Exam Details
Exam Code
:CS0-002Exam Name
:CompTIA Cybersecurity Analyst (CySA+)Certification
:CompTIA CertificationsVendor
:CompTIATotal Questions
:1059 Q&AsLast Updated
:Apr 17, 2025
CompTIA CompTIA Certifications CS0-002 Questions & Answers
-
Question 721:
A security administrator needs to provide access from partners to an Isolated laboratory network inside an organization that meets the following requirements:
The partners' PCs must not connect directly to the laboratory network. The tools the partners need to access while on the laboratory network must be available to all partners The partners must be able to run analyses on the laboratory network, which may take hours to complete
Which of the following capabilities will MOST likely meet the security objectives of the request?
A. Deployment of a jump box to allow access to the laboratory network and use of VDI in persistent mode to provide the necessary tools for analysis
B. Deployment of a firewall to allow access to the laboratory network and use of VDI in non-persistent mode to provide the necessary tools tor analysis
C. Deployment of a firewall to allow access to the laboratory network and use of VDI In persistent mode to provide the necessary tools for analysis
D. Deployment of a jump box to allow access to the Laboratory network and use of VDI in non-persistent mode to provide the necessary tools for analysis
-
Question 722:
A Chief Information Secunty Officer has asked for a list of hosts that have critical and high- seventy findings as referenced in the CVE database. Which of the following tools would produce the assessment output needed to satisfy this request?
A. Nessus
B. Nikto
C. Fuzzer
D. Wireshark
E. Prowler
-
Question 723:
Which of me following are reasons why consumer IoT devices should be avoided in an enterprise environment? (Select TWO)
A. Message queuing telemetry transport does not support encryption.
B. The devices may have weak or known passwords.
C. The devices may cause a dramatic Increase in wireless network traffic.
D. The devices may utilize unsecure network protocols.
E. Multiple devices may interface with the functions of other loT devices.
F. The devices are not compatible with TLS 12.
-
Question 724:
The incident response team is working with a third-party forensic specialist to investigate the root cause of a recent intrusion An analyst was asked to submit sensitive network design details for review The forensic specialist recommended electronic delivery for efficiency but email was not an approved communication channel to send network details Which of the following BEST explains the importance of using a secure method of communication during incident response?
A. To prevent adversaries from intercepting response and recovery details
B. To ensure intellectual property remains on company servers
C. To have a backup plan in case email access is disabled
D. To ensure the management team has access to all the details that are being exchanged
-
Question 725:
As part of an Intelligence feed, a security analyst receives a report from a third-party trusted source. Within the report are several detrains and reputational information that suggest the company's employees may be targeted for a phishing campaign. Which of the following configuration changes would be the MOST appropriate for Mergence gathering?
A. Update the whitelist.
B. Develop a malware signature.
C. Sinkhole the domains
D. Update the Blacklist
-
Question 726:
Which of following allows Secure Boot to be enabled?
A. eFuse
B. UEFI
C. MSM
D. PAM
-
Question 727:
A team of network security analysts is examining network traffic to determine if sensitive data was exfitrated Upon further investigation, the analysts believe confidential data was compromised. Which of me following capattlnes would BEST defend against tnts type of sensitive data eifiitraUon?
A. Deploy an edge firewal.
B. Implement DLP
C. Deploy EDR.
D. Enaypi the hard drives
-
Question 728:
While investigating reports or issues with a web server, a security analyst attempts to log in remotely and recedes the following message:
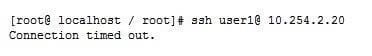
The analyst accesses the server console, and the following console messages are displayed:
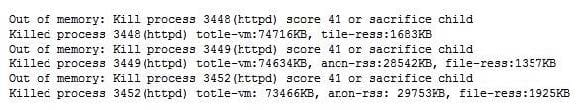
The analyst is also unable to log in on the console. While reviewing network captures for the server, the analyst sees many packets with the following signature:
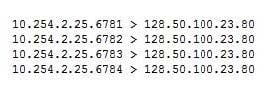
Which of the following is the BEST step for the analyst to lake next in this situation?
A. Load the network captures into a protocol analyzer to further investigate the communication with 128.30.100.23, as this may be a botnet command server
B. After ensuring network captures from the server are saved isolate the server from the network take a memory snapshot, reboot and log in to do further analysis.
C. Corporate data is being exfilltrated from the server Reboot the server and log in to see if it contains any sensitive data.
D. Cryptomining malware is running on the server and utilizing an CPU and memory. Reboot the server and disable any cron Jobs or startup scripts that start the mining software.
-
Question 729:
A cybersecurity analyst needs to determine whether a large file named access log from a web server contains the following loC:
../../../../bin/bash
Which of the following commands can be used to determine if the string is present in the log?
A. echo access.log | grep "../../../../bin/bash"
B. grep "../../../../bin/bash" 1 cat access.log
C. grep "../../../. ./bin/bash" < access.log
D. cat access.log > grep "../../../ ../bin/bash"
-
Question 730:
Which of the following describes the mam difference between supervised and unsupervised machine-learning algorithms that are used in cybersecurity applications?
A. Supervised algorithms can be used to block attacks, while unsupervised algorithms cannot.
B. Supervised algorithms require security analyst feedback, while unsupervised algorithms do not.
C. Unsupervised algorithms are not suitable for IDS systems, white supervised algorithms are
D. Unsupervised algorithms produce more false positives. Than supervised algorithms.
Related Exams:
220-1001
CompTIA A+ Certification: Core 1220-1002
CompTIA A+ Certification: Core 2220-1101
CompTIA A+ Certification: Core 1220-1102
CompTIA A+ Certification: Core 2220-902
CompTIA A+ CertificationCAS-004
CompTIA Advanced Security Practitioner (CASP+)CAS-005
CompTIA SecurityXCLO-001
CompTIA Cloud Essentials+CLO-002
CompTIA Cloud Essentials+CS0-002
CompTIA Cybersecurity Analyst (CySA+)
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only CompTIA exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your CS0-002 exam preparations and CompTIA certification application, do not hesitate to visit our Vcedump.com to find your solutions here.