Exam Details
Exam Code
:ST0-237Exam Name
:Symantec Data Loss Prevention 12 Technical AssessmentCertification
:Symantec Certified Security programVendor
:SymantecTotal Questions
:237 Q&AsLast Updated
:Apr 16, 2025
Symantec Symantec Certified Security program ST0-237 Questions & Answers
-
Question 291:
Consider a situation where you run the vxdmpadm start restore command and encounter an error message "VxVM vxdmpadm ERROR V-5-1-3243 The VxVM restore daemon is already running"
How will you solve this error?
A. Stop vxdmpadm and restart vxdmpadm.
B. Stop vxdmpadm and start vxdarestore.
C. Stop vxdmpadm and reboot the system.
D. Restart the all the VxVM daemons.
-
Question 292:
Which version of Oracle does Symantec Data Loss Prevention version 12.0 require for new installations or upgrading from 11.x to 12.0?
A. 10.2.0.1
B. 10.2.0.4
C. 11.2.0.2
D. 11.2.0.3
-
Question 293:
A user is unable to log in as sysadmin. The Data Loss Prevention system is configured to use Active Directory authentication. The user is a member of two roles: sysadmin and remediator. How should the user log in to the user interface in the sysadmin role?
A. sysadmin\username@domain
B. sysadmin\username
C. domain\username
D. username\sysadmin
-
Question 294:
When attempting to log in as administrator to the UI, the administrator receives a login error:
Invalid Username/Password or Disabled Account
The DBA verifies the account is enabled. The information provided for the environment only includes the DLP protect database username and password as well as a username and password called Sys Admin \Admin.
How should the administrator change the built-in 'Administrator' password?
A. log in to the Enforce UI as the Sys Admin account and go to System > Login Management > DLP Users and reset the administrator password
B. extract the administrator password from the DatabasePassword.properties file
C. update the PasswordEnforcement.properties file with a new administrator password
D. use the AdminPasswordReset utility to update the password
-
Question 295:
How should an administrator determine which Database version is running?
A. Run the command select database version from database;
B. Right click on database folder and select version
C. Run the command select * from v$version;
D. Look in add/remove programs for the database program
-
Question 296:
Which structure records are stored in the private region? (Each correct answer presents part of the solution. Select three.)
A. Disk group configuration
B. Disk and disk group ID
C. File system metadata
D. Disk group kernel log
E. Partition tables
-
Question 297:
Refer to the exhibit.
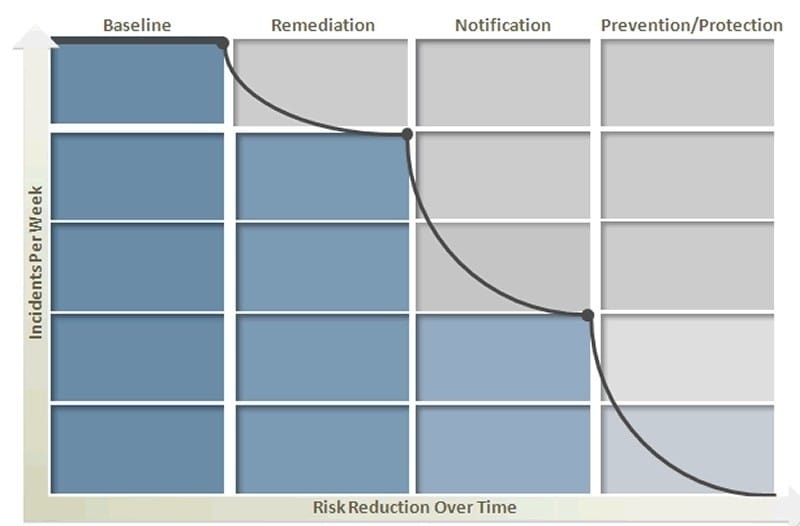
Symantec Data Loss Prevention's four phases of risk reduction model provides a blueprint for identifying and remediating key risk areas without disrupting legitimate business activity. What occurs during the notification phase?
A. Notification helps define confidential information and assign appropriate levels of protection to it using classifications.
B. On-Screen Pop-ups compare existing company information protection polices to best practices.
C. Notification helps develop a plan for integrating appropriate data security practices.
D. Automated sender notification educates employees in real-time about company policy violations.
-
Question 298:
The chief information security officer (CISO) is responsible for overall risk reduction and develops high- level initiatives to respond to security risk trends. Which report will be useful to the CISO?
A. all high severity incidents that have occurred during the last week
B. all dismissed incidents violating a specific policy marked as false positive
C. all incidents from the previous month summarized by business units and policy
D. all new incidents that have been generated by a specific business unit during the last week
-
Question 299:
Refer to the exhibit.

Symantec Data Loss Prevention's four phases of risk reduction model provides a blueprint for identifying and remediating key risk areas without disrupting legitimate business activity. According to this model, which activity should occur during the baseline phase?
A. Monitor incidents and tune the policy to reduce false positives
B. Define and build the incident response team
C. Establish business metrics and begin sending reports to business unit stakeholders
D. Test policies to ensure that blocking actions minimize business process disruptions
-
Question 300:
What is the most efficient policy so that incidents are generated only when a specific user under investigation sends encrypted files?
A. a policy that has one condition
B. a policy that has one exception
C. a policy that has two conditions
D. a policy that has two exceptions
Related Exams:
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only Symantec exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your ST0-237 exam preparations and Symantec certification application, do not hesitate to visit our Vcedump.com to find your solutions here.