Exam Details
Exam Code
:5V0-91.20Exam Name
:VMware Carbon Black Portfolio SkillsCertification
:VMware CertificationsVendor
:VMwareTotal Questions
:116 Q&AsLast Updated
:Mar 27, 2025
VMware VMware Certifications 5V0-91.20 Questions & Answers
-
Question 31:
A security policy states to enable Live Response by default across the enterprise. However, the team identified critical systems which should not support Live Response due to risk. The team needs to disable Live Response on selected systems.
From which page can this goal be accomplished?
A. Policy
B. API Access
C. Endpoints
D. Roles
-
Question 32:
An Endpoint Standard administrator finds a binary in the environment and decides to manually add the file hash to the Banned List.
Which reputation does the file now have?
A. Suspect/Heuristic Malware
B. Company Black
C. Adware/PUP Malware
D. Known Malware
-
Question 33:
An Enterprise EDR administrator wants to use Watchlists curated by VMware Carbon Black and other
threat intelligence specialists.
How should the administrator add these curated Watchlists from the Watchlists page?
A. Click Add Watchlists, and input the URL(s) for the desired Watchlists.
B. Click Take Action, select Edit, and select the desired Watchlists.
C. Click Take Action, and select Subscribe for the desired Watchlists.
D. Click Add Watchlists, on the Subscribe tab select the desired Watchlists, and click Subscribe.
-
Question 34:
Which reputation has the highest priority in Cloud Endpoint Standard?
A. Unknown
B. Adware/PUP Malware
C. Known Malware
D. Ignore
-
Question 35:
An analyst has investigated two alerts on two separate HR workstations and found that notepad.exe has established communication to another IP address.
Which rule will kill notepad.exe entirely if this activity is detected in the future?
A. **\system32\notepad.exe --> Communicates over the network --> Terminate process
B. **\system32\notepad.exe --> Runs or is Running --> Deny operation
C. **/system32/notepad.exe --> Runs or is Running --> Terminate process
D. **/system32/notepad.exe--> Communicates over the network --> Deny operation
-
Question 36:
An Enterprise EDR administrator has created a custom Watchlist and wants to add a custom query to a report in the custom Watchlist.
From which page can the administrator add this custom query?
A. Policies
B. Watchlists
C. Investigate
D. Cloud Analysis
-
Question 37:
An analyst has investigated multiple alerts on a number of HR workstations and found that java.exe is
attempting to PowerShell. Of the Windows workstations in question, the analyst has also found that Java is
installed in multiple locations.
The analyst needs to block java.exe from this type of operation.
Which rule meets this need?
A. **/java.exe --> Invokes an untrusted process --> Terminate process
B. **/Program Files/*/java.exe--> Invokes an untrusted process --> Deny operation
C. **\Program Files\*\java.exe --> Invokes a command interpreter --> Terminate process
D. **\java.exe --> Invokes a command interpreter --> Deny operation
-
Question 38:
In which two ways can the tamper protection on an App Control agent be disabled when diagnosing agent issues or removing the agent? (Choose two.)
A. From the Computer Details page on the web console
B. From the Files on Computers page on the web console
C. Run authenticated DasCLI on Windows command prompt
D. Run RepCLI on Windows command prompt
E. From the File Catalog page on the web console
-
Question 39:
Refer to the exhibit, noting the circled red dot:
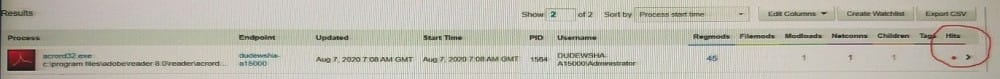
What is the meaning of the red dot under Hits in the Process Search page?
A. Whether the execution of the process resulted in a syslog hit
B. Whether the execution of the process resulted in a sensor hit
C. Whether the execution of the process resulted in matching hits for different users
D. Whether the execution of the process resulted in a feed hit
-
Question 40:
Which two statements are true regarding Live Response? (Choose two.)
A. Live Response can only be initiated through the user interface.
B. Live Response supports one user per session on an endpoint.
C. Live Response opens an SSH session with the remote device.
D. Live Response requires both view and manage permissions to use.
E. Live Response utilizes the same channel for sensor-server communications.
Related Exams:
1V0-21.20
Associate VMware Data Center Virtualization1V0-31.21
Associate VMware Cloud Management and Automation1V0-41.20
Associate VMware Network Virtualization1V0-61.21
Associate VMware Digital Workspace1V0-71.21
Associate VMware Application Modernization1V0-81.20
Associate VMware Security2V0-21.20
Professional VMware vSphere 7.x2V0-21.23
VMware vSphere 8.x Professional2V0-31.21
Professional VMware vRealize Automation 8.32V0-31.23
VMware Aria Automation 8.10 Professional
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only VMware exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your 5V0-91.20 exam preparations and VMware certification application, do not hesitate to visit our Vcedump.com to find your solutions here.