Exam Details
Exam Code
:ECSSExam Name
:EC-Council Certified Security Specialist (ECSS) v10Certification
:EC-COUNCIL CertificationsVendor
:EC-COUNCILTotal Questions
:337 Q&AsLast Updated
:Apr 09, 2025
EC-COUNCIL EC-COUNCIL Certifications ECSS Questions & Answers
-
Question 161:
Which of the following Trojans is used by attackers to modify the Web browser settings?
A. Trojan.Lodear
B. Win32/Pacex.Gen
C. WMA/TrojanDownloader.GetCodec
D. Win32/FlyStudio
-
Question 162:
Peter works as a professional Computer Hacking Forensic Investigator for eLaw-Suit law firm. He is working on a case of a cyber crime. Peter knows that the good investigative report should not only communicate the relevant facts, but also present expert opinion. This report should not include the cases in which the expert acted as a lay witness. Which of the following type of witnesses is a lay witness?
A. One who observes an event.
B. One with special knowledge of the subject about which he or she is testifying.
C. One who can give a firsthand account of something seen, heard, or experienced.
D. One who is not qualified as an expert witness.
-
Question 163:
You are a professional Computer Hacking forensic investigator. You have been called to collect the evidences of Buffer Overflows or Cookie snooping attack. Which of the following logs will you review to accomplish the task?
Each correct answer represents a complete solution. Choose all that apply.
A. Web server logs
B. Event logs
C. System logs
D. Program logs
-
Question 164:
Which two security components should you implement on the sales personnel portable computers to increase security?
(Click the Exhibit button on the toolbar to see the case study.)
Each correct answer represents a complete solution. Choose two.
A. Remote access policy
B. L2TP over IPSec
C. Encrypting File System (EFS)
D. Remote Authentication Dial-In User Service (RADIUS)
E. PPTP
-
Question 165:
Which of the following is the first computer virus that was used to infect the boot sector of storage media formatted with the DOS File Allocation Table (FAT) file system?
A. I love you
B. Melissa
C. Brain
D. Tequila
-
Question 166:
RRD Job World wants to upgrade its network. The company decides to implement a TCP/IP- based network. According to the case study, RRD Job World is concerned about security. Which of the following methods should the on-site employees use to communicate securely with the headquarters?
(Click the Exhibit button on the toolbar to see the case study.)
A. L2TP over IPSec
B. Windows NT Challenge/Response (NTLM) authentication
C. DNS security and group policies
D. Basic (Clear Text) authentication using SSL
-
Question 167:
Which of the following statutes is enacted in the U.S., which prohibits creditors from collecting data from applicants, such as national origin, caste, religion etc?
A. The Equal Credit Opportunity Act (ECOA)
B. The Fair Credit Reporting Act (FCRA)
C. The Privacy Act
D. The Electronic Communications Privacy Act
-
Question 168:
Who among the following are security experts who specialize in penetration testing and other testing methodologies to ensure that their company's information systems are secure?
Each correct answer represents a complete solution. Choose all that apply.
A. Black hat hackers
B. Script Kiddies
C. White hat hackers
D. Ethical hackers
-
Question 169:
You work as a Network Security Analyzer. You got a suspicious email while working on a forensic project. Now, you want to know the IP address of the sender so that you can analyze various information such as the actual location, domain information, operating system being used, contact information, etc. of the email sender with the help of various tools and resources. You also want to check whether this email is fake or real. You know that analysis of email headers is a good starting point in such cases. The email header of the suspicious email is given below: What is the IP address of the sender of this email?
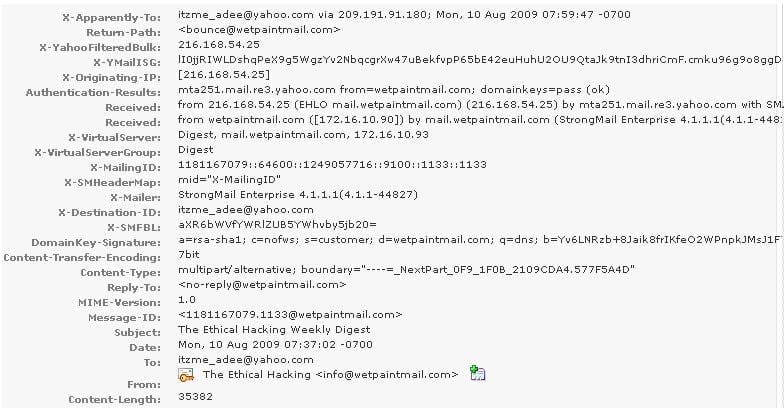
A. 209.191.91.180
B. 216.168.54.25
C. 172.16.10.90
D. 141.1.1.1
-
Question 170:
Andrew works as a Forensic Investigator for PassGuide Inc. The company has a Windows-based environment. The company's employees use Microsoft Outlook Express as their e-mail client program. E-mails of some employees have been deleted due to a virus attack on the network. Andrew is therefore assigned the task to recover the deleted mails. Which of the following tools can Andrew use to accomplish the task?
Each correct answer represents a complete solution. Choose two.
A. EventCombMT
B. eMailTrackerPro
C. FINALeMAIL
D. R-mail
Related Exams:
112-51
EC-Council Certified Network Defense Essentials (NDE)212-77
EC-Council Certified Linux Security212-81
EC-Council Certified Encryption Specialist (ECES)212-82
EC-Council Certified Cybersecurity Technician (C|CT)212-89
EC-Council Certified Incident Handler (ECIH)312-38
EC-Council Certified Network Defender (CND)312-39
EC-Council Certified SOC Analyst (CSA)312-40
EC-Council Certified Cloud Security Engineer (CCSE)312-49
ECCouncil Computer Hacking Forensic Investigator (V9)312-49V10
EC-Council Certified Computer Hacking Forensic Investigator (V10)
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only EC-COUNCIL exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your ECSS exam preparations and EC-COUNCIL certification application, do not hesitate to visit our Vcedump.com to find your solutions here.