Exam Details
Exam Code
:CAS-004Exam Name
:CompTIA Advanced Security Practitioner (CASP+)Certification
:CompTIA CertificationsVendor
:CompTIATotal Questions
:743 Q&AsLast Updated
:Apr 15, 2025
CompTIA CompTIA Certifications CAS-004 Questions & Answers
-
Question 201:
A user in the finance department uses a laptop to store a spreadsheet that contains confidential financial information for the company.
Which of the following would be the BEST way to protect the file while the user travels between locations? (Choose two.)
A. Encrypt the laptop with full disk encryption.
B. Back up the file to an encrypted flash drive.
C. Place an ACL on the file to only allow access to specified users.
D. Store the file in the user profile.
E. Place an ACL on the file to deny access to everyone.
F. Enable access logging on the file.
-
Question 202:
A security assessor identified an internet-facing web service API provider that was deemed vulnerable. Execution of testssl provided the following insight:
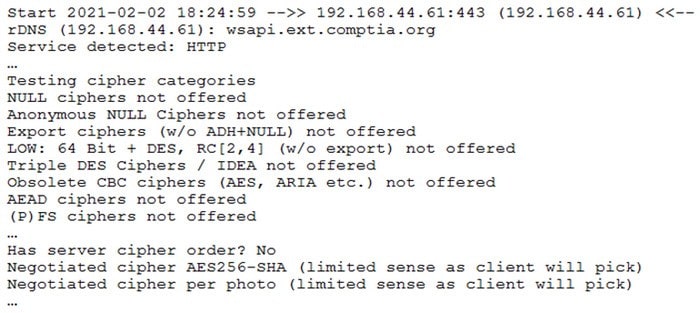
Which of the following configuration changes would BEST mitigate chosen ciphertext attacks?
A. Enable 3DES ciphers IDEA.
B. Enable export ciphers.
C. Enable PFS ciphers.
D. Enable AEAD.
-
Question 203:
Some end users of an e-commerce website are reporting a delay when browsing pages. The website uses TLS 1.2. A security architect for the website troubleshoots by connecting from home to the website and capturing traffic via Wireshark. The security architect finds that the issue is the time required to validate the certificate. Which of the following solutions should the security architect recommend?
A. Adding more nodes to the web server clusters
B. Changing the cipher algorithm used on the web server
C. Implementing OCSP stapling on the server
D. Upgrading to TLS 1.3
-
Question 204:
A help desk technician is troubleshooting an issue with an employee's laptop that will not boot into its operating system. The employee reported the laptop had been stolen but then found it one day later. The employee has asked the technician for help recovering important data. The technician has identified the following:
1.
The laptop operating system was not configured with BitLocker.
2.
The hard drive has no hardware failures.
3.
Data is present and readable on the hard drive, although it appears to be illegible.
Which if the following is the MOST likely reason the technician is unable to retrieve legible data from the hard drive?
A. The employee's password was changed, and the new password needs to be used.
B. The PKI certificate was revoked, and a new one must be installed.
C. The hard drive experienced crypto-shredding.
D. The technician is using the incorrect cipher to read the data.
-
Question 205:
A security engineer performed an assessment on a recently deployed web application. The engineer was able to exfiltrate a company report by visiting the following URL:
www.intranet.abc.com/get-files.jsp?file=report.pdf
Which of the following mitigation techniques would be BEST for the security engineer to recommend?
A. Input validation
B. Firewall
C. WAF
D. DLP
-
Question 206:
A security administrator wants to detect a potential forged sender claim in the envelope of an email. Which of the following should the security administrator implement? (Choose two.)
A. MX record
B. DMARC
C. SPF
D. DNSSEC
E. S/MIME
F. TLS
-
Question 207:
A company is acquiring a competitor, and the security team is performing due diligence activities on the competitor prior to the acquisition. The team found a recent compliance audit of the competitor's environment that shows a mature security infrastructure, but it lacks a cohesive policy and process framework. Based on the audit findings, the security team determines the competitor's existing security capabilities are sufficient, but they will need to incorporate additional security policies. Which of the following risk management strategies is the security team recommending?
A. Mitigate and avoid
B. Transfer and accept
C. Avoid and transfer
D. Accept and mitigate
-
Question 208:
A security analyst is reviewing SIEM events and is uncertain how to handle a particular event. The file is reviewed with the security vendor who is aware that this type of file routinely triggers this alert. Based on this information, the security
analyst acknowledges this alert. Which of the following event classifications is MOST likely the reason for this action?
A. True negative
B. False negative
C. False positive
D. Non-automated response
-
Question 209:
The Chief Information Security Officer (CISO) asked a security manager to set up a system that sends an alert whenever a mobile device enters a sensitive area of the company's data center. The CISO would also like to be able to alert the individual who is entering the area that the access was logged and monitored. Which of the following would meet these requirements?
A. Near-field communication
B. Short Message Service
C. Geofencing
D. Bluetooth
-
Question 210:
An architectural firm is working with its security team to ensure that any draft images that are leaked to the public can be traced back to a specific external party. Which of the following would BEST accomplish this goal?
A. Properly configure a secure file transfer system to ensure file integrity.
B. Have the external parties sign non-disclosure agreements before sending any images.
C. Only share images with external parties that have worked with the firm previously.
D. Utilize watermarks in the images that are specific to each external party.
Related Exams:
220-1001
CompTIA A+ Certification: Core 1220-1002
CompTIA A+ Certification: Core 2220-1101
CompTIA A+ Certification: Core 1220-1102
CompTIA A+ Certification: Core 2220-902
CompTIA A+ CertificationCAS-004
CompTIA Advanced Security Practitioner (CASP+)CAS-005
CompTIA SecurityXCLO-001
CompTIA Cloud Essentials+CLO-002
CompTIA Cloud Essentials+CS0-002
CompTIA Cybersecurity Analyst (CySA+)
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only CompTIA exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your CAS-004 exam preparations and CompTIA certification application, do not hesitate to visit our Vcedump.com to find your solutions here.