Exam Details
Exam Code
:350-901Exam Name
:Developing Applications Using Cisco Core Platforms and APIs (DEVCOR)Certification
:Cisco Certified DevNet ProfessionalVendor
:CiscoTotal Questions
:414 Q&AsLast Updated
:Mar 29, 2025
Cisco Cisco Certified DevNet Professional 350-901 Questions & Answers
-
Question 11:
DRAG DROP
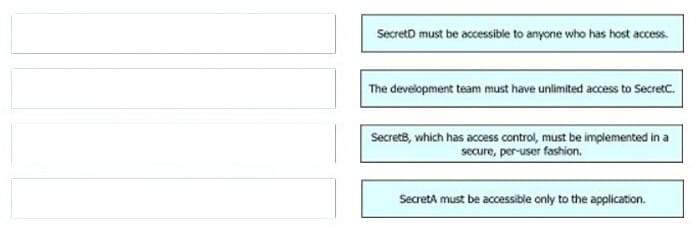
A developer is designing an application that uses confidential information for a company and its clients. The developer must implement different secret storage techniques for each handled secret to enforce security policy compliance within a project. Drag and drop the security policy requirements from the left onto the storage solutions on the right.
Select and Place:
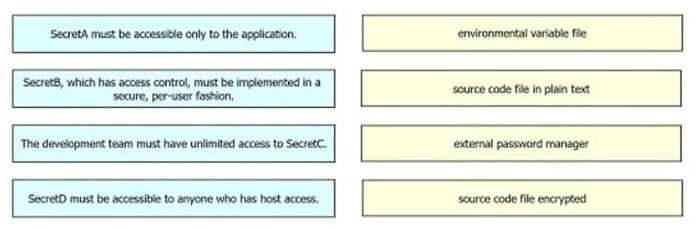
-
Question 12:
DRAG DROP
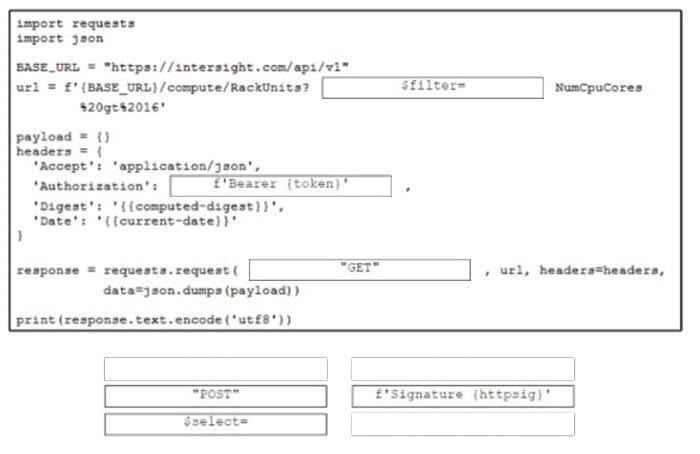
Drag and drop the code from the bottom onto the box whore the code is missing to retrieve a list of rack units that have more than 16 CPU cores. The filtered list will be used to create a summary on the monitoring dashboard. Not all options are used.
Select and Place:
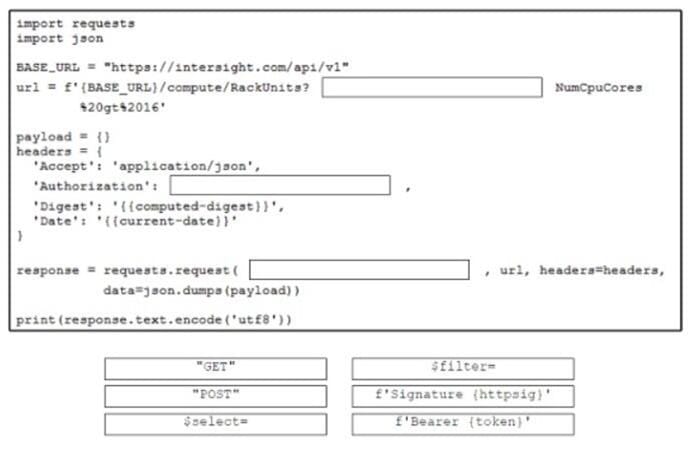
-
Question 13:
DRAG DROP
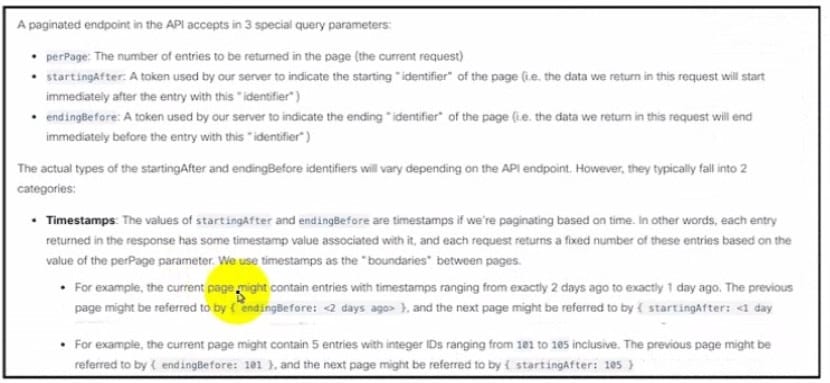
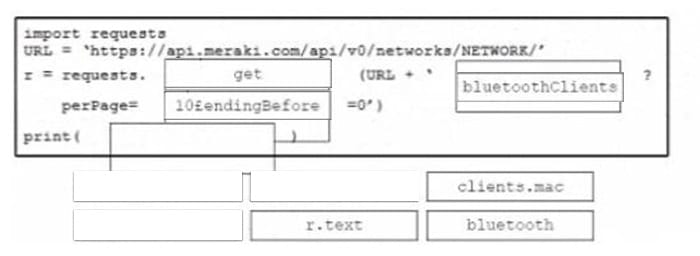
Refer to the exhibit Drag and drop the code from the bottom onto the box where the code is missing to query the last 10 Bluetooth clients seen by APs in their network using the Meraki Dashboard API Not all options are used.
