Exam Details
Exam Code
:AZ-700Exam Name
:Designing and Implementing Microsoft Azure Networking SolutionsCertification
:Microsoft CertificationsVendor
:MicrosoftTotal Questions
:390 Q&AsLast Updated
:Mar 31, 2025
Microsoft Microsoft Certifications AZ-700 Questions & Answers
-
Question 121:
You have an Azure application gateway configured for a single website that is available at https://www.contoso.com.
The application gateway contains one backend pool and one rule. The backend pool contains two backend servers. Each backend server has an additional website that is available on port 8080.
You need to ensure that if port 8080 is unavailable on a backend server, all the traffic for https://www.contoso.com is redirected to the other backend server.
What should you do?
A. Create a health probe
B. Add a new rule
C. Change the port on the listener
D. Add a new listener
-
Question 122:
You have deployed a virtual named VM1 that connects over port number 4444 to an application named App1.
App1 is hosted in your on-premises environment.
You discover that VM1 is not able to connect to App1.
You need to verify whether the issue relates to the network security groups.
What should you use?
A. Diagnostic settings in Azure Monitor
B. Diagnose and solve problems in Traffic Manager Profiles
C. The security recommendations in Azure Advisor
D. IP flow verify in Azure Network Watcher
-
Question 123:
You have two Azure virtual networks named VNet1 and VNet2.
VNet1 contains an Azure virtual machine named VM1.
VNet2 contains an Azure virtual machine named VM2.
VM1 hosts a frontend application that connects to VM2 to retrieve data. Users report that the frontend application is slower than usual. You need to view the average round-trip time (RTT) of the packets from VM1 to VM2.
Which Azure Network Watcher feature should you use?
A. IP flow verify
B. Connection troubleshoot
C. Connection monitor
D. NSG flow logs
-
Question 124:
You have an Azure virtual network named Hub1.
Hub1 connects to an on-premises network by using a Site-to-Site VPN connection.
You created an Azure Virtual network named Spoke1.
You are implementing peering between Hub1 and Spoke1.
You need to ensure that a virtual machine connected to Spoke1 can connect to the on-premises network through Hub1.
How should you complete the PowerShell script?
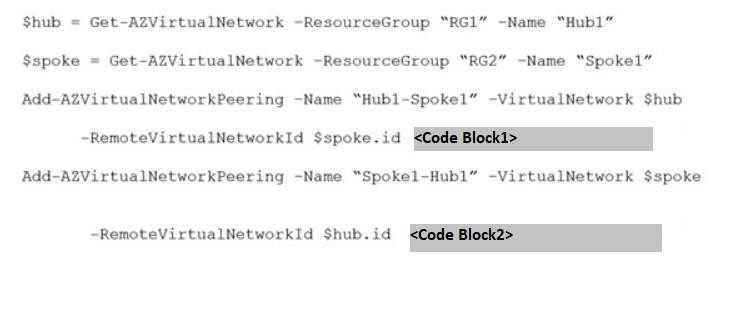
A. Code Block1: -AllowForwardedTraffic
B. Code Block1: -AllowGatewayTransit
C. Code Block1: -UseRemoteGateways
D. Code Block2: -AllowForwardedTraffic
E. Code Block2: -AllowGatewayTransit
F. Code Block2: -UseRemoteGateways
-
Question 125:
You plan to create a Point-to-Site (P2S) VPN connection for a remote user to connect to your Azure environment. Which of the following protocols should you use?
A. OpenVPN
B. IPSec
C. Secure Socket Tunneling Protocol (SSTP)
D. IKEv2 VPN
E. FTP
-
Question 126:
Which virtual machines can VM1 ping successfully?
A. VM2 only
B. VM2 and VM4 only
C. VM2, VM3 and VM4 only
D. VM2, VM3, VM4 and VM5 only
-
Question 127:
You have an Azure Front Door instance named FD1 that is protected by using Azure Web Application Firewall (WAF).
FD1 uses a frontend host named app1.healthengine.com to provide access to Azure web apps hosted in the East US Azure region and the West US Azure region.
You need to configure FD1 to block requests to app1.healthengine.com from all countries other than the United States.
What should you include in the WAF policy?
A. a frontend host association
B. a managed rule set
C. a custom rule that uses a rate limit rule
D. a custom rule that uses a match rule
-
Question 128:
Your company has an Azure virtual network named Vnet1 that uses an IP address space of 192.168.0.0/20.
Vnet1 contains a subnet named Subnet1 that uses an IP address space of 192.168.0.0/24. You create an IPv6 address range to Vnet1 by using a CIDR suffix of /48. You need to enable the virtual machines on Subnet1 to communicate with
each other by using IPv6 addresses assigned by the company.
The solution must minimize the number of additional IPv4 addresses.
What should you do for each virtual machine?
A. Create an additional IP configuration
B. Create an additional NIC
C. Create a public IPv6 address
-
Question 129:
You need to deploy an Azure Load Balancer that support outbound traffic rules. Which SKU should you use? Costs must be minimal.
A. Basic
B. Standard
-
Question 130:
You have an Azure subscription that contains the following resources:
A virtual network named Vnet1
A subnet named Subnet1 in Vnet1
A virtual machine named VM1 that connects to Subnet1
Three storage accounts named storage1, storage2, and storage3
You need to ensure that VM1 can access storage1. VM1 must be prevented from accessing any other storage accounts.
To achieve the requirement, you configure the firewall on storage1 to only accept connections from Vnet1.
Did you achieve the requirement?
A. Yes
B. No
Related Exams:
62-193
Technology Literacy for Educators70-243
Administering and Deploying System Center 2012 Configuration Manager70-355
Universal Windows Platform – App Data, Services, and Coding Patterns77-420
Excel 201377-427
Excel 2013 Expert Part One77-725
Word 2016 Core Document Creation, Collaboration and Communication77-726
Word 2016 Expert Creating Documents for Effective Communication77-727
Excel 2016 Core Data Analysis, Manipulation, and Presentation77-728
Excel 2016 Expert: Interpreting Data for Insights77-731
Outlook 2016 Core Communication, Collaboration and Email Skills
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only Microsoft exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your AZ-700 exam preparations and Microsoft certification application, do not hesitate to visit our Vcedump.com to find your solutions here.