Exam Details
Exam Code
:C9510-401Exam Name
:IBM WebSphere Application Server Network Deployment V8.5.5 and Liberty Profile System AdministrationCertification
:IBM CertificationsVendor
:IBMTotal Questions
:73 Q&AsLast Updated
:Apr 09, 2025
IBM IBM Certifications C9510-401 Questions & Answers
-
Question 61:
A system administrator wants to learn some of the Jython scripting commands for the administration of the environment.
Which product feature should the administrator use?
A. The wsadmin.properties file to load a profile.
B. The AdminTask object to generate wsadmin scripts.
C. The guided activities panel from the Integrated Solutions Console (ISC).
D. The "Log command assistance commands" option in the Integrated Solutions Console (ISC).
-
Question 62:
A web application has a configured session timeout of eight hours and a default LTPA token timeout of two hours. After every two hours, the users have to log in again from their HTTP browser. The system administrator is required to make configuration changed so users only have to log in once, while keeping the above mentioned timeouts the same. The authentication mechanism available is Kerberos.
How should the administrator do this?
A. Configure the SIP digest authentication.
B. Configure the SPNEGO Web or SPNEGO TAI.
C. Enable Session Management Security Integration.
D. Ensure Web Inbound security attribute propagation is enabled.
-
Question 63:
A WebSphere system administrator needs to install the Installation Manager (IM) on an unmanaged node on a host named
. The deployment manager is running on a host named . What step must the administrator take before submitting a job from the Integrated Solutions Console (ISC) to install the IM on
? A. Install a node agent on
. B. Install the job manager on
. C. Start the job manager on
. D. Register
as a target for job manager. -
Question 64:
A developer created an enterprise application which contained data source and security role information. The developer asked a system administrator to install this application to an application server where global security is enabled using the Integrated Solutions Console (ISC). A new data source was configured at the server scope for the use of this application. While load testing the application, the developer noticed that the attributes configured on the new data source were ignored by the application server.
How can the administrator ensure that the attributes configured on the new data source are used by the application server?
A. Create the data source under cell scope instead of server scope.
B. Delete any data source of the same name defined under node, cluster or cell scope.
C. Reinstall the application and clear the Process embedded configuration check box.
D. Correct the component-managed and container-managed authentication aliases set on the data source.
-
Question 65:
The administrator needs to identify any security role references and security constraints in a web application.
How can the administrator identify these roles and constraints?
A. ibm-application-ext.xml file using a text editor.
B. ibmconfig folder in the application after using the EARExpander command.
C. Web deployment descriptor using IBM Assembly and Deploy Tools.
D. Security role to user/group mapping by using the Integrated Solutions Console (ISC).
-
Question 66:
A system administrator discovers an issue that requires a change to a federated server. In this cell,
WebSphere administrative security is enabled, but application security is not enabled.
How should the administrator make this change?
The administrator should use:
A. a web browser to connect to the node agent https port.
B. a web browser to connect to the deployment manager admin_host port.
C. the job manager to submit a job to update the unmanaged server.
D. an ssh connection to the node and modify the client_types.xml file.
-
Question 67:
A system administrator has created a cluster containing two servers in a same node. The administrator did not select the option Generate unique HTTP ports during the creation of the cluster members. After the cluster creation, the administrator changed the HTTP port of the second cluster member to 9081.
Testing the servers using the snoop servlet directly to the server's HTTP port, the administrator got the following error message for the second server:
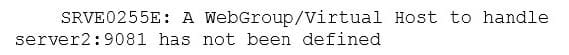
How can the administrator fix this problem?
A. Regenerate and propagate the HTTP plug-in.
B. Add the port 9081 to the default_host alias.
C. Create a new virtual host alias at the cell level for the port 9081.
D. Edit the server.xml for the second server and add the port 9081.
-
Question 68:
A system administrator completed a WebSphere Application Server installation by using the Installation Manager. During installation, all defaults were selected for the installation root directories and the shared resources directory. Over time, the administrator has updated the installation with various interim fixes and fix packs. The administrator notices that the shared resources directory is very large in size and grows larger each time the Installation Manager is run.
How can the administrator decrease the size and remove some of the content from the shared resources directory?
A. Manually delete content from the directory.
B. During an update, create a new shared resources directory.
C. Clear the Delete Saved Files option for the Installation Manager.
D. Set the preserve Downloaded Artifacts preference to false.
-
Question 69:
A newly deployed application has authorization errors when invoking EJB methods from a servlet. An additional review indicates that users are authenticated, but do not have the correct authorization.
How can a system administrator fix the issue ensuring only authorized access?
A. Using the Integrated Solutions Console (ISC), map all security roles to the special subject Everyone.
B. Using the Integrated Solutions Console (ISC), map the security roles that are still not mapped to groups in the correct user registry.
C. Edit the application using an assembly tool to add a security constraint for the servlet and reinstall the application.
D. Edit the application using an assembly tool to remove the security constraint defined for the servlet and reinstall the application.
-
Question 70:
A system administrator suspects that the slow performance of an application might be caused by lock contention.
To debug this further, what can the administrator do using IBM Support Assistant?
A. Analyze the running server using IBM Monitoring and Diagnostic Tools for Java ?Health Center.
B. Collect a javacore and analyze it using IBM Monitoring and Diagnostic Tools for Java ?Health Center.
C. Collect three thread dumps at equal time intervals and analyze them using IBM Monitoring and Diagnostic Tools for Java ?Dump Analyzer.
D. Collect three system dumps at equal time intervals and analyze them using IBM Monitoring and Diagnostic Tools for Java ?Memory Analyzer.
Related Exams:
C1000-002
IBM MQ V9.0 System AdministrationC1000-003
IBM Mobile Foundation v8.0 Application DevelopmentC1000-004
IBM Curam SPM V7.X Application DeveloperC1000-007
IBM Cloud Application Development v3C1000-010
IBM Operational Decision Manager Standard V8.9.1 Application DevelopmentC1000-012
IBM Watson Application Developer V3.1C1000-015
IBM Business Process Manager V8.6 Application Development using Process DesignerC1000-018
IBM QRadar SIEM V7.3.2 Fundamental AnalysisC1000-020
IBM New Workloads Sales V2C1000-021
IBM Virtualized Storage V2
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only IBM exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your C9510-401 exam preparations and IBM certification application, do not hesitate to visit our Vcedump.com to find your solutions here.