Exam Details
Exam Code
:98-367Exam Name
:Security FundamentalsCertification
:Microsoft CertificationsVendor
:MicrosoftTotal Questions
:277 Q&AsLast Updated
:Mar 25, 2025
Microsoft Microsoft Certifications 98-367 Questions & Answers
-
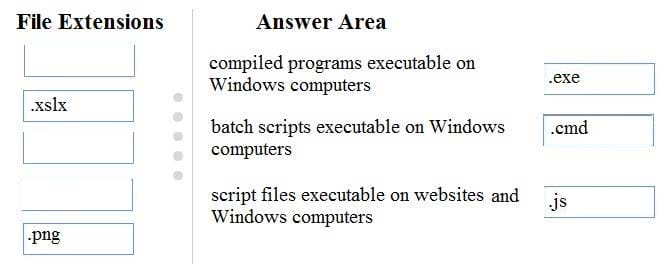
Question 271:
DRAG DROP
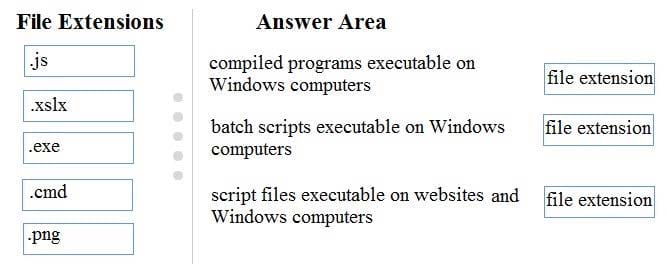
Certain potentially harmful file types should be filtered as attachments of incoming email messages.
Match the file extension that should be filtered with its description.
Instructions: To answer, drag the appropriate file extension from the column on the left to its description on the right. Each file extension may be used once, more than once, or not at all. You may need to drag the split bar between panes or
scroll to view content.
Note: For each correct selection is worth one point.
Select and Place:
-
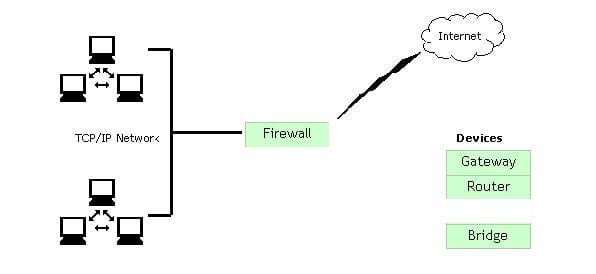
Question 272:
You work as a Network Administrator for McRobert Inc. Your company has a TCP/IP-based network. You plan to connect your company's LAN to the Internet. You are concerned about the security of your network and want to protect it against external access and misuse. Which device will you install between your LAN and the Internet to accomplish this?
Select and Place:
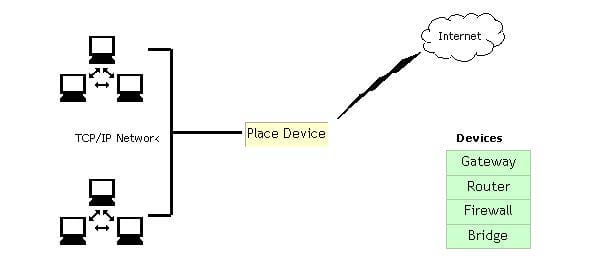
-
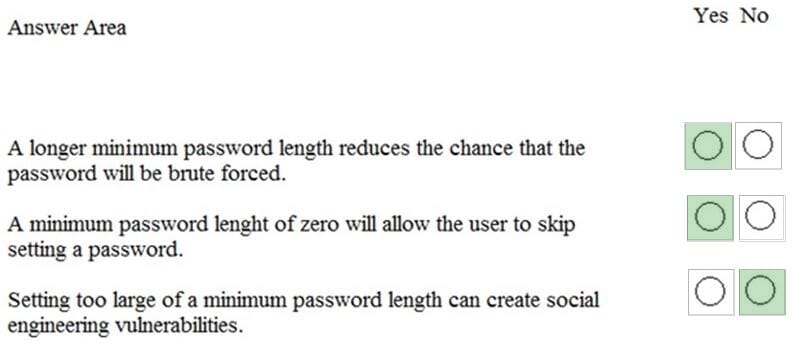
Question 273:
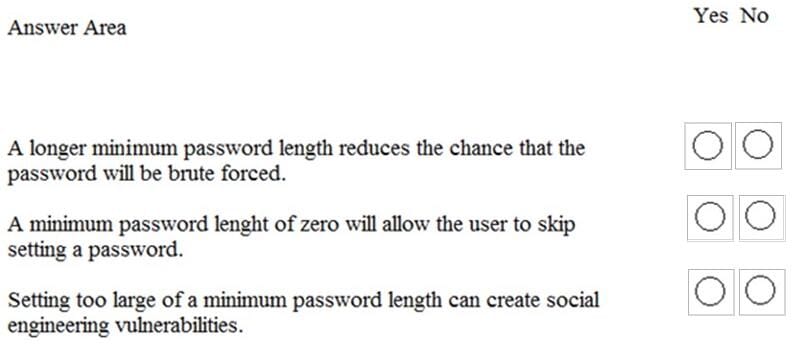
You are helping your classmates with their password settings.