Select and Place:
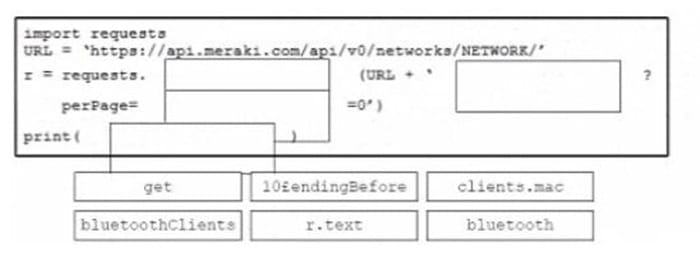
-
Question 14:
What is a benefit of running multiple instances of a back-end service and using load balancing to distribute the communication between the front-end and back-end services?
A. The consistency of data for stateful services increases.
B. High availability is provided for the back-end services.
C. Scaling horizontally is automated out of the box.
D. The total load on the database servers decreases.
-
Question 15:
How is an OAulh2 three-legged authentication flow initiated?
A. The user makes a roquost to the OAuth client
B. Exchange the key f
C. Construct an API call to retrieve the credentials.
D. Get the authorization code.
-
Question 16:
The code fetches the latest order from the purchases table for a specific user. An engineer needs to pass query parameters to the execute function to prevent an SQL injection attack. Which code snippet must be placed in the blank in the code to meet this requirement?
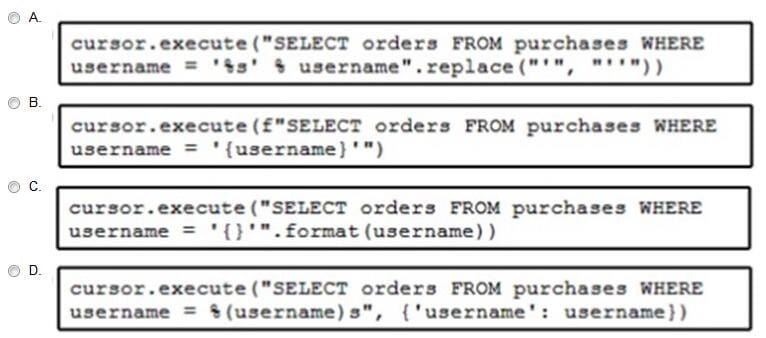
A. Option A
B. Option B
C. Option C
D. Option D
-
Question 17:
An engineer needs to configure an interface named GigabitEthernet3 with an IP address on several RESTCONF-enabled Cisco IOS XE devices. Which code snippet must be placed in the blank in the code to meet this requirement?
A. (item["name"])'
B. (item["name"])/ip/addres3
C. item["name"]:/ip/address/primary'
D. (ltemt"name"]} /ip
-
Question 18:
How does the use of release packaging allow dependencies to be effectively managed during deployments?
A. dependencies are staggered between multiple releases
B. designed to prevent any dependencies between release units
C. dependencies are tested after the release is deployed
D. removal of release units if they have issues in testing
-
Question 19:
Which data encoding format uses gRPC by default for serializing structured sets of information?
A. JSON
B. YAML
C. Protobuf
D. XML
-
Question 20:
Refer to the exhibits. Which data payload completes the CURL command to run the create port object API call In Cisco Firepower Threat Defense?
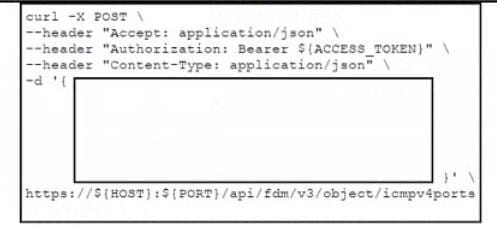
Which data payload completes the CURL command to run the create port object API call In Cisco Firepower Threat Defense?

A. Option A
B. Option B
C. Option C
D. Option D
Related Exams:
300-435
Automating and Programming Cisco Enterprise Solutions (ENAUTO)300-535
Automating and Programming Cisco Service Provider Solutions (SPAUTO)300-635
Automating and Programming Cisco Data Center Solutions (DCAUTO)300-735
Automating and Programming Cisco Security Solutions (SAUTO)300-835
Automating Cisco Collaboration Solutions (CLAUTO)300-910
Implementing DevOps Solutions and Practices using Cisco Platforms (DEVOPS)350-901
Developing Applications Using Cisco Core Platforms and APIs (DEVCOR)
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only Cisco exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your 350-901 exam preparations and Cisco certification application, do not hesitate to visit our Vcedump.com to find your solutions here.