Exam Details
Exam Code
:ECSSExam Name
:EC-Council Certified Security Specialist (ECSS) v10Certification
:EC-COUNCIL CertificationsVendor
:EC-COUNCILTotal Questions
:337 Q&AsLast Updated
:Apr 09, 2025
EC-COUNCIL EC-COUNCIL Certifications ECSS Questions & Answers
-
Question 231:
Cola Co. manufactures, markets, sells, and distributes non-alcoholic potables such as Lemcaa and Thunder Up under its brand name Cola and uses green and red logo. Mola Co., a new company, starts manufacturing, marketing, selling, and distributing non-alcoholic potables like Lumca and Cloud Up under its brand name Mola and uses green and red logo. Which of the following violations has been committed by Mola Co.?
A. Copyright infringement
B. Trademark infringement
C. Patent law
D. Plagiarism
-
Question 232:
John works as a Security Administrator for NetPerfect Inc. The company uses Windows-based systems. A project has been assigned to John to track malicious hackers and to strengthen the company's security system. John configures a computer system to trick malicious hackers into thinking that it is the company's main server, which in fact is a decoy system to track hackers.
Which system is John using to track the malicious hackers?
A. Bastion host
B. Honeypot
C. Honeytokens
D. Intrusion Detection System (IDS)
-
Question 233:
Maria works as a Desktop Technician for PassGuide Inc. She has received an e-mail from the MN
Compensation Office with the following message:
If Maria replies to this mail, which of the following attacks may she become vulnerable to?
Dear Sir/Madam,
My name is Edgar Rena, the director of compensation here at the MN Compensation Office in
Chicago. We receive so many complaints about fraudulent activities that have been taking place in your region for the past few years. Due to the high volume loss of money, the MN compensation department has had an agreement with the
appropriate authority to compensate each victim with a sum of USD$500,000.00.
You were selected among the list of people to be paid this sum. To avoid any imperative mood by intending scammers, your payment has been transmuted into an International bank draft which can be cashed at any local bank in your
country.
Please fill the below details and send it to our secretary for your compensation bank draft.
Full name: ______
Address:______
Tel:______
Fill and Send to:______
Dr. Michael Brown
MN Compensation Office, IL
Tel: +1-866-233-8434
Email: [email protected]
Further instructions shall be given to you by our secretary as soon as you contact him. To avoid losing your compensation, you are requested to pay the sum of $350 for Insurance Premium to our secretary.
Thanks and God bless.
Rate now:
A. Phishing attack
B. SYN attack
C. CookieMonster attack
D. Mail bombing
-
Question 234:
You work as a Network Security Analyzer. You got a suspicious email while working on a forensic project. Now, you want to know the IP address of the sender so that you can analyze various information such as the actual location, domain information, operating system being used, contact information, etc. of the email sender with the help of various tools and resources. You also want to check whether this email is fake or real. You know that analysis of email headers is a good starting point in such cases. The email header of the suspicious email is given below:
What is the IP address of the sender of this email?
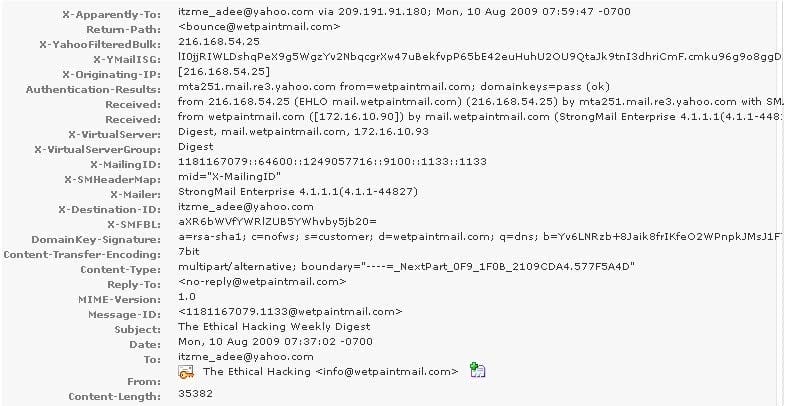
A. 209.191.91.180
B. 141.1.1.1
C. 172.16.10.90
D. 216.168.54.25
-
Question 235:
Andrew, a bachelor student of Faulkner University, creates a gmail account. He uses 'Faulkner' as the password for the gmail account. After a few days, he starts receiving a lot of e-mails stating that his gmail account has been hacked. He also finds that some of his important mails have been deleted by someone. Which of the following methods has the attacker used to crack Andrew's password?
Each correct answer represents a complete solution. Choose all that apply.
A. Brute force attack
B. Dictionary-based attack
C. Rainbow attack
D. Zero-day attack
E. Password guessing
F. Social engineering
G. Denial-of-service (DoS) attack
H. Buffer-overflow attack
-
Question 236:
Rick works as a Computer Forensic Investigator for BlueWells Inc. He has been informed that some confidential information is being leaked out by an employee of the company. Rick suspects that someone is sending the information through email. He checks the emails sent by some employees to other networks. Rick finds out that Sam, an employee of the Sales department, is continuously sending text files that contain special symbols, graphics, and signs. Rick suspects that Sam is using the Steganography technique to send data in a disguised form. Which of the following techniques is Sam using?
Each correct answer represents a part of the solution. Choose all that apply.
A. Technical steganography
B. Perceptual masking
C. Linguistic steganography
D. Text Semagrams
-
Question 237:
Which of the following password cracking attacks is implemented by calculating all the possible hashes for a set of characters?
A. Rainbow attack
B. Brute force attack
C. SQL injection attack
D. Dictionary attack
-
Question 238:
Which of the following Trojans is used by attackers to modify the Web browser settings?
A. WMA/TrojanDownloader.GetCodec
B. Win32/Pacex.Gen
C. Win32/FlyStudio
D. Trojan.Lodear
-
Question 239:
Which of the following is an example of a social engineering attack?
A. Phishing
B. Man-in-the-middle attack
C. Browser Sniffing
D. E-mail bombing
-
Question 240:
A firewall is a combination of hardware and software, used to provide security to a network. It is used to protect an internal network or intranet against unauthorized access from the Internet or other outside networks. It restricts inbound and outbound access and can analyze all traffic between an internal network and the Internet. Users can configure a firewall to pass or block packets from specific IP addresses and ports. Which of the following tools works as a firewall for the Linux 2.4 kernel?
A. Stunnel
B. IPChains
C. IPTables
D. OpenSSH
Related Exams:
112-51
EC-Council Certified Network Defense Essentials (NDE)212-77
EC-Council Certified Linux Security212-81
EC-Council Certified Encryption Specialist (ECES)212-82
EC-Council Certified Cybersecurity Technician (C|CT)212-89
EC-Council Certified Incident Handler (ECIH)312-38
EC-Council Certified Network Defender (CND)312-39
EC-Council Certified SOC Analyst (CSA)312-40
EC-Council Certified Cloud Security Engineer (CCSE)312-49
ECCouncil Computer Hacking Forensic Investigator (V9)312-49V10
EC-Council Certified Computer Hacking Forensic Investigator (V10)
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only EC-COUNCIL exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your ECSS exam preparations and EC-COUNCIL certification application, do not hesitate to visit our Vcedump.com to find your solutions here.