Instructions: For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.
Hot Area:
-
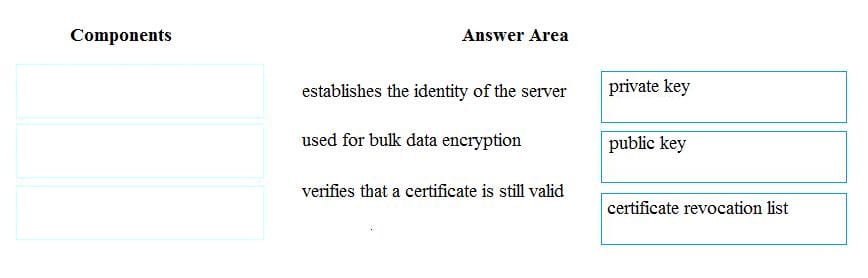
Question 274:
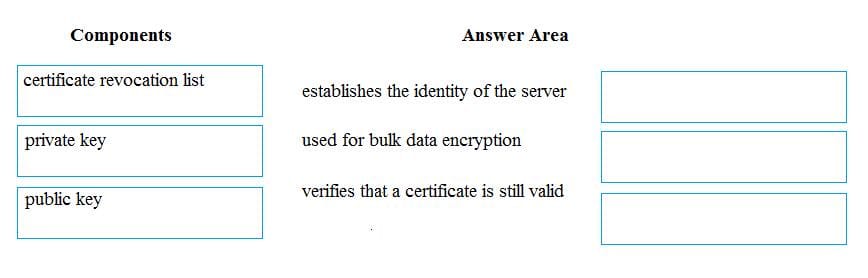
Match the components of a secure website with their role in securing communication.
Instructions: To answer, drag the appropriate component from the column on the left to its role on the right.
Each component may be used once, more than once or not at all. You may need to drag the split bar between panes or scroll to view content.
NOTE: Each correct selection is worth one point.
Select and Place:
-
Question 275:
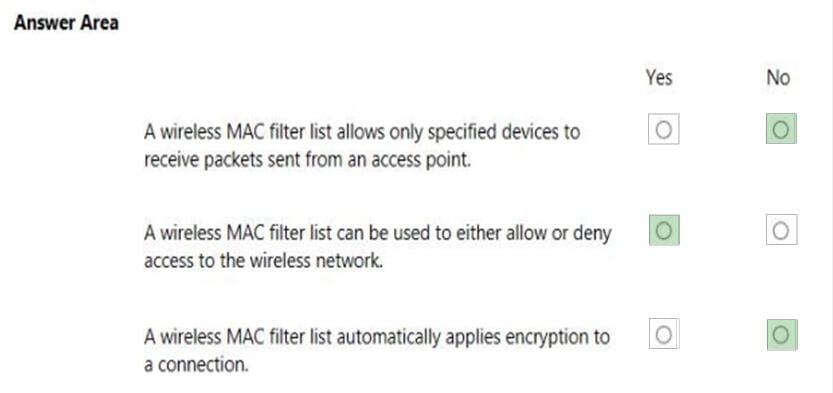
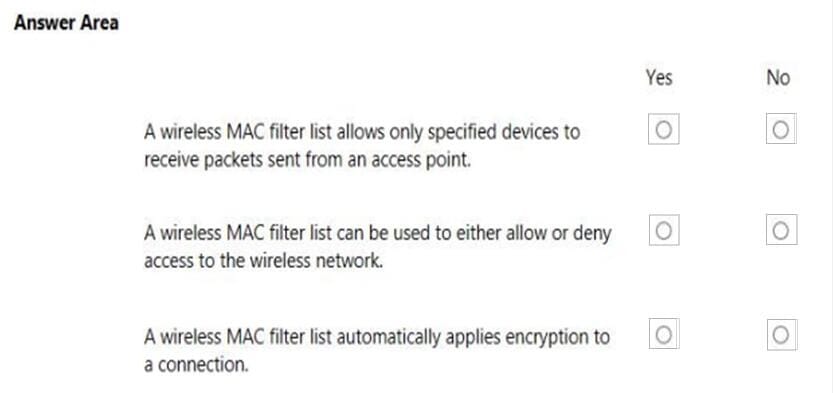
You are setting up the wireless network for your class.
