Exam Details
Exam Code
:5V0-91.20Exam Name
:VMware Carbon Black Portfolio SkillsCertification
:VMware CertificationsVendor
:VMwareTotal Questions
:116 Q&AsLast Updated
:Mar 27, 2025
VMware VMware Certifications 5V0-91.20 Questions & Answers
-
Question 91:
An incorrectly constructed watchlist generates 10,000 incorrect alerts.
How should an administrator resolve this issue?
A. Delete the watchlist to automatically clear the alerts, and then create a new watchlist with the correct criteria.
B. From the Triage Alerts Page, use the facets to select the watchlist, click the Wrench button to "Mark all as Resolved False Positive", and then update the watchlist with the correct criteria.
C. Update the Triage Alerts Page to show 200 alerts, click the Select All Checkbox, click the "Dismiss Alert(s)" button for each page, and then update the watchlist with the correct criteria.
D. From the Watchlists Page, select the offending watchlist, click "Clear Alerts" from the Action menu, and then update the watchlist with the correct criteria.
-
Question 92:
Review the following query:
path:c:\program\ files\ \(x86\)\microsoft
How would this query input term be interpreted?
A. c:\program files x86\microsoft
B. c:rogram files (x86)icrosoft
C. c:rogramfilesx86icrosoft
D. c:\program files (x86)\microsoft
-
Question 93:
Which action is only available for the "Performs any operation" and "Performs any API Operation" operation attempts?
A. Bypass
B. Allow and Log
C. Runs or is Running
D. Allow
-
Question 94:
Carbon Black App Control maintains an inventory of all interesting (executable) files on endpoints where the agent is installed.
What is the initial inventory procedure called, and how can this process be triggered?
A. Inventorying; enable Discovery mode
B. Baselining; install the agent
C. Discovery; place agent into Disabled mode
D. Initialization; move agent out of Disabled mode
-
Question 95:
There is a requirement to block ransomware when a sensor is offline. Which blocking and isolation rule fulfills this requirement?
A. Known Malware --> Performs ransomware-like behavior --> Terminate process
B. Not Listed Application --> Performs ransomware-like behavior --> Deny operation
C. Suspect Malware --> Performs ransomware-like behavior --> Deny operation
D. Unknown Application --> Performs ransomware-like behavior --> Terminate process
-
Question 96:
How often do watchlists run?
A. Every 10 minutes
B. Every 5 minutes
C. Watchlists can be configured to run at scheduled intervals
D. Every 30 minutes
-
Question 97:
Which ID in Endpoint Standard is associated with one specific action, involves up to three different hashes (Parent, Process, Target), and occurs on a single device at a specific time?
A. Threat ID
B. Process ID
C. Alert ID
D. Event ID
-
Question 98:
Review this result after executing a query in the Process Search page, noting the circled black dot:
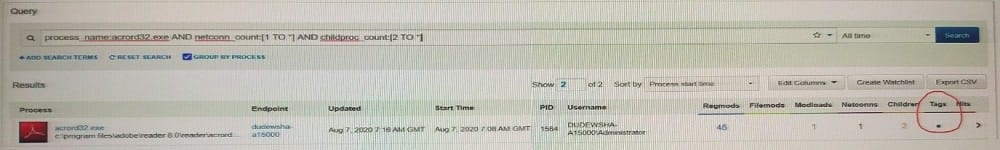
What is the meaning of the black dot shown under Tags?
A. The execution of the process resulted in watchlist hits.
B. The events for the process were tagged in an investigation.
C. The events for the process were also sent to the Syslog Server.
D. The execution of the process resulted in feed hits.
-
Question 99:
Which statement filters data to only return rows where the publisher of the software includes VMware anywhere in the name?
A. WHERE publisher = "%VMware%"
B. WHERE publisher = "%VMware"
C. WHERE publisher LIKE "VMware%"
D. WHERE publisher LIKE "%VMware%"
-
Question 100:
A company wants to implement the strictest security controls for computers on which the software seldom changes (i.e., servers or single-purpose systems).
Which Enforcement Level is the most fitting?
A. Low Enforcement
B. Medium Enforcement
C. High Enforcement
D. None (Visibility)
Related Exams:
1V0-21.20
Associate VMware Data Center Virtualization1V0-31.21
Associate VMware Cloud Management and Automation1V0-41.20
Associate VMware Network Virtualization1V0-61.21
Associate VMware Digital Workspace1V0-71.21
Associate VMware Application Modernization1V0-81.20
Associate VMware Security2V0-21.20
Professional VMware vSphere 7.x2V0-21.23
VMware vSphere 8.x Professional2V0-31.21
Professional VMware vRealize Automation 8.32V0-31.23
VMware Aria Automation 8.10 Professional
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only VMware exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your 5V0-91.20 exam preparations and VMware certification application, do not hesitate to visit our Vcedump.com to find your solutions here.