Exam Details
Exam Code
:JN0-633Exam Name
:Security, Professional (JNCIP-SEC)Certification
:Juniper CertificationsVendor
:JuniperTotal Questions
:175 Q&AsLast Updated
:Mar 22, 2025
Juniper Juniper Certifications JN0-633 Questions & Answers
-
Question 21:
You are asked to configure your SRX Series device to support IDP SSL inspections for up to 6,000 concurrent HTTP sessions to a server within your network.
Which two statements are true in this scenario? (Choose two.)
A. You must add at least one PKI certificate.
B. Junos does not support more than 5000 sessions in this scenario.
C. You must enable SSL decoding.
D. You must enable SSL inspection.
-
Question 22:
Click the Exhibit button.
[edit security application-firewall]
user@host# show
rule-sets web {
rule one {
match {
dynamic-application junos:HTTP;
}
then {
permit;
}
}
default-rule {
reject; } }
What will happen to non-HTTP traffic that matches the application-firewall policy shown in the exhibit?
A. It will be denied because this is a blacklist policy.
B. It will be dropped and an error will be sent to the source.
C. It will be silently dropped.
D. It will be allowed because this is a whitelist policy.
-
Question 23:
The IPsec VPN on your SRX Series device establishes both the Phase 1 and Phase 2 security associations. Users are able to pass traffic through the VPN. During peak VPN usage times, users complain about decreased performance. Network connections outside of the VPN are not seriously impacted.
Which two actions will resolve the problem? (Choose two.)
A. Lower the MTU size on the interface to reduce the likelihood of packet fragmentation.
B. Verify that NAT-T is not disabled in the properties of the phase 1 gateway.
C. Lower the MSS setting in the security flow stanza for IPsec VPNs.
D. Verify that the PKI certificate used to establish the VPN is being properly verified using either the CPL or OCSP.
-
Question 24:
Your management has a specific set of Web-based applications that certain employees are allowed to use.
Which two SRX Series device features would be used to accomplish this task? (Choose two.)
A. UserFW
B. IDP
C. AppFW
D. firewall filter
-
Question 25:
Click the Exhibit button.
[edit security idp-policy test] user@host# show rulebase-ips {
rule R3 {
match {
source-address any;
destination-address any;
attacks {
predefined-attacks FTP:USER:ROOT;
}
}
then {
action {
recommended;
}
}
terminal;
}
rule R4 {
match {
source-address any;
destination-address any;
attacks {
predefined-attacks HTTP:HOTMAIL:FILE-UPLOAD;
}
}
then {
action { recommended; } } } }
You have just committed the new IDP policy shown in the exhibit. However, you notice no action is taken on traffic matching the R4 IDP rule. Which two actions will resolve the problem? (Choose two.)
A. Change the R4 rule to match on a predefined attack group.
B. Insert the R4 rule above the R3 rule.
C. Delete the terminal statement from the R3 rule.
D. Change the IPS rulebase to an exempt rulebase.
-
Question 26:
Which feature is used for layer 2 bridging on an SRX Series device?
A. route mode
B. packet mode
C. transparent mode
D. MPLS mode
-
Question 27:
You are performing AppSecure traffic processing to enforce AppFW.
What happens when traffic matching an established security session is newly detected as a different application?
A. The security processing facility of the data plane re-examines the whitelist or blacklist referenced in the security policy to see if the new application is permitted.
B. The newly detected application will not be permitted and session will be torn down unless a specific match exists against the exempt rulebase.
C. Zone-based firewall rules will be re-parsed to determine if a rule exists that permits the newly detected application.
D. The application will not be permitted if doing so would violate the session limit in the screen properties applied to that zone.
-
Question 28:
How does the SRX5800, in transparent mode, signal failover to the connected switches?
A. It initiates spanning-tree BPDUs.
B. It sends out gratuitous ARPs.
C. It flaps the impaired interfaces.
D. It uses an IP address monitoring configuration.
-
Question 29:
Click the Exhibit button.
[edit]
user@host# show interfaces
ge-0/0/1 { unit 0 { family bridge { interface-mode access; vlan-id 20; } }
}
ge-0/0/10 { unit 0 { family bridge { interface-mode access; vlan-id 20; }
} }
[edit]
user@host# show bridge-domains
d1 {
domain-type bridge; vlan-id 20; }
[edit]
user@host# show security flow bridge
[edit]
user@host# show security zones
security-zone 12 {
host-inbound-traffic {
system-services {
any-service;
}
}
interfaces {
ge-0/0/1.0; ge-0/0/10.0; } }
Referring to the exhibit, which statement is true?
A. Packets sent tom the SRX Series device are sent to the RE.
B. Packets sent to the SRX Series device are discarded.
C. Only frames that have a VLAN ID of 20 are accepted.
D. Only frames that do not have any VLAN tags are accepted.
-
Question 30:
Click the Exhibit button.
Traffic is being sent from Host-1 to Host-2 through an IPsec VPN. In this process, SRX-2 is using NAT to change the destination address of Host-2 from 192.168.1.1 to 10.60.60.1 SRX-1 uses the 172.31.50.1 address for its tunnel endpoint and SRX-2 uses the 10.10.50.1 address for its tunnel endpoint.
Referring to the exhibit, which statement is true?
Exhibit:
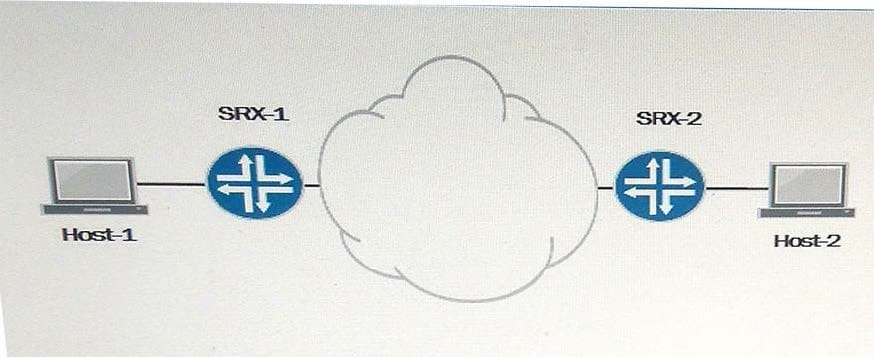
A. The security policy on SRX-2 must permit traffic from the 172.31.50.1 destination address.
B. The security policy on SRX-2 must permit traffic from the 10.10.50.1destination address.
C. The security policy on SRX-2 must permit traffic from the 10.60.60.1 destination address.
D. The security policy on SRX-2 must permit traffic from the 192.168.1.1destination address.
Related Exams:
JN0-102
Internet Associate, Junos(JNCIA-Junos)JN0-104
Junos, Associate (JNCIA-Junos)JN0-105
Junos, Associate (JNCIA-Junos)JN0-1101
Juniper Networks Certified Design Associate (JNCDA)JN0-130
Juniper networks Certified internet specialist.e(jncis-e)JN0-1301
Data Center Design, Specialist (JNCDS-DC)JN0-1302
Data Center Design Specialist (JNCDS-DC)JN0-1331
Security Design, Specialist (JNCDS-SEC)JN0-1332
Security Design, Specialist (JNCDS-SEC)JN0-1361
Service Provider Design Specialist (JNCDS-SP)
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only Juniper exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your JN0-633 exam preparations and Juniper certification application, do not hesitate to visit our Vcedump.com to find your solutions here.