Exam Details
Exam Code
:5V0-91.20Exam Name
:VMware Carbon Black Portfolio SkillsCertification
:VMware CertificationsVendor
:VMwareTotal Questions
:116 Q&AsLast Updated
:Mar 27, 2025
VMware VMware Certifications 5V0-91.20 Questions & Answers
-
Question 51:
The security operations group is complaining that they are getting multiple App Control alerts for specific malicious files after they have banned the file.
Which step is necessary to prevent future alerts on these files?
A. Edit the Malicious File Detected Alert. Select the criteria: Ignore already banned files and Ignore already approved files.
B. Edit the Malicious File Detected Alert. Select the criteria: Ignore already banned files.
C. Disable the Reminder Mail.
D. Set the Alert Status to Disabled.
-
Question 52:
An administrator has updated a Threat Intelligence Report by turning it into a watchlist and needs to disable (Ignore) the old Threat Intelligence Report.
Where in the UI is this action not possible to perform?
A. Search Threat Reports Page
B. Threat Intelligence Feeds Page
C. Threat Report Page
D. Triage Alerts Page
-
Question 53:
While an administrator is reviewing an alert, the device is observed beaconing to an unknown destination. Which action should be taken to stop this behavior?
A. Deregister the sensor
B. Put the device in Bypass mode
C. Place the device in Quarantine
D. Assign the application to the Approved List
-
Question 54:
An analyst is investigating a specific alert in Endpoint Standard. The analyst selects the investigate button from the alert triage page and sees the following:
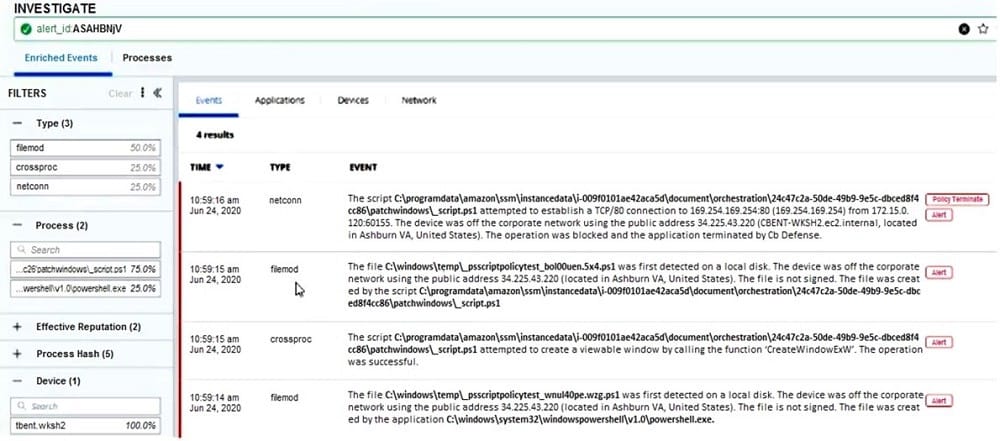
Which statement accurately characterizes this situation?
A. These events are tied to an observed alert within the user interface.
B. The policy had no blocking and isolation rules set.
C. The events shown will all have the same event ID, correlating them to the alert.
D. Each event listed contributed to the overall alert score and severity.
-
Question 55:
An analyst is investigating an alert within Enterprise EDR on the process analysis page. The process tree can be seen below:
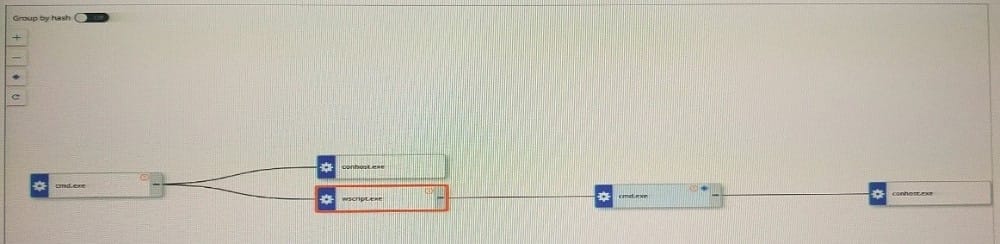
Which statement accurately characterizes this situation?
A. Conhost.exe has one or more child processes.
B. The solid line between the nodes denotes a process was injected into by another process.
C. Several nodes in this process tree have watchlist hits.
D. The analyst navigated to this process analysis page from the wscrlpt.exe process.
-
Question 56:
An active compromise is detected on an endpoint. Due to current policies, the compromise was detected but not terminated.
What would be an appropriate action to end the current communication between the device and the attacker?
A. Uninstall the sensor
B. Place the system into bypass mode
C. Place the system into Quarantine D. Remotely scan the endpoint
-
Question 57:
Which strategy is used to create an exclusion in Endpoint Standard for another AV/security product?
A. Isolation Rule
B. Permission Rule
C. Approved List
D. Bypass Mode
-
Question 58:
An analyst wants to block an application's specific behavior but does not want to kill the process entirely as it is heavily used on workstations. The analyst needs to use a Blocking and Isolation Action to ensure that the process is kept alive while blocking further unwanted activity.
Which Blocking and Isolation Action should the analyst use to accomplish this goal?
A. Log Operation
B. Deny Operation
C. Terminate Process
D. Block Process
-
Question 59:
Given an event rule: Approve nVidia Drivers, changes the local state to Approved for file writes or execution blocks when the publisher is NVIDIA Corporation. How is an alert created that is triggered whenever an nVidia driver is approved by the event rule?
A. Add a new Alert of type Event Alert. Set Subtype to New unapproved file to computer and Execution block (unapproved file) and Publisher to NVIDIA Corporation. Click Create and add email recipients.
B. Click Create Alert on the event rule Approve nVidia Drivers details page. Click Create and add email recipients. Create and Exit.
C. Click Create Alert on the event rule Approve nVidia Drivers details page. Add email recipients. Create and Exit.
D. Create a custom rule name Approve nVidia that approves writes or blocks when the publisher is NVIDIA Corporation. Create an alert for rule name Approve nVidia. Click Create and add email recipients.
-
Question 60:
Which strategy should be used to purge inactive bans from the web console?
A. Schedule an add-hoc cron job to remove
B. Use a pre-configured system cron job daily to remove them
C. Run the cbbannlng script on the EDR server
D. Go to the hashes page on the web console and remove them
Related Exams:
1V0-21.20
Associate VMware Data Center Virtualization1V0-31.21
Associate VMware Cloud Management and Automation1V0-41.20
Associate VMware Network Virtualization1V0-61.21
Associate VMware Digital Workspace1V0-71.21
Associate VMware Application Modernization1V0-81.20
Associate VMware Security2V0-21.20
Professional VMware vSphere 7.x2V0-21.23
VMware vSphere 8.x Professional2V0-31.21
Professional VMware vRealize Automation 8.32V0-31.23
VMware Aria Automation 8.10 Professional
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only VMware exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your 5V0-91.20 exam preparations and VMware certification application, do not hesitate to visit our Vcedump.com to find your solutions here.