Exam Details
Exam Code
:AZ-104Exam Name
:Microsoft Azure AdministratorCertification
:Microsoft CertificationsVendor
:MicrosoftTotal Questions
:361 Q&AsLast Updated
:Mar 23, 2025
Microsoft Microsoft Certifications AZ-104 Questions & Answers
-
Question 161:
Note: This question is part of a series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals. Some question sets might have more than one correct solution, while others might not have a correct solution.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
You have an Azure subscription that contains the following users in an Azure Active Directory tenant named contoso.onmicrosoft.com:
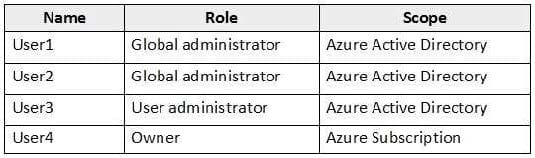
User1 creates a new Azure Active Directory tenant named external.contoso.onmicrosoft.com.
You need to create new user accounts in external.contoso.onmicrosoft.com.
Solution: You instruct User2 to create the user accounts.
Does that meet the goal?
A. Yes
B. No
-
Question 162:
You have a hybrid infrastructure that contains an Azure Active Directory (Azure AD) tenant named contoso.onmicrosoft.com. The tenant contains the users shown in the following table.
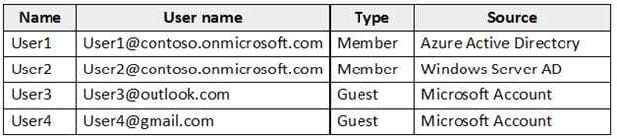
You plan to share a cloud resource to the All Users group. You need to ensure that User1, User2, User3, and User4 can connect successfully to the cloud resource.
What should you do first?
A. Create a user account of the member type for User4.
B. Create a user account of the member type for User3.
C. Modify the Directory-wide Groups settings.
D. Modify the External collaboration settings.
-
Question 163:
You have an Azure Active Directory (Azure AD) tenant named contoso.com. Multi-factor authentication (MFA) is enabled for all users.
You need to provide users with the ability to bypass MFA for 10 days on devices to which they have successfully signed in by using MFA.
What should you do?
A. From the multi-factor authentication page, configure the users' settings.
B. From Azure AD, create a conditional access policy.
C. From the multi-factor authentication page, configure the service settings.
D. From the MFA blade in Azure AD, configure the MFA Server settings.
-
Question 164:
You have an Azure subscription that contains the resources shown in the following table.
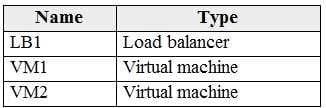
VM1 and VM2 run a website that is configured as shown in the following table.

LB1 is configured to balance requests to VM1 and VM2.
You configure a health probe as shown in the exhibit. (Click the Exhibit tab.)
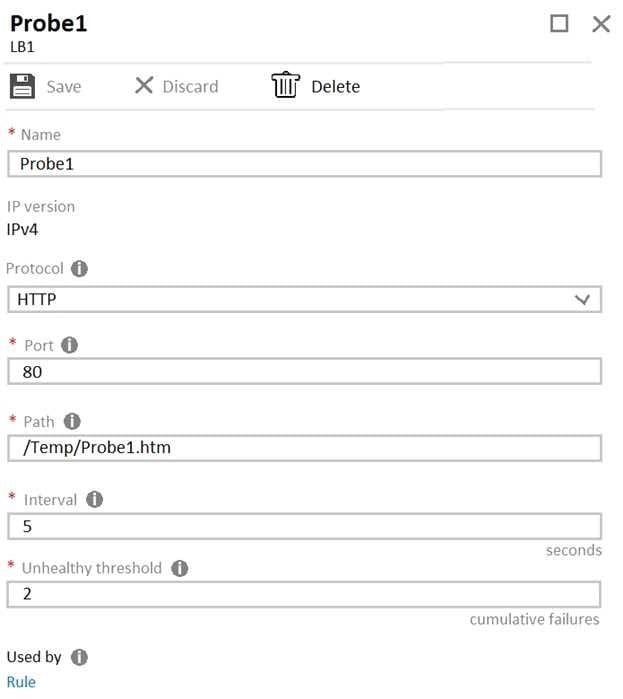
You need to ensure that the health probe functions correctly. What should you do?
