with class map CE with match ip precedence critical to align with customer contract SLAs. The customer is sending all traffic from CE1 toward the FTP server with IP precedence 5. A network engineer must allow 10% of interface capacity on router R3. Which two actions must the engineer take to accomplish the task? (Choose two.)
A. Implement a class map on R3 to match all packets with QoS IP precedence value 011.
B. Implement a class map on R1 to match all packets with QoS IP precedence value 100.
C. Apply a policy map to R3 to reserve 10% of interface bandwidth.
D. Apply a policy map to R1 to reserve the remaining 10% of interface bandwidth.
E. Implement a class map on R3 to match all packets with QoS IP precedence value 101.
-
Question 9:
Which action occurs during the traceback phase of the six-phase approach to service provider security?
A. Trace the attack that flows from the attacked sections of the network toward the network edges
B. Detect unusual activity or behavior and activate appropriate measures after an alert is raised
C. Review the whole attack-handling process
D. Mitigate the attack that flows using various mechanisms
-
Question 10:
A network engineer must collect traffic statistics for an internal LAN toward the internet. The sample must include the source and destination IP addresses the destination ports, the total number of bytes from each flow using a 64-bit counter and all transport flag information. Because of CPU limits, the flow collector processes samples that are a maximum of 20 seconds long. Which two configurations must the network engineer apply to the router? (Choose two.)
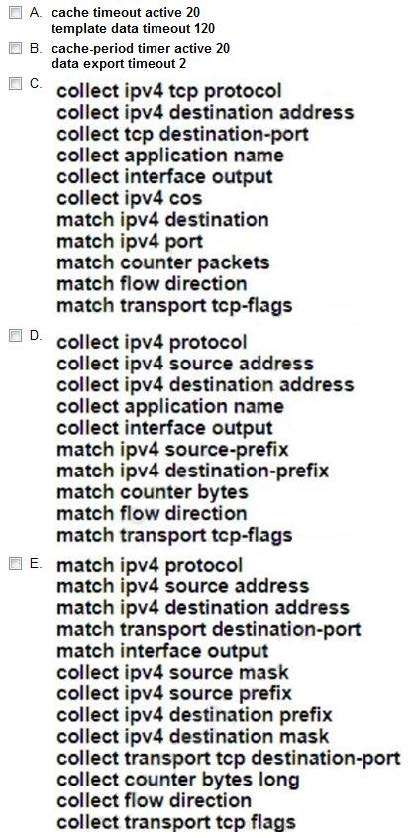
A. Option A
B. Option B
C. Option C
D. Option D
E. Option E
Related Exams:
300-510
Implementing Cisco Service Provider Advanced Routing Solutions (SPRI)300-515
Implementing Cisco Service Provider VPN Services (SVPI)300-535
Automating and Programming Cisco Service Provider Solutions (SPAUTO)350-501
Implementing and Operating Cisco Service Provider Network Core Technologies (SPCOR)
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only Cisco exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your 350-501 exam preparations and Cisco certification application, do not hesitate to visit our Vcedump.com to find your solutions here.