Exam Details
Exam Code
:CS0-002Exam Name
:CompTIA Cybersecurity Analyst (CySA+)Certification
:CompTIA CertificationsVendor
:CompTIATotal Questions
:1059 Q&AsLast Updated
:Apr 17, 2025
CompTIA CompTIA Certifications CS0-002 Questions & Answers
-
Question 431:
The director of software development is concerned with recent web application security incidents, including the successful breach of a back-end database server. The director would like to work with the security team to implement a standardized way to design, build, and test web applications and the services that support them. Which of the following meets the criteria?
A. OWASP
B. SANS
C. PHP
D. Ajax
-
Question 432:
A technician receives the following security alert from the firewall's automated system:
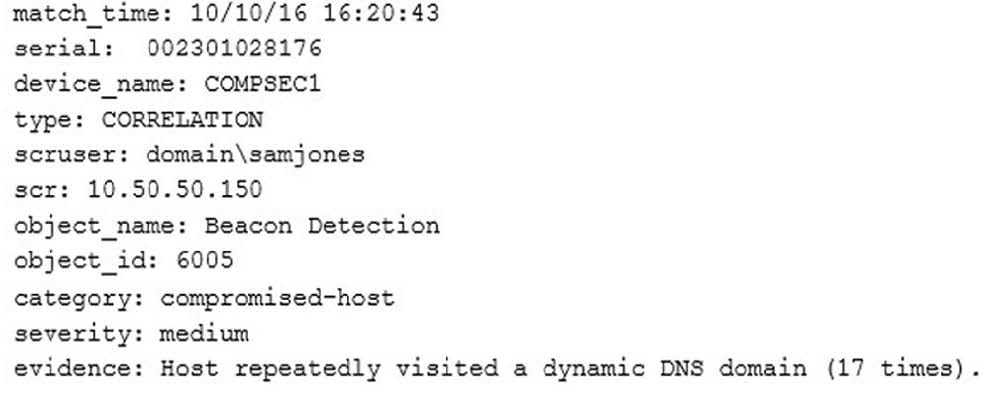
After reviewing the alert, which of the following is the BEST analysis?
A. This alert is a false positive because DNS is a normal network function.
B. This alert indicates a user was attempting to bypass security measures using dynamic DNS.
C. This alert was generated by the SIEM because the user attempted too many invalid login attempts.
D. This alert indicates an endpoint may be infected and is potentially contacting a suspect host.
-
Question 433:
During a review of security controls, an analyst was able to connect to an external, unsecured FTP server from a workstation. The analyst was troubleshooting and reviewed the ACLs of the segment firewall the workstation is connected to:
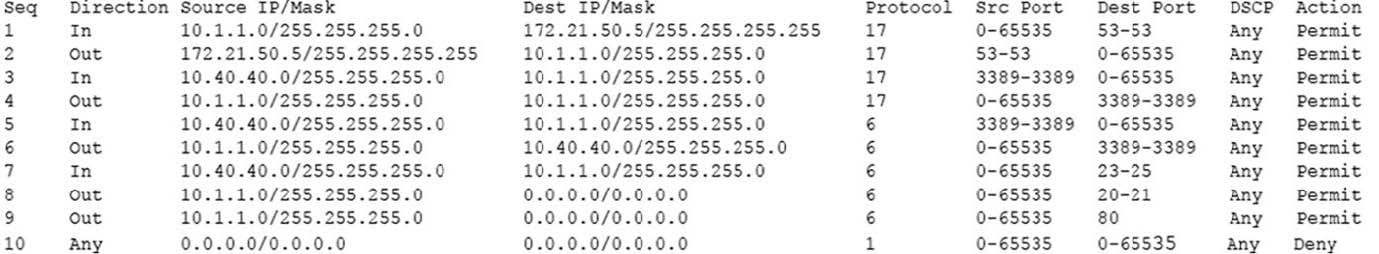
Based on the ACLs above, which of the following explains why the analyst was able to connect to the FTP server?
