Exam Details
Exam Code
:CS0-002Exam Name
:CompTIA Cybersecurity Analyst (CySA+)Certification
:CompTIA CertificationsVendor
:CompTIATotal Questions
:1059 Q&AsLast Updated
:Apr 09, 2025
CompTIA CompTIA Certifications CS0-002 Questions & Answers
-
Question 871:
Which of the following technologies can be used to store digital certificates and is typically used in high- security implementations where integrity is paramount?
A. HSM
B. eFuse
C. UEFI
D. Self-encrypting drive
-
Question 872:
A security analyst is conducting a post-incident log analysis to determine which indicators can be used to detect further occurrences of a data exfiltration incident. The analyst determines backups were not performed during this time and reviews the following:
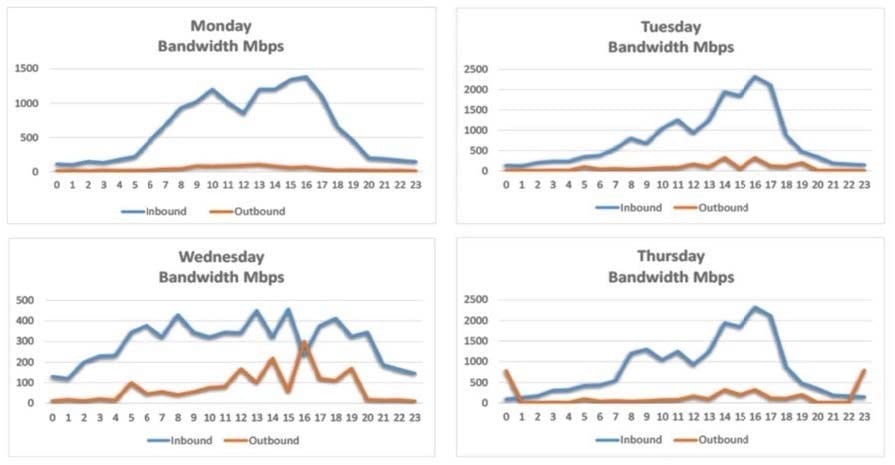
Which of the following should the analyst review to find out how the data was exfilltrated?
A. Monday's logs
B. Tuesday's logs
C. Wednesday's logs
D. Thursday's logs
-
Question 873:
A team of security analysis has been alerted to potential malware activity. The initial examination indicates one of the affected workstations on beaconing on TCP port 80 to five IP addresses and attempting to spread across the network over port 445. Which of the following should be the team's NEXT step during the detection phase of this response process?
A. Escalate the incident to management ,who will then engage the network infrastructure team to keep them informed
B. Depending on system critically remove each affected device from the network by disabling wired and wireless connections
C. Engage the engineering team to block SMB traffic internally and outbound HTTP traffic to the five IP addresses Identify potentially affected systems by creating a correlation
D. Identify potentially affected system by creating a correlation search in the SIEM based on the network traffic.
-
Question 874:
While preparing of an audit of information security controls in the environment an analyst outlines a framework control that has the following requirements:
1.
All sensitive data must be classified
2.
All sensitive data must be purged on a quarterly basis
3.
Certificates of disposal must remain on file for at least three years This framework control is MOST likely classified as:
A. prescriptive
B. risk-based
C. preventive
D. corrective
-
Question 875:
An organization developed a comprehensive modern response policy Executive management approved the policy and its associated procedures. Which of the following activities would be MOST beneficial to evaluate personnel's familiarity with incident response procedures?
A. A simulated breach scenario evolving the incident response team
B. Completion of annual information security awareness training by ail employees
C. Tabtetop activities involving business continuity team members
D. Completion of lessons-learned documentation by the computer security incident response team
E. External and internal penetration testing by a third party
-
Question 876:
Which of me following BEST articulates the benefit of leveraging SCAP in an organization's cybersecurity analysis toolset?
A. It automatically performs remedial configuration changes lo enterprise security services
B. It enables standard checklist and vulnerability analysis expressions for automaton
C. It establishes a continuous integration environment for software development operations
D. It provides validation of suspected system vulnerabilities through workflow orchestration
-
Question 877:
A security analyst needs to assess the web server versions on a list of hosts to determine which are running a vulnerable version of the software and output that list into an XML file named Webserverlist. Xml. The host list is provided in a file named werbserverlist,text. Which of the fallowing Nmap commands would BEST accomplish this goal?
A. nmap -iL webserverlist.txt -sC -p 443 -oX webserverlist.xml
B. nmap -iL webserverlist.txt -sV -p 443 -oX webserverlist.xml
C. nmap -iL webserverlist.txt -F -p 443 -oX webserverlist.xml
D. nmap --takefile webserverlist.txt --outputfileasXML webserverlist.xml –scanports 443
-
Question 878:
A security analyst has been alerted to several emails that snow evidence an employee is planning malicious activities that involve employee Pll on the network before leaving the organization. The security analysis BEST response would be to coordinate with the legal department and:
A. the public relations department
B. senior leadership
C. law enforcement
D. the human resources department
-
Question 879:
An information security analyst is working with a data owner to identify the appropriate controls to preserve the confidentiality of data within an enterprise environment One of the primary concerns is exfiltration of data by malicious insiders Which of the following controls is the MOST appropriate to mitigate risks?
A. Data deduplication
B. OS fingerprinting
C. Digital watermarking
D. Data loss prevention
-
Question 880:
A security analyst is attempting to utilize the blowing threat intelligence for developing detection capabilities:
APT X's approach to a target would be sending a phishing email to the target after conducting active and passive reconnaissance. Upon successful compromise, APT X conducts internal reconnaissance and attempts to move laterally by utilizing existing resources. When APT X finds data that aligns to its objectives, it stages and then exfiltrates data sets in sizes that can range from 1GB to 5GB. APT X also establishes several backdoors to maintain a C2 presence in the environment.
In which of the following phases is this APT MOST likely to leave discoverable artifacts?
A. Data collection/exfiltration
B. Defensive evasion
C. Lateral movement
D. Reconnaissance
Related Exams:
220-1001
CompTIA A+ Certification: Core 1220-1002
CompTIA A+ Certification: Core 2220-1101
CompTIA A+ Certification: Core 1220-1102
CompTIA A+ Certification: Core 2220-902
CompTIA A+ CertificationCAS-004
CompTIA Advanced Security Practitioner (CASP+)CAS-005
CompTIA SecurityXCLO-001
CompTIA Cloud Essentials+CLO-002
CompTIA Cloud Essentials+CS0-002
CompTIA Cybersecurity Analyst (CySA+)
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only CompTIA exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your CS0-002 exam preparations and CompTIA certification application, do not hesitate to visit our Vcedump.com to find your solutions here.