Exam Details
Exam Code
:VCP550Exam Name
:VMware Certified Professional - Data Center VirtualizationCertification
:VMware CertificationsVendor
:VMwareTotal Questions
:267 Q&AsLast Updated
:Dec 16, 2024
VMware VMware Certifications VCP550 Questions & Answers
-
Question 51:
A customer needs to select an appropriate Path Selection Policy (PSP) for their storage array. There is no requirement for a preferred path. The policy should not select a new path unless the current one fails. Which PSP meets the requirement?
A. Fixed
B. Round Robin
C. Most Recently Used
D. Asymmetric Logical Unit Access
-
Question 52:
An administrator needs to unmount a datastore that is also used for HA storage heartbeats.
What is the least disruptive method for an administrator to perform this activity on a slave HA host?
A. On the Datastore Heartbeating tab, unmount the datastore normally and confirm a new datastore has been selected.
B. On the Datastore Heartbeating tab, specify an alternate datastore, then unmount the datastore normally.
C. Disable HA datastore heartbeats, then unmount the datastore.
D. Reduce the number of heartbeat datastores, then remove the datastore from the heartbeat list.
-
Question 53:
When deploying two sibling resource pools (RP1 and RP2), an administrator needs to make all resources in RP1 available to virtual machines in RP2. Which configuration should the administrator use to meet this requirement?
A. Set the Reservation of RP2 to 0
B. Set the Reservation of RP1 to 0
C. Set the Limit of RP1 to Unlimited
D. Set the Limit of RP2 to Unlimited
-
Question 54:
Which controller is recommended for high disk I/O workloads?
A. BusLogic Parallel
B. LSI Logic Parallel
C. LSI Logic SAS
D. VMware Paravirtual
-
Question 55:
An administrator needs to migrate a company's physical servers to virtual servers and deploy into the ESXi 5.x cluster. During the process of converting to a virtual machine, the administrator needs to reduce the size of the disks. Which method should the administrator use to meet this requirement?
A. Use VMware Converter hot cloning with volume-based cloning at the file level
B. Shut down the physical server and use VMware Converter cold cloning with volume-based cloning at the block level
C. Use VMware Converter hot cloning with volume-based cloning at the block level
D. Shut down the physical server and use VMware Converter cold cloning with volume-based cloning at the file level
-
Question 56:
An administrator is deploying vSphere using a NAS device as the shared storage system.
The administrator has already created a VMkernel port, enabled the NFS client, and configured a mount point accessible to the hosts.
Which additional configuration is required before the datastore can be used to create virtual machines?
A. The ESXi hosts must have root access to the datastore.
B. The NAS must support NFS version 4.
C. Port binding must be configured on the VMkernel port.
D. The MTU on the VMkernel port must be set to 9000.
-
Question 57:
An administrator is considering using NPIV to assign WWNs to virtual machines. Virtual machine portability is a major concern. Why would NPIV be inappropriate for this deployment?
A. Virtual machines using NPIV must use DirectPath I/O.
B. Storage vMotion is not supported using NPIV.
C. vMotion is not supported using NPIV.
D. Enabling NPIV requires SR-IOV supported hardware.
-
Question 58:
An administrator of a secure environment needs to add an iSCSI target to a new ESXi host using the vSphere client. The administrator has configured discovery and performed a rescan operation, but the iSCSI target does NOT appear.
Which action should the administrator take for the target to appear in the vSphere client?
A. Configure appropriate CHAP authentication settings
B. Bind a VMkernel port to the iSCSI initiator
C. Configure Jumbo Frames prior to adding iSCSI targets
D. Enable iSCSI in a vSphere Distributed Switch configuration
-
Question 59:
-- Exhibit -
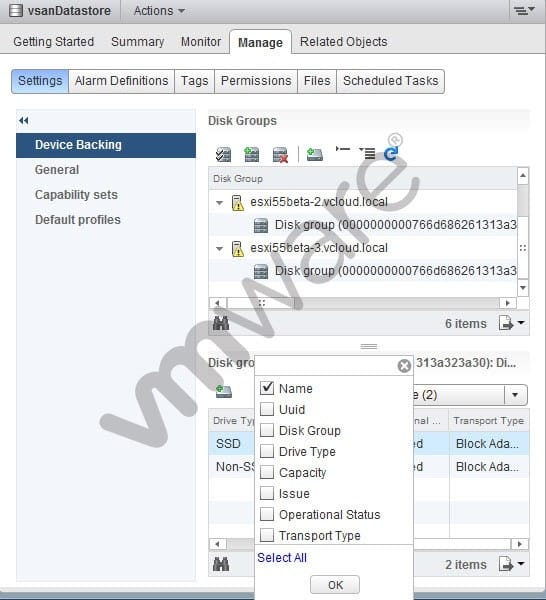
-- Exhibit -Which field should an administrator add to a Virtual SAN Disk Group under the Device Backing settings to monitor the health of disks in the Disk Group?
A. Issue
B. Operational Status
C. Capacity
D. Transport Type
-
Question 60:
A vSphere administrator needs to perform packet tracing from a Linux virtual machine. The virtual machine is attached to a vSphere Standard Switch configured with several VLANs. Which approach could the administrator use to configure the network to capture all traffic from the Linux virtual machine?
A. Configure the virtual switch with VLAN Trunking and specify each VLANs on the port group containing the virtual machine.
B. Configure a vSphere Distributed Switch with VLAN Trunking. Create a port group and configure it with Promiscuous Mode. Connect the virtual machine to that port group.
C. Configure the port group containing the virtual machine for Promiscuous Mode. Set the port group to use VLAN 1.
D. Configure a vSphere Distributed Switch with VLAN Trunking. Connect the virtual machine to the switch and enable Port Mirroring on the port group containing the virtual machine.
Related Exams:
1V0-21.20
Associate VMware Data Center Virtualization1V0-31.21
Associate VMware Cloud Management and Automation1V0-41.20
Associate VMware Network Virtualization1V0-61.21
Associate VMware Digital Workspace1V0-71.21
Associate VMware Application Modernization1V0-81.20
Associate VMware Security2V0-21.20
Professional VMware vSphere 7.x2V0-21.23
VMware vSphere 8.x Professional2V0-31.21
Professional VMware vRealize Automation 8.32V0-31.23
VMware Aria Automation 8.10 Professional
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only VMware exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your VCP550 exam preparations and VMware certification application, do not hesitate to visit our Vcedump.com to find your solutions here.