Exam Details
Exam Code
:CAS-004Exam Name
:CompTIA Advanced Security Practitioner (CASP+)Certification
:CompTIA CertificationsVendor
:CompTIATotal Questions
:743 Q&AsLast Updated
:Apr 15, 2025
CompTIA CompTIA Certifications CAS-004 Questions & Answers
-
Question 281:
An organization developed an incident response plan. Which of the following would be BEST to assess the effectiveness of the plan?
A. Requesting a third-party review
B. Generating a checklist by organizational unit
C. Establishing role succession and call lists
D. Creating a playbook
E. Performing a tabletop exercise
-
Question 282:
A security analyst has concerns about malware on an endpoint. The malware is unable to detonate by modifying the kernel response to various system calls. As a test, the analyst modifies a Windows server to respond to system calls as if it was a Linux server. In another test, the analyst modifies the operating system to prevent the malware from identifying target files. Which of the following techniques is the analyst MOST likely using?
A. Honeypot
B. Deception
C. Simulators
D. Sandboxing
-
Question 283:
A penetration tester is testing a company's login form for a web application using a list of known usernames and a common password list. According to a brute-force utility, the penetration tester needs to provide the tool with the proper headers, POST URL with variable names, and the error string returned with an improper login. Which of the following would BEST help the tester to gather this information? (Choose two.)
A. The new source feature of the web browser
B. The logs from the web server
C. The inspect feature from the web browser
D. A tcpdump from the web server
E. An HTTP interceptor
F. The website certificate viewed via the web browser
-
Question 284:
An architect is designing security scheme for an organization that is concerned about APTs. Any proposed architecture must meet the following requirements:
1.
Services must be able to be reconstituted quickly from a known-good state.
2.
Network services must be designed to ensure multiple diverse layers of redundancy.
3.
Defensive and responsive actions must be automated to reduce human operator demands.
Which of the following designs must be considered to ensure the architect meets these requirements? (Choose three.)
A. Increased efficiency by embracing advanced caching capabilities
B. Geographic distribution of critical data and services
C. Hardened and verified container usage
D. Emulated hardware architecture usage
E. Establishment of warm and hot sites for continuity of operations
F. Heterogeneous architecture
G. Deployment of IPS services that can identify and block malicious traffic
H. Implementation and configuration of a SOAR
-
Question 285:
A security administrator sees several hundred entries in a web server security log that are similar to the following:
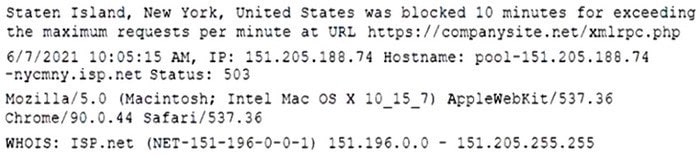
The network source varies, but the URL, status, and user agent are the same. Which of the following would BEST protect the web server without blocking legitimate traffic?
A. Replace the file xmlrpc.php with a honeypot form to collect further IOCs.
B. Automate the addition of bot IP addresses into a deny list for the web host.
C. Script the daily collection of the WHOIS ranges to add to the WAF as a denied ACL.
D. Block every subnet that is identified as having a bot that is a source of the traffic.
-
Question 286:
A third-party organization has implemented a system that allows it to analyze customers' data and deliver analysis results without being able to see the raw data. Which of the following is the organization implementing?
A. Asynchronous keys
B. Homomorphic encryption
C. Data lake
D. Machine learning
-
Question 287:
A company is on a deadline to roll out an entire CRM platform to all users at one time. However, the company is behind schedule due to reliance on third-party vendors. Which of the following development approaches will allow the company to begin releases but also continue testing and development for future releases?
A. Implement iterative software releases
B. Revise the scope of the project to use a waterfall approach.
C. Change the scope of the project to use the spiral development methodology.
D. Perform continuous integration.
-
Question 288:
A software development company is building a new mobile application for its social media platform. The company wants to gain its users' trust by reducing the risk of on-path attacks between the mobile client and its servers and by implementing stronger digital trust. To support users' trust, the company has released the following internal guidelines:
1.
Mobile clients should verity the identity of all social media servers locally.
2.
Social media servers should improve TLS performance of their certificate status.
3.
Social media servers should inform the client to only use HTTPS.
Given the above requirements, which of the following should the company implement? (Choose two.)
A. Quick UDP internet connection
B. OCSP stapling
C. Private CA
D. DNSSEC
E. CRL
F. HSTS
G. Distributed object model
-
Question 289:
Which of the following communication protocols is used to create PANs with small, low-power digital radios and supports a large number of nodes?
A. Zigbee
B. Wi-Fi
C. CAN
D. Modbus
E. DNP3
-
Question 290:
A pharmaceutical company was recently compromised by ransomware. Given the following EDR output from the process investigation: On which of the following devices and processes did the ransomware originate?
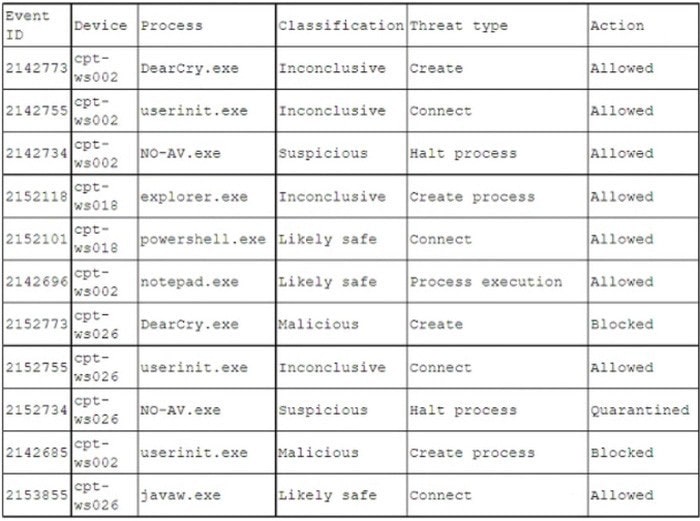
A. cpt-ws018, powershell.exe
B. cpt-ws026, DearCry.exe
C. cpt-ws002, NO-AV.exe
D. cpt-ws026, NO-AV.exe
E. cpt-ws002, DearCry.exe
Related Exams:
220-1001
CompTIA A+ Certification: Core 1220-1002
CompTIA A+ Certification: Core 2220-1101
CompTIA A+ Certification: Core 1220-1102
CompTIA A+ Certification: Core 2220-902
CompTIA A+ CertificationCAS-004
CompTIA Advanced Security Practitioner (CASP+)CAS-005
CompTIA SecurityXCLO-001
CompTIA Cloud Essentials+CLO-002
CompTIA Cloud Essentials+CS0-002
CompTIA Cybersecurity Analyst (CySA+)
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only CompTIA exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your CAS-004 exam preparations and CompTIA certification application, do not hesitate to visit our Vcedump.com to find your solutions here.