A. On LB1, change the Unhealthy threshold to 65536.
B. On LB1, change the port to 8080.
C. On VM1 and VM2, create a file named Probe1.htm in the C:\intepub\wwwroot\Temp folder.
D. On VM1 and VM2, create a file named Probe1.htm in the C:\intepub\wwwroot\SiteA\Temp folder.
-
Question 165:
You have a Microsoft 365 tenant and an Azure Active Directory (Azure AD) tenant named contoso.com.
You plan to grant three users named User1, User2, and User3 access to a temporary Microsoft SharePoint document library named Library1.
You need to create groups for the users. The solution must ensure that the groups are deleted automatically after 180 days.
Which two groups should you create? Each correct answer presents a complete solution.
NOTE: Each correct selection is worth one point.
A. a Security group that uses the Assigned membership type
B. an Office 365 group that uses the Assigned membership type
C. an Office 365 group that uses the Dynamic User membership type
D. a Security group that uses the Dynamic User membership type
E. a Security group that uses the Dynamic Device membership type
-
Question 166:
Note: This question is part of a series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals. Some question sets might have more than one correct solution, while others might not have a correct solution.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
You have an Azure subscription that contains the following resources:
1.
A virtual network that has a subnet named Subnet1
2.
Two network security groups (NSGs) named NSG-VM1 and NSG-Subnet1
3.
A virtual machine named VM1 that has the required Windows Server configurations to allow Remote Desktop connections
NSG-Subnet1 has the default inbound security rules only.
NSG-VM1 has the default inbound security rules and the following custom inbound security rule:
1.
Priority: 100
2.
Source: Any
3.
Source port range: *
4.
Destination: *
5.
Destination port range: 3389
6.
Protocol: UDP
7.
Action: Allow
VM1 has a public IP address and is connected to Subnet1. NSG-VM1 is associated to the network interface of VM1. NSG-Subnet1 is associated to Subnet1.
You need to be able to establish Remote Desktop connections from the internet to VM1.
Solution: You add an inbound security rule to NSG-Subnet1 and NSG-VM1 that allows connections from the internet source to the VirtualNetwork destination for port range 3389 and uses the TCP protocol.
Does this meet the goal?
A. Yes
B. No
-
Question 167:
You create an Azure VM named VM1 that runs Windows Server 2019. VM1 is configured as shown in the exhibit. (Click the Exhibit tab.)
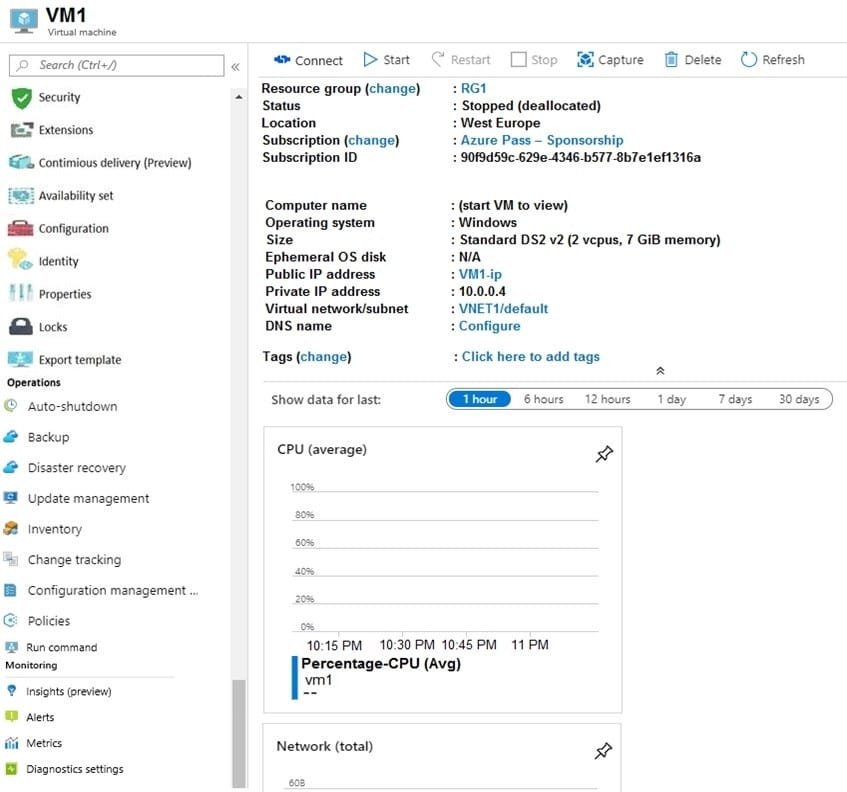
You need to enable Desired State Configuration for VM1.
