Exam Details
Exam Code
:EC0-349Exam Name
:Computer Hacking Forensic InvestigatorCertification
:EC-COUNCIL CertificationsVendor
:EC-COUNCILTotal Questions
:304 Q&AsLast Updated
:Apr 13, 2025
EC-COUNCIL EC-COUNCIL Certifications EC0-349 Questions & Answers
-
Question 171:
This type of testimony is presented by someone who does the actual fieldwork and does not offer a view in court.
A. Civil litigation testimony
B. Expert testimony
C. Victim advocate testimony
D. Technical testimony
-
Question 172:
On an Active Directory network using NTLM authentication, where on the domain controllers are the passwords stored?
A. SAM
B. AMS
C. Shadow file
D. Password.conf
-
Question 173:
Why is it still possible to recover files that have been emptied from the Recycle Bin on a Windows computer?
A. The data is still present until the original location of the file is used
B. The data is moved to the Restore directory and is kept there indefinitely
C. The data will reside in the L2 cache on a Windows computer until it is manually deleted
D. It is not possible to recover data that has been emptied from the Recycle Bin
-
Question 174:
When is it appropriate to use computer forensics?
A. If copyright and intellectual property theft/misuse has occurred
B. If employees do not care for their boss management techniques
C. If sales drop off for no apparent reason for an extended period of time
D. If a financial institution is burglarized by robbers
-
Question 175:
Madison is on trial for allegedly breaking into her university internal network. The police raided her dorm room and seized all of her computer equipment. Madison lawyer is trying to convince the judge that the seizure was unfounded and baseless. Under which US Amendment is Madison lawyer trying to prove the police violated?
A. The 10th Amendment
B. The 5th Amendment
C. The 1st Amendment
D. The 4th Amendment
-
Question 176:
Using Linux to carry out a forensics investigation, what would the following command accomplish? dd if=/usr/home/partition.image of=/dev/sdb2 bs=4096 conv=notrunc,noerror
A. Search for disk errors within an image file
B. Backup a disk to an image file
C. Copy a partition to an image file
D. Restore a disk from an image file
-
Question 177:
A computer forensics investigator is inspecting the firewall logs for a large financial institution that has employees working 24 hours a day, 7 days a week.
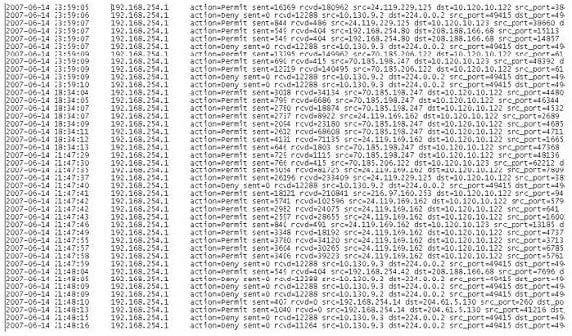
What can the investigator infer from the screenshot seen below?
A. A smurf attack has been attempted
B. A denial of service has been attempted
C. Network intrusion has occurred
D. Buffer overflow attempt on the firewall.
-
Question 178:
When investigating a wireless attack, what information can be obtained from the DHCP logs?
A. The operating system of the attacker and victim computers
B. IP traffic between the attacker and the victim
C. MAC address of the attacker
D. If any computers on the network are running in promiscuous mode
-
Question 179:
Which program is the bootloader when Windows XP starts up?
A. KERNEL.EXE
B. NTLDR
C. LOADER
D. LILO
-
Question 180:
What encryption technology is used on Blackberry devices Password Keeper?
A. 3DES
B. AES
C. Blowfish
D. RC5
Related Exams:
112-51
EC-Council Certified Network Defense Essentials (NDE)212-77
EC-Council Certified Linux Security212-81
EC-Council Certified Encryption Specialist (ECES)212-82
EC-Council Certified Cybersecurity Technician (C|CT)212-89
EC-Council Certified Incident Handler (ECIH)312-38
EC-Council Certified Network Defender (CND)312-39
EC-Council Certified SOC Analyst (CSA)312-40
EC-Council Certified Cloud Security Engineer (CCSE)312-49
ECCouncil Computer Hacking Forensic Investigator (V9)312-49V10
EC-Council Certified Computer Hacking Forensic Investigator (V10)
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only EC-COUNCIL exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your EC0-349 exam preparations and EC-COUNCIL certification application, do not hesitate to visit our Vcedump.com to find your solutions here.