Exam Details
Exam Code
:CAS-004Exam Name
:CompTIA Advanced Security Practitioner (CASP+)Certification
:CompTIA CertificationsVendor
:CompTIATotal Questions
:743 Q&AsLast Updated
:Apr 07, 2025
CompTIA CompTIA Certifications CAS-004 Questions & Answers
-
Question 131:
Which of the following testing plans is used to discuss disaster recovery scenarios with representatives from multiple departments within an incident response team but without taking any invasive actions?
A. Disaster recovery checklist
B. Tabletop exercise
C. Full interruption test
D. Parallel test
-
Question 132:
A partner organization is requesting that a security administrator exchange S/MIME certificates for email between the two organizations. The partner organization is most likely trying to:
A. utilize digital signatures to ensure data integrity.
B. reduce the amount of impersonation spam the organization receives.
C. enable a more decentralized IT infrastructure.
D. eliminate the organization's business email compromise risks.
-
Question 133:
An organization recently completed a security controls assessment. The results highlighted the following vulnerabilities:
1.
Out-of-date definitions
2.
Misconfigured operating systems
3.
An inability to detect active attacks
4.
Unimpeded access to critical servers' USB ports
Which of the following will most likely reduce the risks that were identified by the assessment team?
A. Install EDR on endpoints, configure group policy, lock server room doors, and install a camera system with guards watching 24/7.
B. Create an information security program that addresses user training, perform weekly audits of user workstations, and utilize a centralized configuration management program.
C. Update antivirus definitions, install NGFW with logging enabled, use USB port lockers, and run SCAP scans weekly.
D. Implement a vulnerability management program and a SIEM tool with alerting, install a badge system with zones, and restrict privileged access.
-
Question 134:
A penetration tester discovers a condition that causes unexpected behavior in a web application. This results in the dump of the interpreter's debugging information, which includes the interpreter's version, full path of binary files, and the user ID running the process. Which of the following actions would best mitigate this risk?
A. Include routines in the application for message handling.
B. Adopt a compiled programming language instead.
C. Perform SAST vulnerability scans on every build.
D. Validate user-generated input.
-
Question 135:
A pharmaceutical company uses a cloud provider to host thousands of independent resources in object storage. The company needs a practical and effective means of discovering data, monitoring changes, and identifying suspicious activity. Which of the following would best meet these requirements?
A. A machine-learning-based data security service
B. A file integrity monitoring service
C. A cloud configuration assessment and compliance service
D. A cloud access security broker
-
Question 136:
A security engineer at a manufacturing facility is trying to determine whether any of the OT devices are susceptible to a recently announced vulnerability. Which of the following is the best way for the engineer to detect exploitable vulnerabilities?
A. Utilize a passive vulnerability scanner on the network.
B. Compare deployed equipment to the CVE disclosure.
C. Perform threat hunting on the OT segment.
D. Review software inventory for vulnerable versions.
-
Question 137:
A security team performed an external attack surface analysis and discovered the following issues on a group of application servers:
1.
The majority of the systems have end-of-life operating systems.
2.
The latest patches that are available are over two years old.
3.
The systems are considered mission critical for client support.
4.
The proprietary software running on the systems is not compatible with newer versions of the operating system.
5.
Server outages would negatively affect quarterly revenue projections.
Which of the following would allow the security team to immediately mitigate the risks inherent to this situation?
A. Implement a WAF between the application servers and the external perimeter.
B. Contact the vendor for the proprietary software and negotiate a new maintenance contract.
C. Document the application servers as being end of life and define a target date for decommission.
D. Isolate the servers from the internet and configure an internal ACL, only allowing to authorized employees.
-
Question 138:
Based on a recent security audit, a company discovered the perimeter strategy is inadequate for its recent growth. To address this issue, the company is looking for a solution that includes the following requirements:
1.
Collapse of multiple network security technologies into a single footprint
2.
Support for multiple VPNs with different security contexts
3.
Support for application layer security (Layer 7 of the OSI Model)
Which of the following technologies would be the most appropriate solution given these requirements?
A. NAT gateway
B. Reverse proxy
C. NGFW
D. NIDS
-
Question 139:
An engineering team is developing and deploying a fleet of mobile devices to be used for specialized inventory management purposes. These devices should:
1.
Be based on open-source Android for user familiarity and ease.
2.
Provide a single application for inventory management of physical assets.
3.
Permit use of the camera be only the inventory application for the purposes of scanning
4.
Disallow any and all configuration baseline modifications.
Restrict all access to any device resource other than those requirement ?
A. Set an application wrapping policy, wrap the application, distributes the inventory APK via the MAM tool, and test the application restrictions.
B. Write a MAC sepolicy that defines domains with rules, label the inventory application, build the policy, and set to enforcing mode.
C. Swap out Android Linux kernel version for >2,4,0, but the internet build Android, remove unnecessary functions via MDL, configure to block network access, and perform integration testing
D. Build and install an Android middleware policy with requirements added, copy the file into/ user/init, and then built the inventory application.
-
Question 140:
A company implements the following access control methodology based on the following data classifications:
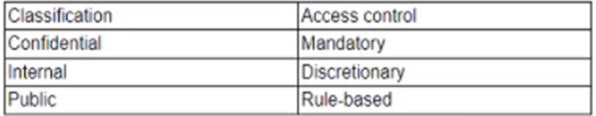
The Chief Information Security Officer (CISO) wants to implement an additional layer of access control based on the geographic location of the underlying system that processes and stores data. The additional layer will be added to the existing access control system. Which of the following components must be implemented to achieve these goals? (Choose two.)
A. Tagging
B. Attribute-based access control
C. Role-based access control
D. Groups
E. Tokenization
F. Digital rights management
Related Exams:
220-1001
CompTIA A+ Certification: Core 1220-1002
CompTIA A+ Certification: Core 2220-1101
CompTIA A+ Certification: Core 1220-1102
CompTIA A+ Certification: Core 2220-902
CompTIA A+ CertificationCAS-004
CompTIA Advanced Security Practitioner (CASP+)CAS-005
CompTIA SecurityXCLO-001
CompTIA Cloud Essentials+CLO-002
CompTIA Cloud Essentials+CS0-002
CompTIA Cybersecurity Analyst (CySA+)
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only CompTIA exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your CAS-004 exam preparations and CompTIA certification application, do not hesitate to visit our Vcedump.com to find your solutions here.