Exam Details
Exam Code
:C2150-609Exam Name
:IBM Security Access Manager V9.0 DeploymentCertification
:IBM CertificationsVendor
:IBMTotal Questions
:138 Q&AsLast Updated
:Apr 12, 2025
IBM IBM Certifications C2150-609 Questions & Answers
-
Question 81:
An Access Manager environment utilizing failover coolies was recently upgraded from TAM 6.1.1 to IBM Security Access MANAGER (ISAM) V9.0. The deployment professional wants to take advantage of the Distributed Session Cache.
What are two advantages of the DSC verses failover coolies? (Choose two.)
A. Utilizes SHA2 encryption keys
B. Central administration of sessions
C. Concurrent session policy enforcement
D. Additional session cookie increasing security
E. Extra attributes passed in the session cookie
-
Question 82:
A deployment professional has created a new SAML 2.0 Service Provider federation and added an Identity Provider partner.
What will be the next step to allow users to single sign-on to the service?
A. Configure trigger URL
B. Upload a mapping rule
C. Import Identity Provider metadata
D. Create a certificate to sign SAML messages
-
Question 83:
Multiple users are complaining about being denied access to resources they believe they are entitled to see. The IBM Security Access Manager (ISAM) V9.0 deployment professional needs to understand and troubleshoot the various access control constructs in the ISAM protected object space. The deployment professional must also understand the order of evaluation of the three major access control constructs available in the Policy Administration tool.
That is the correct order of evaluation for these constructs?
A. ACL->AuthzRule->POP
B. POP->AuthzRule->ACL
C. ACL->POP->AuthzRule
D. AuthzRule->ACL->POP
-
Question 84:
An IBM Security Access Manager (ISAM) V9.0 deployment professional has downloaded a snapshot from an ISAM virtual appliance configured with reverse proxy. This snapshot is being applied to another virtual appliance.
Which condition must be met before applying a snapshot from one virtual appliance to another?
A. Both appliances must be in the same time zone
B. Both appliances must be at the same firmware level
C. Both appliances must have same application database setting
D. Both appliances must have the same activation keys applied.
-
Question 85:
A part of installing a fixpack a deployment professional wants to back up the appliance configuration. How is this done?
A. Click on the Create Backup link of the active partition
B. Select the active partition, select the Backup option form the Edit menu
C. Create a new snapshot, download the snapshot to the deployment professional's workstation, install the fixpack.
D. Install the fixpack. The installation will copy the configuration and install the fixpack to the inactive partition, set it active and restart.
-
Question 86:
A deployment professional has created an Access Control Policy to protect sensitive business information: Which Policy decision is returned for a user with a risk score of 35 and has consented to registering a device?
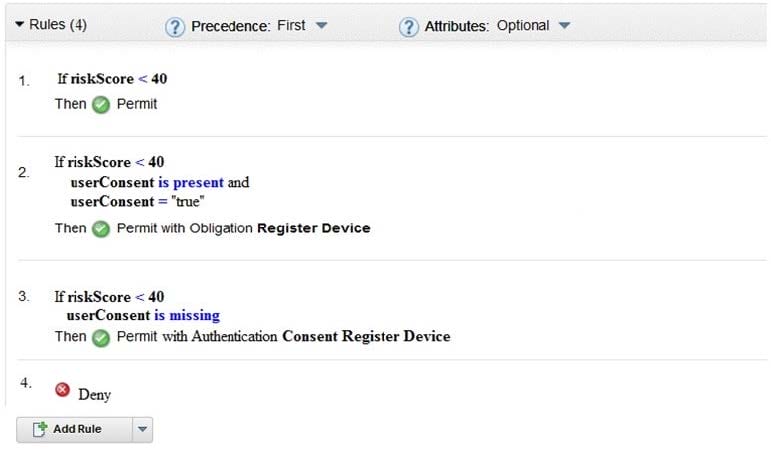
A. Deny
B. Permit
C. Permit with Obligation Register Device
D. Permit with Authentication Consent Register Device
-
Question 87:
An IBM Security Access Manager (ISAM) V9.0 environments is configured with Primary and Secondary Masters servers. The Primary master node becomes unavailable and ISAM deployment professional promotes the Secondary Master node to a Primary Master.
What happens to the original Primary Master when it becomes available and rejoins the network?
A. It is automatically removed from the cluster.
B. It is automatically demoted to the role of a non-master node.
C. It is automatically promoted to the role of a primary Master node.
D. It is automatically demoted to the role of a Secondary Master node.
-
Question 88:
The IBM Security Manager V9.0 Advances Access Control module can perform Context-based Authorization based on the contents of a POST parameter.
Which two configuration steps need to be performed to do this? (Choose two.)
A. Attach an appropriate Access Control List to the required URL
B. Attach an appropriate Access Control Policy to the required URL
C. Attach an appropriate Protected Information Point to the required URL
D. Add an entry to the [user-agents] stanza in the reverse proxy configuration file
E. Add an entry to the [user-attribute-definitions] stanza in the reverse proxy configuration file
-
Question 89:
The request in a customer environment is IDP Initiated unsolicited SSO. The initial URL is:
https://POCIDP/FIM/sps/saml2idp/saml20/loginitial?
RequestBinding =HTTPPostandPartnerId= https://POCSP/isam/sps/abc/saml20andNameIdFormat =Email
The POCIDP is Point of Contact for Identity Provider and POCSP is Point of Contact for Service Provider.
The customer wants to configure TargetURL within the Service Provider Federation configuration in IBM
Security Access Manager V9.0.
What will satisfy this requirement?
A. poc.sigin.responseTargetURL
B. Target_URL in the mapping rule
C. Federation Runtime property TargetURL
D. itfim_override_targeturl_attr in the mapping rule
-
Question 90:
A system is configured with two IBM Security Access Manager (ISAM) V9.0 reverse proxy servers behind a load balancer, and it is planned to use forms-based user authentication. It is a requirement that if a reverse proxy were to fail, users that were already logged in would not be required to log in again.
Which two configurations can the deployment professional use to achieve this? (Choose two.)
A. Configure the system to use LTPA cookies
B. Configure the system to use session cookies
C. Configure the system to use failover cookies
D. Configure the system to use the global signon (GSO) cache
E. Configure the system to use the Distributed Session Cache (DSC)
Related Exams:
C1000-002
IBM MQ V9.0 System AdministrationC1000-003
IBM Mobile Foundation v8.0 Application DevelopmentC1000-004
IBM Curam SPM V7.X Application DeveloperC1000-007
IBM Cloud Application Development v3C1000-010
IBM Operational Decision Manager Standard V8.9.1 Application DevelopmentC1000-012
IBM Watson Application Developer V3.1C1000-015
IBM Business Process Manager V8.6 Application Development using Process DesignerC1000-018
IBM QRadar SIEM V7.3.2 Fundamental AnalysisC1000-020
IBM New Workloads Sales V2C1000-021
IBM Virtualized Storage V2
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only IBM exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your C2150-609 exam preparations and IBM certification application, do not hesitate to visit our Vcedump.com to find your solutions here.