Instructions: For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.
Hot Area:
-
Question 276:
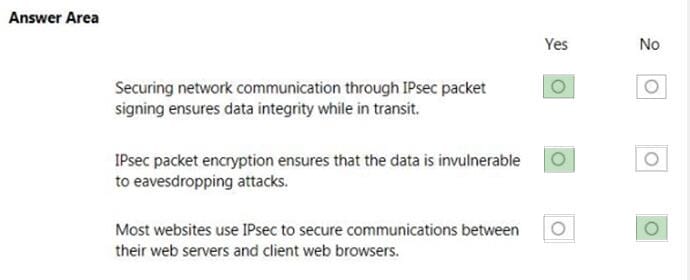
You are configuring the network settings of computers in your school's computer lab.
Instructions: For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.
Hot Area:
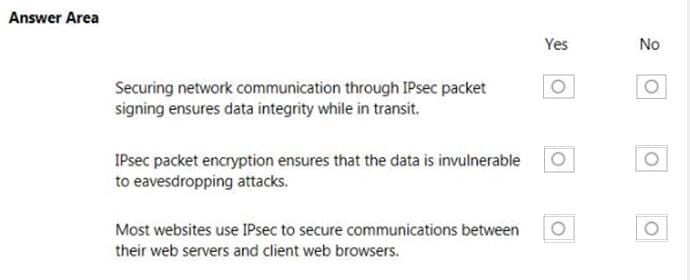
-
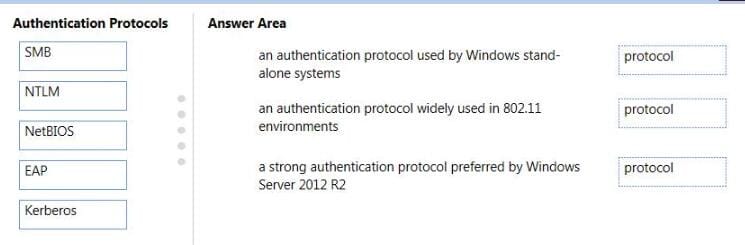
Question 277:
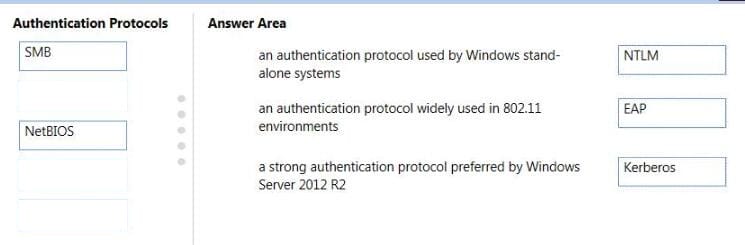
Match the authentication protocol with its description.
Instructions: To answer, drag the appropriate authentication protocol from the column on the left to its description on the right. Each authentication protocol may be used once, more than once, or not at all. You may need to drag the split bar
between panes or scroll to view content.
NOTE: Each correct selection is worth one point.
Select and Place:
Related Exams:
62-193
Technology Literacy for Educators70-243
Administering and Deploying System Center 2012 Configuration Manager70-355
Universal Windows Platform – App Data, Services, and Coding Patterns77-420
Excel 201377-427
Excel 2013 Expert Part One77-725
Word 2016 Core Document Creation, Collaboration and Communication77-726
Word 2016 Expert Creating Documents for Effective Communication77-727
Excel 2016 Core Data Analysis, Manipulation, and Presentation77-728
Excel 2016 Expert: Interpreting Data for Insights77-731
Outlook 2016 Core Communication, Collaboration and Email Skills
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only Microsoft exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your 98-367 exam preparations and Microsoft certification application, do not hesitate to visit our Vcedump.com to find your solutions here.