Exam Details
Exam Code
:CS0-002Exam Name
:CompTIA Cybersecurity Analyst (CySA+)Certification
:CompTIA CertificationsVendor
:CompTIATotal Questions
:1059 Q&AsLast Updated
:Apr 17, 2025
CompTIA CompTIA Certifications CS0-002 Questions & Answers
-
Question 671:
At which of the following phases of the SDLC shoukJ security FIRST be involved?
A. Design
B. Maintenance
C. Implementation
D. Analysis
E. Planning
F. Testing
-
Question 672:
While conoXicting a cloud assessment, a security analyst performs a Prowler scan, which generates the following within the report:
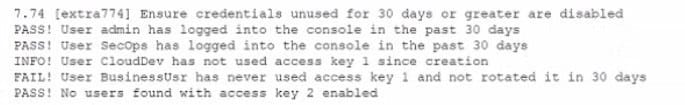
Based on the Prowler report, which of the following is the BEST recommendation?
A. Delete Cloud Dev access key 1
B. Delete BusinessUsr access key 1.
C. Delete access key 1.
D. Delete access key 2.
-
Question 673:
An analyst is reviewing the following output as part of an incident: Which of the Wowing is MOST likely happening?
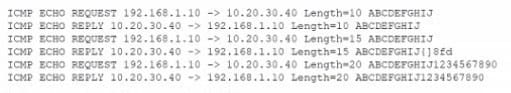
A. The hosts are part of a reflective denial -of -service attack.
B. Information is leaking from the memory of host 10.20 30.40
C. Sensitive data is being exfilltrated by host 192.168.1.10.
D. Host 291.168.1.10 is performing firewall port knocking.
-
Question 674:
While monitoring the information security notification mailbox, a security analyst notices several emails were repotted as spam. Which of the following should the analyst do FIRST?
A. Block the sender In the email gateway.
B. Delete the email from the company's email servers.
C. Ask the sender to stop sending messages.
D. Review the message in a secure environment.
-
Question 675:
A company uses an FTP server to support its critical business functions The FTP server is configured as follows:
The FTP service is running with (he data duectory configured in /opt/ftp/data. The FTP server hosts employees' home aVectories in /home Employees may store sensitive information in their home directories
An loC revealed that an FTP director/ traversal attack resulted in sensitive data loss.
Which of the following should a server administrator implement to reduce the risk of current and future directory traversal attacks targeted at the FTP server?
A. Implement file-level encryption of sensitive files
B. Reconfigure the FTP server to support FTPS
C. Run the FTP server n a chroot environment
D. Upgrade the FTP server to the latest version
-
Question 676:
As part of the senior leadership team's ongoing nsk management activities the Chief Information Security Officer has tasked a security analyst with coordinating the right training and testing methodology to respond to new business initiatives or significant changes to existing ones The management team wants to examine a new business process that would use existing infrastructure to process and store sensitive data.
Which of the following would be appropnate for the security analyst to coordinate?
A. A black-box penetration testing engagement
B. A tabletop exercise
C. Threat modeling
D. A business impact analysis
-
Question 677:
A security analyst discovers suspicious host activity while performing monitoring activities. The analyst pulls a packet capture for the activity and sees the following:
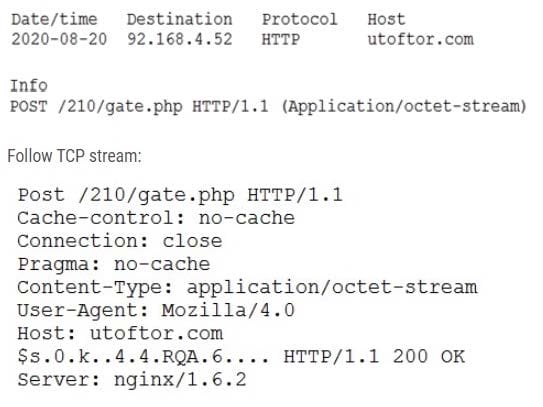
Which of the following describes what has occurred?
A. The host attempted to download an application from utoftor.com.
B. The host downloaded an application from utoftor.com.
C. The host attempted to make a secure connection to utoftor.com.
D. The host rejected the connection from utoftor.com.
-
Question 678:
Which of the following, BEST explains the function of TPM?
A. To provide hardware-based security features using unique keys
B. To ensure platform confidentiality by storing security measurements
C. To improve management of the OS installation.
D. To implement encryption algorithms for hard drives
-
Question 679:
An organization wants to implement a privileged access management solution to belter manage the use ot emergency and privileged service accounts. Which of the following would BEST satisfy the organization's goal?
A. Access control lists
B. Discretionary access controls
C. Policy-based access controls
D. Credential vaulting
-
Question 680:
A cybersecunty analyst needs to harden a server that is currently being used as a web server The server needs to be accessible when entenng www company com into the browser Additionally web pages require frequent updates which are performed by a remote contractor Given the following output:
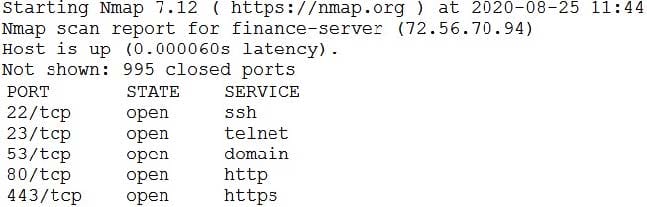
Which of the following should the cybersecunty analyst recommend to harden the server? (Select TWO).
A. Uninstall the DNS service
B. Perform a vulnerability scan
C. Change the server's IP to a private IP address
D. Disable the Telnet service
E. Block port 80 with the host-based firewall
F. Change the SSH port to a non-standard port
Related Exams:
220-1001
CompTIA A+ Certification: Core 1220-1002
CompTIA A+ Certification: Core 2220-1101
CompTIA A+ Certification: Core 1220-1102
CompTIA A+ Certification: Core 2220-902
CompTIA A+ CertificationCAS-004
CompTIA Advanced Security Practitioner (CASP+)CAS-005
CompTIA SecurityXCLO-001
CompTIA Cloud Essentials+CLO-002
CompTIA Cloud Essentials+CS0-002
CompTIA Cybersecurity Analyst (CySA+)
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only CompTIA exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your CS0-002 exam preparations and CompTIA certification application, do not hesitate to visit our Vcedump.com to find your solutions here.