Exam Details
Exam Code
:NS0-155Exam Name
:NetApp Certified 7-Mode Data AdministratorCertification
:NetApp CertificationsVendor
:NetAppTotal Questions
:189 Q&AsLast Updated
:Apr 15, 2025
NetApp NetApp Certifications NS0-155 Questions & Answers
-
Question 141:
You want to create an automated test environment that performs a single file SnapRestore time you run the procedure, however, SnapRestore prompts you to confirm your decision to revert the file. How can you automate this step?
A. Use the -f option with the snap restore command.
B. Enable the options snaprestore_noprompts enable = on option.
C. These prompts are for data protection and auditing and cannot be overridden.
D. Enter the priv set advanced mode on the storage system and prompt will not appear.
-
Question 142:
The two copies SyncMirror volume are called ____________, which are physical copies of the same file system and consist of one or more RAID groups.
A. Snapshot copies
B. Aggregates
C. Plexes
D. Volumes
-
Question 143:
When using MetroCluster in a forced takeover mode, identify two methods for restricting access to the disaster site node. (Choose two)
A. Use manual fencing
B. Use the cf giveback f command.
C. Use the cf forcetakeover d command.
D. Turn off power to the disaster site node.
E. Isolate the failed node from the surviving node.
-
Question 144:
Which command disables client access to Snapshot copies on a volume called flexvoll?
A. cifs shares change flxvoll nosnap
B. snap access flexvoll off
C. vol options flexvoll nonsnapdir on
D. vol options flexvoll snapdir off
E. vol options flexvoll snapdir on
-
Question 145:
What security mechanism can an administrator use on an OSSV client to use permissions allowing backup to a SnapVault secondary system?
A. MD5 authentication between SnapVault primary and secondary, with changeable password
B. Contents inside file called access and located in OSSV /snapvault/etc
C. QSM access list modifiable via svconfigurator
D. Via /etc/hosts.equiv file
-
Question 146:
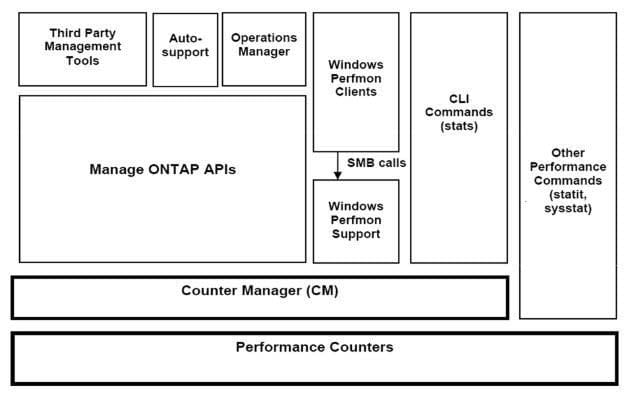
Which three tools present statistics from the Data ONTAP counter manager? (Choose three)
A. Operations manager
B. Window perfmon
C. Sysstat
D. Stats
-
Question 147:
Which three protocols can coexist on a NetApp storage system? (Choose three)
A. DAFS
B. CIFS
C. DFS
D. FCP
E. NFS
-
Question 148:
Which command on the storage system allows you to display statistics on the performance of system resource such as CPU, NVRAM, network interfaces, and disks?
A. netstat
B. netdiag
C. pktt
D. sysstat
-
Question 149:
An iSCSI or FC SAN implementation provides ____________ access to LUNs.
A. VLD
B. VIIP
C. File
D. Block
-
Question 150:
Which set of protocols provide block-level access to NetApp storage?
A. SNA and RPC
B. iSCSI and FCP
C. HTTP and FTP
D. CIFS and NFS
Related Exams:
NS0-002
NetApp Certified Technology Associate - NCSA - HCNS0-003
NetApp Certified Technology AssociateNS0-004
NetApp Certified Technology Solutions ProfessionalNS0-093
NetApp Accredited Hardware Support EngineerNS0-101
NetApp Accredited Sales ProfessionalNS0-111
Network Appliance Storage AssociateNS0-120
Data ONTAP AdvancedNS0-121
Network Appliance Data ONTAP Advanced Exam 7GNS0-130
Storage Professional Data ProtectionNS0-131
Network Appliance Data Protection Exam 7G
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only NetApp exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your NS0-155 exam preparations and NetApp certification application, do not hesitate to visit our Vcedump.com to find your solutions here.