Exam Details
Exam Code
:ECSSExam Name
:EC-Council Certified Security Specialist (ECSS) v10Certification
:EC-COUNCIL CertificationsVendor
:EC-COUNCILTotal Questions
:337 Q&AsLast Updated
:Mar 24, 2025
EC-COUNCIL EC-COUNCIL Certifications ECSS Questions & Answers
-
Question 61:
A firewall is a combination of hardware and software, used to provide security to a network. It is used to protect an internal network or intranet against unauthorized access from the Internet or other outside networks. It restricts inbound and outbound access and can analyze all traffic between an internal network and the Internet. Users can configure a firewall to pass or block packets from specific IP addresses and ports. Which of the following tools works as a firewall for the Linux 2.4 kernel?
A. Stunnel
B. IPTables
C. OpenSSH
D. IPChains
-
Question 62:
Which of the following statements correctly defines a script kiddie?
A. He is an individual who breaks communication systems to perform hacking.
B. He is an individual who has lost respect and integrity as an employee in any organization.
C. He is an individual who uses hacking programs developed by others to attack information systems and spoil websites.
D. He is an individual who is an expert in various computer fields such as operating systems, networking, hardware, software, etc. and enjoys the mental challenge of decoding computer programs, solving network vulnerabilities and security threats, etc
-
Question 63:
Which of the following is allowed by a company to be addressed directly from the public network and is hardened to screen the rest of its network from security exposure?
A. bastion host
B. Intrusion detection system
C. A computer installed in the network and configured with sender reputation
D. Exchange ActiveSync
-
Question 64:
John works as a Desktop Technician for NetPerfect Inc. The company has a Windows-based network. For the last few days, the network of the company has become prone to the Man-in-the- Middle attack. John wants to send a confidential MS-Word file to his Manager through e-mail attachment. He wants to ensure that no one is able to open and understand the file's message except the Manager. Which of the following should John use to accomplish the task?
Each correct answer represents a part of the solution. Choose all that apply.
A. Format the file
B. Apply password to the file
C. Encryption
D. File Compression
-
Question 65:
Which of the following organizations is dedicated to computer security research and information sharing?
A. NIPC
B. FBI
C. Honeynet Project
D. IEEE
-
Question 66:
Rick works as a Computer Forensic Investigator for BlueWells Inc. He has been informed that some confidential information is being leaked out by an employee of the company. Rick suspects that someone is sending the information through email. He checks the emails sent by some employees to other networks. Rick finds out that Sam, an employee of the Sales department, is continuously sending text files that contain special symbols, graphics, and signs. Rick suspects that Sam is using the Steganography technique to send data in a disguised form. Which of the following techniques is Sam using?
Each correct answer represents a part of the solution. Choose all that apply.
A. Text Semagrams
B. Perceptual masking
C. Linguistic steganography
D. Technical steganography
-
Question 67:
You work as a Network Security Analyzer. You got a suspicious email while working on a forensic project. Now, you want to know the IP address of the sender so that you can analyze various information such as the actual location, domain information, operating system being used, contact information, etc. of the email sender with the help of various tools and resources. You also want to check whether this email is fake or real. You know that analysis of email headers is a good starting point in such cases. The email header of the suspicious email is given below:
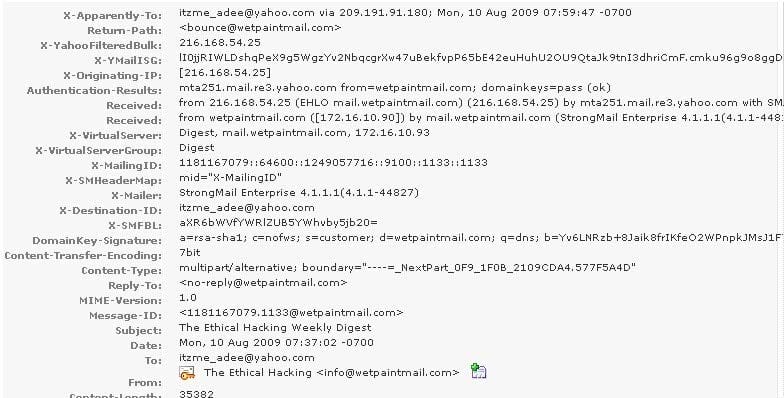
What is the IP address of the sender of this email?
A. 216.168.54.25
B. 209.191.91.180
C. 172.16.10.90
D. 141.1.1.1
-
Question 68:
Peter works as a Technical Representative in a CSIRT for SecureEnet Inc. His team is called to investigate the computer of an employee, who is suspected for classified data theft. Suspect's computer runs on Windows operating system.
Peter wants to collect data and evidences for further analysis. He knows that in Windows operating system, the data is searched in pre-defined steps for proper and efficient analysis. Which of the following is the correct order for searching data on a Windows based system?
A. Volatile data, file slack, registry, memory dumps, file system, system state backup, interne t traces
B. Volatile data, file slack, registry, system state backup, internet traces, file system, memory dumps
C. Volatile data, file slack, internet traces, registry, memory dumps, system state backup, file system
D. Volatile data, file slack, file system, registry, memory dumps, system state backup, interne t traces
-
Question 69:
Which of the following attacks is a man-in-the-middle exploit where a third party can gain HTTPS cookie data?
A. Cookie poisoning
B. CookieMonster attack
C. Cross site scripting attack
D. Smart Force Attack
-
Question 70:
Which of the following is an example of a low-interaction production honeypot that is developed and sold by the Swiss company Netsec?
A. Specter
B. KFSensor
C. Honeyd
D. ManTrap
Related Exams:
112-51
EC-Council Certified Network Defense Essentials (NDE)212-77
EC-Council Certified Linux Security212-81
EC-Council Certified Encryption Specialist (ECES)212-82
EC-Council Certified Cybersecurity Technician (C|CT)212-89
EC-Council Certified Incident Handler (ECIH)312-38
EC-Council Certified Network Defender (CND)312-39
EC-Council Certified SOC Analyst (CSA)312-40
EC-Council Certified Cloud Security Engineer (CCSE)312-49
ECCouncil Computer Hacking Forensic Investigator (V9)312-49V10
EC-Council Certified Computer Hacking Forensic Investigator (V10)
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only EC-COUNCIL exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your ECSS exam preparations and EC-COUNCIL certification application, do not hesitate to visit our Vcedump.com to find your solutions here.