Exam Details
Exam Code
:ST0-237Exam Name
:Symantec Data Loss Prevention 12 Technical AssessmentCertification
:Symantec Certified Security programVendor
:SymantecTotal Questions
:237 Q&AsLast Updated
:Apr 16, 2025
Symantec Symantec Certified Security program ST0-237 Questions & Answers
-
Question 321:
What is the default limit to the number of subdisks that can be attached to a single plex?
A. 1024
B. 2048
C. 4096
D. Unlimited
-
Question 322:
A DLP administrator is writing one policy to block sensitive data from being copied to removable media. The administrator is applying two response rules to the policy: 'Endpoint Prevent: Notify' and 'Endpoint Prevent: Block'.
Why are some copies blocked while others are only notified?
A. There are different conditions for the different response actions
B. The monitor and ignore filters are defined incorrectly
C. The DLP administrator needs to fine tune the throttling options
D. The Directory Group Matching (DGM) profile has users in different groups
-
Question 323:
You have a system that has two disks--disk01 and disk02, which are mapped into the system configuration during boot as disks c0t0d0s2 and c0t1d0s2, respectively. A failure has caused disk01 to become detached. What would you do to view the status of the failed disk01?
A. Use the vxdg list command
B. Use the vxdg s list command
C. Use the vxprint command
D. Use the vxdisk list command
-
Question 324:
An administrator is applying a newly created agent configuration to an Endpoint server. Upon inspection, the new configuration is unassigned in the Endpoint Server Details. What is a possible cause for the new configuration failing to be assigned?
A. the system default settings were saved to the new agent configuration
B. the server that the new agent configuration was applied to needs to be recycled
C. the new agent configuration was saved without applying it to the Endpoint server
D. the new agent configuration was copied and modified from the default agent configuration
-
Question 325:
You have encapsulated the disk for swap partitions and created mirrors under the VxVM control. Which files in /etc get modified when the root disk is encapsulated?
A. vfstab and file system
B. vfstab and rootdisk
C. mnttab and file system
D. volboot and file system
-
Question 326:
A DLP administrator is attempting to use Encryption Insight to detect confidential information in encrypted files but has been unsuccessful. It is determined that the process was unable to retrieve the appropriate PGP key because the user key was using the incorrect encryption mode. What is the correct encryption mode that must be used by the user key?
A. Client Key Mode
B. Server Key Mode
C. Client Server Key Mode
D. Guarded Key Mode
-
Question 327:
While performing a VxVM operation, you discover that the disk group configuration has become corrupt. You want to check the changes in the VxVM configuration data and automatically record any configuration changes that occur. What would you do in this situation?
A. Use the vxconfigd daemon to monitor changes to the VxVM configuration.
B. Use the vxrelocd daemon to monitor monitors changes to the VxVM configuration.
C. Use the vxconfigbackupd daemon to monitors changes to the VxVM configuration.
D. Use vxdctl daemon to monitors changes to the VxVM configuration.
-
Question 328:
A DLP administrator has determined that a Network Discover server is unable to scan a remote file server. Which action should the administrator take to successfully scan the remote file server?
A. restart the discover scan
B. verify that the target file server is a Windows 2008 server
C. use the fully qualified name (FQDN) of the server
D. verify that the file server has .NET services running
-
Question 329:
Refer to the exhibit.
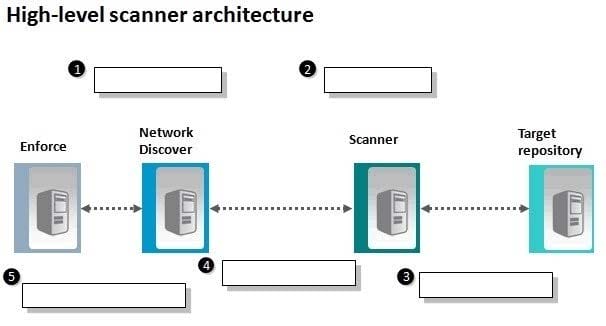
An administrator needs to implement the use of a scanner, but is unfamiliar with the general, high-level process associated with scanners. Which action occurs in step 3?
A. the scanner reviews and confirms configuration parameters
B. the scanner connects to target and reads the content and metadata
C. the scanner process is started by a user or scheduled event
D. the scanner packages filtered content and posts the data to Discover server
-
Question 330:
How should an administrator apply a policy to Network Discover scans?
A. Assign the policy group to the scan target
B. Choose the correct policy in the scan target
C. Assign the policy to the Network Discover Server
D. Choose the correct scan target in the policy destination
Related Exams:
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only Symantec exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your ST0-237 exam preparations and Symantec certification application, do not hesitate to visit our Vcedump.com to find your solutions here.