Exam Details
Exam Code
:400-007Exam Name
:Cisco Certified Design Expert (CCDE Written)Certification
:CCDEVendor
:CiscoTotal Questions
:397 Q&AsLast Updated
:Apr 18, 2025
Cisco CCDE 400-007 Questions & Answers
-
Question 211:
What are two common approaches to analyzing and designing networks? (Choose two.)
A. bottom-up approach
B. high-low security approach
C. top-down approach
D. left-right approach
E. three-tier approach
-
Question 212:
A network attacker exploits application flaws to compromise critical systems in the organization with these objectives:
1.
Obtain sensitive data and export the data out of the network.
2.
Compromise developer and administrator credentials to potentially
What is the next step after application discovery is completed in Zero Trust networkings
A. Establish visibility and behavior modeling
B. Enforce policies and microsegmentation.
C. Assess real-time security health.
D. Ensure trustworthiness of systems.
-
Question 213:
Refer to the exhibit.

For Company XYZ Bangkok is using ECMP to reach the 172 20 2 0/24 network The company wants a design that would allow them to forward traffic from 172 16 2 0/24 toward 172 20 2 0/24 via the Singapore router as the preferred route The rest of the traffic should continue to use ECMP.
Which technology fulfills this design requirement?
A. policy-based routing
B. route summarization
C. unequal-cost load balancing using variance
D. LFA
-
Question 214:
Which function is performed at the access layer of the three-layer hierarchical network design model?
A. fault isolation
B. QoS classification and marking boundary
C. reliability
D. fast transport
E. redundancy and load balancing
-
Question 215:
A business invests in SDN and develops its own SDN controller that, due to budget constraints, runs on a single controller. The controller actively places an exclusive lock on the configuration of the devices to ensure it is the only source of changes to the environment. What is the result if the controller fails?
A. All device configurations are in read-only mode until the controller is restored.
B. The control plane is unavailable until the controller is restored.
C. If a device fails, the configuration backup is unavailable
D. Manual changes are only possible until the controller is restored
-
Question 216:
Refer to the table.
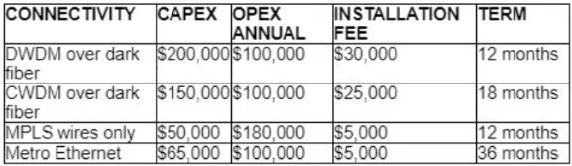
A customer investigates connectivity options for a DCI between two production data centers to aid a large-scale migration project. The migration is estimated to take 20 months to complete but might extend an additional 10 months if issues arise. All connectivity options meet the requirements to migrate workloads. Which transport technology provides the best ROI based on cost and flexibility?
A. CWDM over dark fiber
B. MPLS
C. DWDM over dark fiber
D. Metro Ethernet
-
Question 217:
Which two application requirements are mandatory for traffic to receive proper treatment when placed in the priority queue? (Choose two.)
A. small transactions (HTTP-like behavior)
B. WRED drop treatment
C. tolerance to packet loss
D. intolerance to jitter
E. TCP-based application
-
Question 218:
Company XYZ wants to secure the data plane of their network. Which two technologies can be included in the security design? (Choose two)
A. DAI
B. IP Source Guard
C. BEEP
D. CPPr
E. MPP
-
Question 219:
Refer to the table.
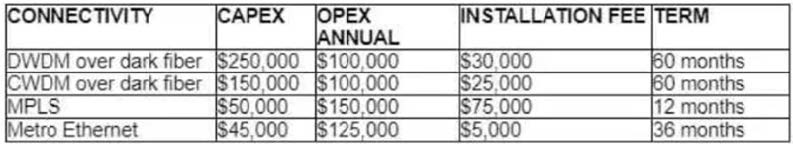
A customer investigates connectivity options for a DCI between two production data centers. The solution must provide dual 10G connections between locations with no single points of failure for Day 1 operations. It must also include an option to scale for up to 20 resilient connections in the second year to accommodate isolated SAN over IP and isolated, dedicated replication IP circuits. All connectivity methods are duplex 10 Gbps. Which transport technology costs the least over two years, in the scenario?
A. Metro Ethernet
B. DWDM
C. CWDM
D. MPLS
-
Question 220:
An architect designs a multi-controller network architecture with these requirements:
1.
Achieve fast failover to control traffic when controllers fail.
2.
Yield a short distance and high resiliency in the connection between the switches and the controller.
3.
Reduce connectivity loss and enable smart recovery to improve the SDN survivability.
4.
Improve connectivity by adding path diversity and capacity awareness for controllers.
Which control plane component of the multi-controller must be built to meet the requirements?
A. control node reliability
B. controller stale consistency
C. control path reliability
D. controller clustering
Related Exams:
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only Cisco exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your 400-007 exam preparations and Cisco certification application, do not hesitate to visit our Vcedump.com to find your solutions here.