What should you do first?
A. Configure a DNS name for VM1.
B. Start VM1.
C. Connect to VM1.
D. Capture a snapshot of VM1.
-
Question 168:
Note: This question is part of a series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals. Some question sets might
have more than one correct solution, while others might not have a correct solution. After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen. You have an Azure subscription that contains the following resources:
1.
A virtual network that has a subnet named Subnet1
2.
Two network security groups (NSGs) named NSG-VM1 and NSG-Subnet1
3.
A virtual machine named VM1 that has the required Windows Server configurations to allow Remote Desktop connections
4.
NSG-Subnet1 has the default inbound security rules only.
NSG-VM1 has the default inbound security rules and the following custom inbound security rule:
1.
Priority: 100
2.
Source: Any
3.
Source port range: *
4.
Destination: *
5.
Destination port range: 3389
6.
Protocol: UDP
7.
Action: Allow
VM1 connects to Subnet1. NSG1-VM1 is associated to the network interface of VM1. NSG-Subnet1 is associated to Subnet1. You need to be able to establish Remote Desktop connections from the internet to VM1.
Solution: You modify the custom rule for NSG-VM1 to use the internet as a source and TCP as a protocol. Does this meet the goal?
A. Yes
B. No
-
Question 169:
Note: This question is part of a series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals. Some question sets might have more than one correct solution, while others might not have a correct solution.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
You have an Azure subscription that contains the following resources:
1.
A virtual network that has a subnet named Subnet1
2.
Two network security groups (NSGs) named NSG-VM1 and NSG-Subnet1
3.
A virtual machine named VM1 that has the required Windows Server configurations to allow Remote Desktop connections
NSG-Subnet1 has the default inbound security rules only.
NSG-VM1 has the default inbound security rules and the following custom inbound security rule:
1.
Priority: 100
2.
Source: Any
3.
Source port range: *
4.
Destination: *
5.
Destination port range: 3389
6.
Protocol: UDP
7.
Action: Allow
VM1 has a public IP address and is connected to Subnet1. NSG-VM1 is associated to the network interface of VM1. NSG-Subnet1 is associated to Subnet1.
You need to be able to establish Remote Desktop connections from the internet to VM1.
Solution: You add an inbound security rule to NSG-Subnet1 that allows connections from the Any source to the *destination for port range 3389 and uses the TCP protocol. You remove NSG-VM1 from the network interface of VM1.
Does this meet the goal?
A. Yes
B. No
-
Question 170:
You have an Azure subscription named Subscription1 that contains the resources shown in the following table.
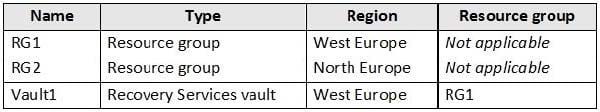
You create virtual machines in Subscription1 as shown in the following table.
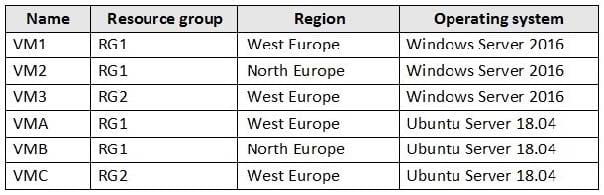
You plan to use Vault1 for the backup of as many virtual machines as possible.
Which virtual machines can be backed up to Vault1?
A. VM1, VM3, VMA, and VMC only
B. VM1 and VM3 only
C. VM1, VM2, VM3, VMA, VMB, and VMC
D. VM1 only
E. VM3 and VMC only
Related Exams:
62-193
Technology Literacy for Educators70-243
Administering and Deploying System Center 2012 Configuration Manager70-355
Universal Windows Platform – App Data, Services, and Coding Patterns77-420
Excel 201377-427
Excel 2013 Expert Part One77-725
Word 2016 Core Document Creation, Collaboration and Communication77-726
Word 2016 Expert Creating Documents for Effective Communication77-727
Excel 2016 Core Data Analysis, Manipulation, and Presentation77-728
Excel 2016 Expert: Interpreting Data for Insights77-731
Outlook 2016 Core Communication, Collaboration and Email Skills
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only Microsoft exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your AZ-104 exam preparations and Microsoft certification application, do not hesitate to visit our Vcedump.com to find your solutions here.