Exam Details
Exam Code
:CAS-002Exam Name
:CompTIA Advanced Security Practitioner (CASP+)Certification
:CompTIA CertificationsVendor
:CompTIATotal Questions
:733 Q&AsLast Updated
:Jan 22, 2024
CompTIA CompTIA Certifications CAS-002 Questions & Answers
-
Question 641:
A security administrator is tasked with securing a company's headquarters and branch offices move to unified communications. The Chief Information Officer (CIO) wants to integrate the corporate users' email, voice mail, telephony, presence and corporate messaging to internal computers, mobile users, and devices. Which of the following actions would BEST meet the CIO's goals while providing maximum unified communications security?
A. Create presence groups, restrict IM protocols to the internal networks, encrypt remote devices, and restrict access to services to local network and VPN clients.
B. Enable discretionary email forwarding restrictions, utilize QoS and Secure RTP, allow external IM protocols only over TLS, and allow port 2000 incoming to the internal firewall interface for secure SIP
C. Set presence to invisible by default, restrict IM to invite only, implement QoS on SIP and RTP traffic, discretionary email forwarding, and full disk encryption.
D. Establish presence privacy groups, restrict all IM protocols, allow secure RTP on session border gateways, enable full disk encryptions, and transport encryption for email security.
-
Question 642:
The Information Security Officer (ISO) is reviewing a summary of the findings from the last COOP tabletop exercise. The Chief Information Officer (CIO) wants to determine which additional controls must be implemented to reduce the risk of an extended customer service outage due to the VoIP system being unavailable. Which of the following BEST describes the scenario presented and the document the ISO is reviewing?
A. The ISO is evaluating the business implications of a recent telephone system failure within the BIA.
B. The ISO is investigating the impact of a possible downtime of the messaging system within the RA.
C. The ISO is calculating the budget adjustment needed to ensure audio/video system redundancy within the RFQ.
D. The ISO is assessing the effect of a simulated downtime involving the telecommunication system within the AAR.
-
Question 643:
-- Exhibit ?
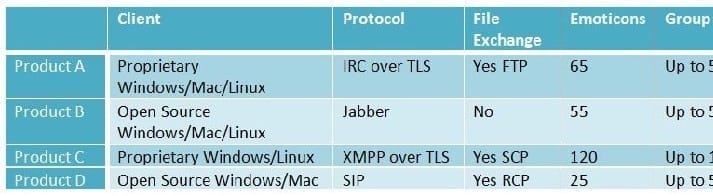
-- Exhibit -
Company management has indicated that instant messengers (IM) add to employee productivity. Management would like to implement an IM solution, but does not have a budget for the project. The security engineer creates a feature matrix
to help decide the most secure product. Click on the Exhibit button.
Which of the following would the security engineer MOST likely recommend based on the table?
A. Product A
B. Product B
C. Product C
D. Product D
-
Question 644:
A government agency considers confidentiality to be of utmost importance and availability issues to be of least importance. Knowing this, which of the following correctly orders various vulnerabilities in the order of MOST important to LEAST important?
A. Insecure direct object references, CSRF, Smurf
B. Privilege escalation, Application DoS, Buffer overflow
C. SQL injection, Resource exhaustion, Privilege escalation
D. CSRF, Fault injection, Memory leaks
-
Question 645:
A system administrator is troubleshooting a possible denial of service on a sensitive system. The system seems to run properly for a few hours after it is restarted, but then it suddenly stops processing transactions. The system administrator suspects an internal DoS caused by a disgruntled developer who is currently seeking a new job while still working for the company. After looking into various system logs, the system administrator looks at the following output from the main system service responsible for processing incoming transactions. DATE/TIMEPIDCOMMAND%CPUMEM
031020141030002055com.proc10.2920K
031020141100002055com.proc12.35.2M
031020141230002055com.proc22.022M
031020141300002055com.proc33.01.6G
031020141330002055com.proc30.28.0G
Which of the following is the MOST likely cause for the DoS?
A. The system does not implement proper garbage collection.
B. The system is susceptible to integer overflow.
C. The system does not implement input validation.
D. The system does not protect against buffer overflows properly.
-
Question 646:
Company XYZ has just purchased Company ABC through a new acquisition. A business decision has been made to integrate the two company's networks, application, and several basic services.
The initial integration of the two companies has specified the following requirements:
Company XYZ requires access to the web intranet, file, print, secure FTP server, and authentication domain resources Company XYZ is being on boarded into Company ABC's authentication domain Company XYZ is considered partially trusted Company XYZ does not want performance issues when accessing ABC's systems
Which of the following network security solutions will BEST meet the above requirements?
