Exam Details
Exam Code
:CS0-002Exam Name
:CompTIA Cybersecurity Analyst (CySA+)Certification
:CompTIA CertificationsVendor
:CompTIATotal Questions
:1059 Q&AsLast Updated
:Mar 23, 2025
CompTIA CompTIA Certifications CS0-002 Questions & Answers
-
Question 981:
A user's computer has been running slowly when the user tries to access web pages. A security analyst runs the command netstat -aon from the command line and receives the following output:
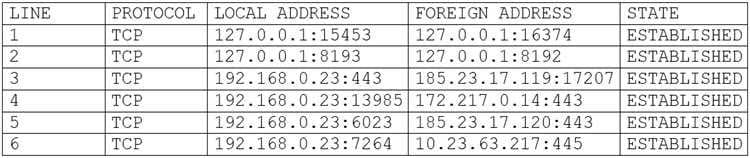
Which of the following lines indicates the computer may be compromised?
A. Line 1
B. Line 2
C. Line 3
D. Line 4
E. Line 5
F. Line 6
-
Question 982:
During routine monitoring, a security analyst discovers several suspicious websites that are communicating with a local host. The analyst queries for IP 192.168.50.2 for a 24-hour period:
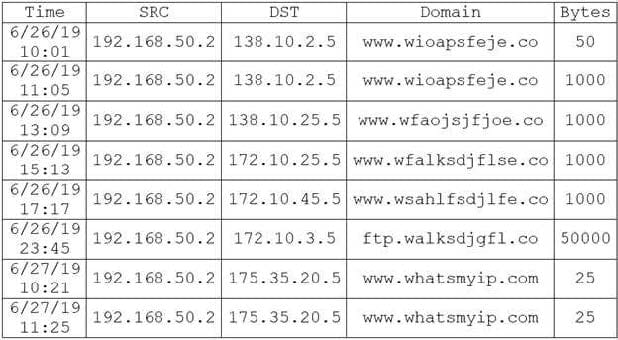
To further investigate, the analyst should request PCAP for SRC 192.168.50.2 and __________.
A. DST 138.10.2.5.
B. DST 138.10.25.5.
C. DST 172.10.3.5.
D. DST 172.10.45.5.
E. DST 175.35.20.5.
-
Question 983:
For machine learning to be applied effectively toward security analysis automation, it requires __________.
A. relevant training data.
B. a threat feed API.
C. a multicore, multiprocessor system.
D. anomalous traffic signatures.
-
Question 984:
A large amount of confidential data was leaked during a recent security breach. As part of a forensic investigation, the security team needs to identify the various types of traffic that were captured between two
compromised devices.
Which of the following should be used to identify the traffic?
A. Carving
B. Disk imaging
C. Packet analysis
D. Memory dump
E. Hashing
-
Question 985:
Which of the following sets of attributes BEST illustrates the characteristics of an insider threat from a security perspective?
A. Unauthorized, unintentional, benign
B. Unauthorized, intentional, malicious
C. Authorized, intentional, malicious
D. Authorized, unintentional, benign
-
Question 986:
A security analyst has observed several incidents within an organization that are affecting one specific piece of hardware on the network. Further investigation reveals the equipment vendor previously released a patch.
Which of the following is the MOST appropriate threat classification for these incidents?
A. Known threat
B. Zero day
C. Unknown threat
D. Advanced persistent threat
-
Question 987:
An incident responder successfully acquired application binaries off a mobile device for later forensic analysis. Which of the following should the analyst do NEXT?
A. Decompile each binary to derive the source code.
B. Perform a factory reset on the affected mobile device.
C. Compute SHA-256 hashes for each binary.
D. Encrypt the binaries using an authenticated AES-256 mode of operation.
E. Inspect the permissions manifests within each application.
-
Question 988:
The security team at a large corporation is helping the payment-processing team to prepare for a regulatory compliance audit and meet the following objectives:
Reduce the number of potential findings by the auditors. Limit the scope of the audit to only devices used by the payment-processing team for activities directly impacted by the regulations. Prevent the external-facing web infrastructure used
by other teams from coming into scope. Limit the amount of exposure the company will face if the systems used by the payment-processing team are compromised.
Which of the following would be the MOST effective way for the security team to meet these objectives?
A. Limit the permissions to prevent other employees from accessing data owned by the business unit.
B. Segment the servers and systems used by the business unit from the rest of the network.
C. Deploy patches to all servers and workstations across the entire organization.
D. Implement full-disk encryption on the laptops used by employees of the payment-processing team.
-
Question 989:
A security analyst needs to reduce the overall attack surface. Which of the following infrastructure changes should the analyst recommend?
A. Implement a honeypot.
B. Air gap sensitive systems.
C. Increase the network segmentation.
D. Implement a cloud-based architecture.
-
Question 990:
A security analyst is building a malware analysis lab. The analyst wants to ensure malicious applications are not capable of escaping the virtual machines and pivoting to other networks. To BEST mitigate this risk, the analyst should use __________.
A. an 802.11ac wireless bridge to create an air gap.
B. a managed switch to segment the lab into a separate VLAN.
C. a firewall to isolate the lab network from all other networks.
D. an unmanaged switch to segment the environments from one another.
Related Exams:
220-1001
CompTIA A+ Certification: Core 1220-1002
CompTIA A+ Certification: Core 2220-1101
CompTIA A+ Certification: Core 1220-1102
CompTIA A+ Certification: Core 2220-902
CompTIA A+ CertificationCAS-004
CompTIA Advanced Security Practitioner (CASP+)CAS-005
CompTIA SecurityXCLO-001
CompTIA Cloud Essentials+CLO-002
CompTIA Cloud Essentials+CS0-002
CompTIA Cybersecurity Analyst (CySA+)
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only CompTIA exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your CS0-002 exam preparations and CompTIA certification application, do not hesitate to visit our Vcedump.com to find your solutions here.