Exam Details
Exam Code
:352-011Exam Name
:Cisco Certified Design Expert PracticalCertification
:Cisco CertificationsVendor
:CiscoTotal Questions
:249 Q&AsLast Updated
:May 06, 2025
Cisco Cisco Certifications 352-011 Questions & Answers
-
Question 1:
A network engineering team is in the process of designing a lab network for a customer demonstration. The design engineer wants to show that the resiliency of the MPLS traffic Engineering Fast Reroute solution has the same failover/ failback times as a traditional SONET/SDH network (around 50MSEC). In order to address both link failure and node failure within the lab typology network, which type of the MPLS TE tunnels must be considered for this demonstration?
A. TE backup tunnel
B. Next-hop (NHop) tunnel
C. FRR Backup tunnel
D. next-next-hop (NNHop) tunnel
-
Question 2:
After a large EIGRP network had automatic summarization enabled throughout, it started experiencing routing loops. Which action should you take to quickly resolve the routing loops yet to perform summarization?
A. Redistribute connected routes at major IP networks boundaries
B. Redesign the IP addressing scheme
C. Increase the AD of the automatically summarized routes D. Replace the automatic summarization with more specific summary routes
-
Question 3:
As part of network design, two geographically separated data centers must be interconnected using Ethernet-over-MPLS pseudowire. The link between the sites is stable, the topology has no apparent loops, and the root bridges for the respective VLANs are stable and unchanging. Which aspect must be the part of the design to mitigate the risk of connectivity issues between the data centers?
A. Enable Spanning Tree on one data center, and Rapid Reconfiguration of Spanning tree on the other
B. Ensure that the spanning tree diameter for one or more VLANs is not too large.
C. Enable UDLD on the link between the data centers.
D. Enable root guard on the link between the data centers.
-
Question 4:
Why is a redundant PIM stub router topology a bad network design decision?
A. Multicast convergence takes long
B. Multicast traffic duplication will occur
C. It interferes with IGMP snooping
D. It interfaces with PIM snooping
-
Question 5:
Which option lists the cloud service models?
A. Internet as a Service, Platform as a Service, and Storage as a Service.
B. Infrastructure as a Service, Platform as a Service, and Storage as a Service.
C. Infrastructure as a Service, Platform as a Service, and Software as a Service.
D. Internet as a Service, Product as a Service, and Storage as a Service.
E. Internet as a Service, Platform as a Service, and Software as a Service.
-
Question 6:
Refer to the Exhibit.
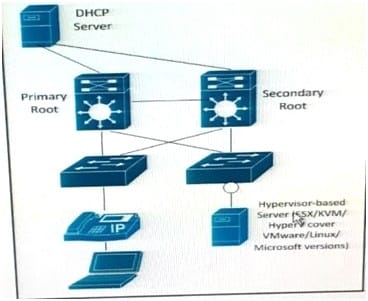
The server is running multiple VLANs on its NIC. Which two Layer 2 features should be applied to the network location identified by a circle? (Choose two)
A. UDLD
B. BPDU guard
C. BPDU filtering
D. Port Fast
E. Loop guard
F. PortFast trunk
-
Question 7:
You are designing an IPv4 any source multicast redundancy solution. Which technology ensures the quickest RP convergence?
A. Bootstrap router
B. MSDP anycast RP
C. Auto-RP
D. Embedded RP
-
Question 8:
A Company has these requirements for access to their wireless and wired corporate LANs using 802.1x
Clients devices that corporate assets and have joined the active directory domain are allowed access
Personal devices must be not allowed access
Clients and access servers must be mutually authenticated.
Which solution meets these requirements?
A. Protected EAP/Microsoft CHAP v2 with user authentication
B. EAP-TLS with machine authentication
C. EAP-TLS with user authentication
D. Protected EAP/Microsoft CHAP v2 with Machine authentication
-
Question 9:
Which two are IoT sensor-specific constraints? (Choose two)
A. Memory
B. Processing power
C. The amount of devices
D. Cooling
E. Standard transport protocols
-
Question 10:
You are working on a network design plan for a company with approximately 2000 sites. The sites will be connected using the public Internet. You plan to use private IP addressing in the network design, which will be routed without NAT through an encrypted WAN network. Some sites will be connected to the Internet with dynamic public IP addresses, and these addresses may change occasionally. Which VPN solution will support these design requirements?
A. GET VPN must be used, because DMVPN does not scale to 2000 sites.
B. DMVPN must be used, because GET VPN does not scale to 2000 sites.
C. GET VPN must be used, because private IP addresses cannot be transferred with DMVPN through the public Internet.
D. DMVPN must be used, because private IP addresses cannot be transferred with GET VPN through the public Internet.
E. GET VPN must be used, because DMVPN does not support dynamic IP addresses for some sites.
F. DMVPN must be used, because GET VPN does not support dynamic IP addresses for some sites.
Related Exams:
300-915
Developing Solutions using Cisco IoT and Edge Platforms (DEVIOT)300-920
Developing Applications for Cisco Webex and Webex Devices (DEVWBX)352-011
Cisco Certified Design Expert Practical500-052
Cisco Unified Contact Center Express500-173
Designing the FlexPod Solution (FPDESIGN)500-174
Implementing and Administering the FlexPod Solution (FPIMPADM)500-201
Deploying Cisco Service Provider Mobile Backhaul Solutions500-210
SP Optical Technology Field Engineer Representative500-220
Cisco Meraki Solutions Specialist500-230
Cisco Service Provider Routing Field Engineer
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only Cisco exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your 352-011 exam preparations and Cisco certification application, do not hesitate to visit our Vcedump.com to find your solutions here.