A. FTP was explicitly allowed in Seq 8 of the ACL.
B. FTP was allowed in Seq 10 of the ACL.
C. FTP was allowed as being included in Seq 3 and Seq 4 of the ACL.
D. FTP was allowed as being outbound from Seq 9 of the ACL.
-
Question 434:
A security analyst is reviewing logs and discovers that a company-owned computer issued to an employee is generating many alerts and warnings. The analyst continues to review the log events and discovers that a non-company-owned device from a different, unknown IP address is generating the same events. The analyst informs the manager of these findings, and the manager explains that these activities are already known and part of an ongoing events. Given this scenario, which of the following roles are the analyst, the employee, and the manager filling?
A. The analyst is red team. The employee is blue team. The manager is white team.
B. The analyst is white team. The employee is red team. The manager is blue team.
C. The analyst is red team. The employee is white team. The manager is blue team.
D. The analyst is blue team. The employee is red team. The manager is white team.
-
Question 435:
A cybersecurity analyst was asked to discover the hardware address of 30 networked assets. From a command line, which of the following tools would be used to provide ARP scanning and reflects the MOST efficient method for accomplishing the task?
A. nmap
B. tracert
C. ping -a
D. nslookup
-
Question 436:
An organization is experiencing degradation of critical services and availability of critical external resources. Which of the following can be used to investigate the issue?
A. Netflow analysis
B. Behavioral analysis
C. Vulnerability analysis
D. Risk analysis
-
Question 437:
An analyst is troubleshooting a PC that is experiencing high processor and memory consumption. Investigation reveals the following processes are running on the system:
lsass.exe csrss.exe wordpad.exe notepad.exe
Which of the following tools should the analyst utilize to determine the rogue process?
A. Ping 127.0.0.1.
B. Use grep to search.
C. Use Netstat.
D. Use Nessus.
-
Question 438:
The Chief Executive Officer (CEO) instructed the new Chief Information Security Officer (CISO) to provide a list of enhancement to the company's cybersecurity operation. As a result, the CISO has identified the need to align security operations with industry best practices. Which of the following industry references is appropriate to accomplish this?
A. OSSIM
B. NIST
C. PCI
D. OWASP
-
Question 439:
An organization wants to harden its web servers. As part of this goal, leadership has directed that vulnerability scans be performed, and the security team should remediate the servers according to industry best practices. The team has already chosen a vulnerability scanner and performed the necessary scans, and now the team needs to prioritize the fixes. Which of the following would help to prioritize the vulnerabilities for remediation in accordance with industry best practices?
A. CVSS
B. SLA
C. ITIL
D. OpenVAS
E. Qualys
-
Question 440:
A cybersecurity analyst is reviewing the following outputs:
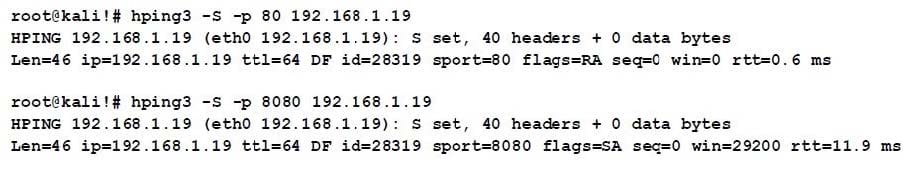
Which of the following can the analyst infer from the above output?
A. The remote host is redirecting port 80 to port 8080.
B. The remote host is running a service on port 8080.
C. The remote host's firewall is dropping packets for port 80.
D. The remote host is running a web server on port 80.
Related Exams:
220-1001
CompTIA A+ Certification: Core 1220-1002
CompTIA A+ Certification: Core 2220-1101
CompTIA A+ Certification: Core 1220-1102
CompTIA A+ Certification: Core 2220-902
CompTIA A+ CertificationCAS-004
CompTIA Advanced Security Practitioner (CASP+)CAS-005
CompTIA SecurityXCLO-001
CompTIA Cloud Essentials+CLO-002
CompTIA Cloud Essentials+CS0-002
CompTIA Cybersecurity Analyst (CySA+)
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only CompTIA exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your CS0-002 exam preparations and CompTIA certification application, do not hesitate to visit our Vcedump.com to find your solutions here.