Exam Details
Exam Code
:C2150-197Exam Name
:IBM Security Identity Manager V6.0 ImplementationCertification
:IBM Certified Deployment ProfessionalVendor
:IBMTotal Questions
:174 Q&AsLast Updated
:Apr 16, 2025
IBM IBM Certified Deployment Professional C2150-197 Questions & Answers
-
Question 21:
Which statement is correct about identity data feed?
A. If a repeated identify feed does not contain a value for an attribute that was previously specified for the user, the identity feed process leaves that attribute unchanged for the IBM Security Identity Manager user.
B. All data feed attributes from the identity data feed must be stored in the IBM Security Systems Identity Manager person record.
C. All attributes in IBM Security Systems Identity Manager person record must exist in the identity feed source.
D. You can include some attributes in an identity feed that are not contained in the identity feed object class.
-
Question 22:
Orphan accounts are managed resource accounts whose owner in the IBM Security Identity Manager Server cannot be determined.
Orphan accounts can be assigned by the administrator to a user with which restriction?
A. When deleting the orphan accounts in IBM Security Identity Manager, they are not deleted on the managed resource.
B. The administrator can assign the orphan account to any user as long as the applicable policies allow it.
C. The administrator can assign the orphan account to any user and bypass policy enforcements.
D. The orphan account, once assigned an owner, can not become orphan again.
-
Question 23:
Which attribute is used by the default global adoption policy to match the IBM Security Identity Manager user?
A. The distinguished name of the account.
B. The e-mail address of the account.
C. The full name of the account user.
D. The account user ID.
-
Question 24:
A person modify transaction is created containing requests for two roles which are identified by a Separation of Duty policy as conflicting.
Which of the following is a TRUE statement concerning how the person modify transaction may be processed?
A. An administrator or policy owner may change either of the requested roles so that they do not conflict.
B. The person modify transaction may be completed without approving or rejecting the conflicting roles.
C. An administrator or policy owner may reject either one of the two conflicting roles.
D. An administrator or policy owner may reject or approve the role violation.
-
Question 25:
What does the following service selection policy return?
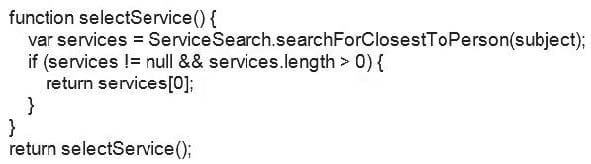
A. It returns multiple services of the same kind for the subject to choose in a dynamic workflow.
B. It returns the service closest to the subject based on the 'location' attribute of the subject.
C. It returns the service closest to the subject in the organizational tree defined in ISIM.
D. It returns the service closest to the service that the subject has requested.
-
Question 26:
What is the recommended Application Server JVM heapsizes for a 64 bit JVM?
A. 4096 MB/8192 MB
B. 1024 MB/4096 MB
C. 512 MB/1024 MB
D. 512 MB/4096 MB
-
Question 27:
A customer requires that users should NOT be able to circumvent answering challenge response questions when they login to the ISIM Self Service Console, and also wants the responses to challenges to appear masked (such as passwords) instead of appearing in plain text. How can this be achieved?
A. Setcom.ibm.tivoli.ibm.challengeResponse.bypassChallengeResponse=false and com.ibm.tivoli.ibm.challengeResponse.showAnswers=false in scriptframework.properties file.
B. Set enrole.password.challengeResponse.bypassChallengeResponse=false in enrole.properties file and select checkbox for Enable Password Editing under Security Settings.
C. Set enrole.password.challengeResponse.bypassChallengeResponse=false and enrole.password.challengeResponse.showAnswers=false in enrole.properties file.
D. Set ui.challengeResponse.bypassChallengeResponse=faise and ui.challengeResponse.showAnswers=false in ui.properties file.
-
Question 28:
What are TWO valid sets of Access Control Item (ACI) members that can be used to grant access to create or modify static organizational roles?
A. The supervisor of the business unit in which the organizational role resides.
B. Users who are members of a role other than the one being operated on.
C. Users who are members of an ISIM group.
D. The supervisor of the owner of the role.
E. Users who are members of a role.
-
Question 29:
Customer A is mining roles that reflect the employee population and their entitlements. As a design principle, which statement is TRUE in a role design for Company A?
A. Design hybrid roles, using a flag in the role definitions to convert static organizational roles to dynamic organizational roles and vice versa during steady state procedures.
B. Design only dynamic organizational roles, and ensure that person objects contain all the information needed to assign a person to a dynamic role automatically.
C. Design a mix of dynamic and static organizational roles, and encourage business processes to assign employees to static organizational roles.
D. Role design only needs to factor in groups of entitlements, since organizational roles are only used in provisioning policy membership.
-
Question 30:
Which one is NOT available in Operation workflows?
A. Subprocess Node
B. Workorder Node
C. Extension Node
D. Script Node
Related Exams:
000-567
IBM Tivoli Provisioning Manager V7.2.0.2 Implementation000-587
IBM FileNet P8 V5.1A2010-040
Assess: SmartCloud Control Desk V7.5 Change, Configuration, Release Management ImplementationA2010-505
Assess: IBM SmartCloud Control Desk V7.5.1 IT Asset ManagementA2010-568
Assess: IBM Tivoli Composite Application Manager for Application Diagnostics V7.1 ImplementationA2010-569
Assess: IBM Tivoli Workload Scheduler V8.6 ImplementationA2010-570
Assess: IBM Maximo Asset Management V7.5 ImplementationA2010-571
Assess: IBM Tivoli Process Automation Engine V7.5 ImplementationA2010-574
Assess: IBM Tivoli Business Service Manager V6.1 ImplementationA2010-599
Assess: IBM Tivoli Storage Productivity Center V5.1 Implementation
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only IBM exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your C2150-197 exam preparations and IBM certification application, do not hesitate to visit our Vcedump.com to find your solutions here.