A. Place a Company ABC managed firewall in Company XYZ's hub site; then place Company ABC's file, print, authentication, and secure FTP servers in a zone off the firewall. Ensure that Company ABC's business partner firewalls are opened up for web intranet access and other required services.
B. Require Company XYZ to manage the router ACLs, controlling access to Company ABC resources, but with Company ABC approving the change control to the ACLs. Open up Company ABC's business partner firewall to permit access to Company ABC's file, print, secure FTP server, authentication servers and web intranet access.
C. Place no restrictions on internal network connectivity between Company XYZ and Company ABC. Open up Company ABC's business partner firewall to permit access to Company ABC's file, print, secure FTP server, authentication servers and web intranet access.
D. Place file, print, secure FTP server and authentication domain servers at Company XYZ's hub site. Open up Company ABC's business partner firewall to permit access to ABC's web intranet access and other required services.
-
Question 647:
Company A needs to export sensitive data from its financial system to company B's database, using company B's API in an automated manner. Company A's policy prohibits the use of any intermediary external systems to transfer or store its sensitive data, therefore the transfer must occur directly between company A's financial system and company B's destination server using the supplied API. Additionally, company A's legacy financial software does not support encryption, while company B's API supports encryption. Which of the following will provide end-to-end encryption for the data transfer while adhering to these requirements?
A. Company A must install an SSL tunneling service on the financial system.
B. Company A's security administrator should use an HTTPS capable browser to transfer the data.
C. Company A should use a dedicated MPLS circuit to transfer the sensitive data to company B.
D. Company A and B must create a site-to-site IPSec VPN on their respective firewalls.
-
Question 648:
A company has implemented data retention policies and storage quotas in response to their legal department's requests and the SAN administrator's recommendation. The retention policy states all email data older than 90 days should be eliminated. As there are no technical controls in place, users have been instructed to stick to a storage quota of 500Mb of network storage and 200Mb of email storage. After being presented with an e- discovery request from an opposing legal council, the security administrator discovers that the user in the suit has 1Tb of files and 300Mb of email spanning over two years. Which of the following should the security administrator provide to opposing council?
A. Delete files and email exceeding policy thresholds and turn over the remaining files and email.
B. Delete email over the policy threshold and hand over the remaining emails and all of the files.
C. Provide the 1Tb of files on the network and the 300Mb of email files regardless of age.
D. Provide the first 200Mb of e-mail and the first 500Mb of files as per policy.
-
Question 649:
A security administrator at Company XYZ is trying to develop a body of knowledge to enable heuristic and behavior based security event monitoring of activities on a geographically distributed network. Instrumentation is chosen to allow for monitoring and measuring the network. Which of the following is the BEST methodology to use in establishing this baseline?
A. Model the network in a series of VMs; instrument the systems to record comprehensive metrics; run a large volume of simulated data through the model; record and analyze results; document expected future behavior.
B. Completely duplicate the network on virtual machines; replay eight hours of captured corporate network traffic through the duplicate network; instrument the network; analyze the results; document the baseline.
C. Instrument the operational network; simulate extra traffic on the network; analyze net flow information from all network devices; document the baseline volume of traffic.
D. Schedule testing on operational systems when users are not present; instrument the systems to log all network traffic; monitor the network for at least eight hours; analyze the results; document the established baseline.
-
Question 650:
A security auditor is conducting an audit of a corporation where 95% of the users travel or work from non- corporate locations a majority of the time. While the employees are away from the corporate offices, they retain full access to the corporate network and use of corporate laptops. The auditor knows that the corporation processes PII and other sensitive data with applications requiring local caches of any data being manipulated. Which of the following security controls should the auditor check for and recommend to be implemented if missing from the laptops?
A. Trusted operating systems
B. Full disk encryption
C. Host-based firewalls
D. Command shell restrictions
Related Exams:
220-1001
CompTIA A+ Certification: Core 1220-1002
CompTIA A+ Certification: Core 2220-1101
CompTIA A+ Certification: Core 1220-1102
CompTIA A+ Certification: Core 2220-902
CompTIA A+ CertificationCAS-004
CompTIA Advanced Security Practitioner (CASP+)CAS-005
CompTIA SecurityXCLO-001
CompTIA Cloud Essentials+CLO-002
CompTIA Cloud Essentials+CS0-002
CompTIA Cybersecurity Analyst (CySA+)
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only CompTIA exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your CAS-002 exam preparations and CompTIA certification application, do not hesitate to visit our Vcedump.com to find your solutions here.