Exam Details
Exam Code
:CAS-004Exam Name
:CompTIA Advanced Security Practitioner (CASP+)Certification
:CompTIA CertificationsVendor
:CompTIATotal Questions
:743 Q&AsLast Updated
:Apr 15, 2025
CompTIA CompTIA Certifications CAS-004 Questions & Answers
-
Question 501:
A small business would like to provide guests who are using mobile devices encrypted WPA3 access without first distributing PSKs or other credentials. Which of the following features will enable the business to meet this objective?
A. Simultaneous Authentication of Equals
B. Enhanced open
C. Perfect forward secrecy
D. Extensible Authentication Protocol
-
Question 502:
A user experiences an HTTPS connection error when trying to access an Internet banking website from a corporate laptop. The user then opens a browser on a mobile phone and is able to access the same Internet banking website without issue. Which of the following security configurations is MOST likely the cause of the error?
A. HSTS
B. TLS 1.2
C. Certificate pinning
D. Client authentication
-
Question 503:
An organization requires a legacy system to incorporate reference data into a new system. The organization anticipates the legacy system will remain in operation for the next 18 to 24 months. Additionally, the legacy system has multiple critical vulnerabilities with no patches available to resolve them. Which of the following is the BEST design option to optimize security?
A. Limit access to the system using a jump box.
B. Place the new system and legacy system on separate VLANs
C. Deploy the legacy application on an air-gapped system.
D. Implement MFA to access the legacy system.
-
Question 504:
A company Is adopting a new artificial-intelligence-based analytics SaaS solution. This Is the company's first attempt at using a SaaS solution, and a security architect has been asked to determine any future risks. Which of the following would be the GREATEST risk In adopting this solution?
A. The inability to assign access controls to comply with company policy
B. The inability to require the service provider process data in a specific country
C. The inability to obtain company data when migrating to another service
D. The inability to conduct security assessments against a service provider
-
Question 505:
A company Invested a total of $10 million lor a new storage solution Installed across live on-site datacenters. Fitly percent of the cost of this Investment was for solid-state storage. Due to the high rate of wear on this storage, the company Is estimating that 5% will need to be replaced per year. Which of the following is the ALE due to storage replacement?
A. $50,000
B. $125,000
C. $250,000
D. $500.000
E. $51,000,000
-
Question 506:
A business wants to migrate its workloads from an exclusively on-premises IT infrastructure to the cloud but cannot implement all the required controls. Which of the following BEST describes the risk associated with this implementation?
A. Loss of governance
B. Vendor lockout
C. Compliance risk
D. Vendor lock-in
-
Question 507:
An organization is assessing the security posture of a new SaaS CRM system that handles sensitive Pll and identity information, such as passport numbers. The SaaS CRM system does not meet the organization's current security standards.
The assessment identifies the following:
1- There will be a $20,000 per day revenue loss for each day the system is delayed going into production.
2- The inherent risk is high.
3- The residual risk is low.
4- There will be a staged deployment to the solution rollout to the contact center.
Which of the following risk-handling techniques will BEST meet the organization's requirements?
A. Apply for a security exemption, as the risk is too high to accept.
B. Transfer the risk to the SaaS CRM vendor, as the organization is using a cloud service.
C. Accept the risk, as compensating controls have been implemented to manage the risk.
D. Avoid the risk by accepting the shared responsibility model with the SaaS CRM provider.
-
Question 508:
A security engineer needs to implement a CASB to secure employee user web traffic. A key requirement is that the relevant event data must be collected from existing on-premises infrastructure components and consumed by the CASB to
expand traffic visibility. The solution must be highly resilient to network outages.
Which of the following architectural components would BEST meet these requirements?
A. Log collection
B. Reverse proxy
C. AWAF
D. API mode
-
Question 509:
A security analyst discovered that a database administrator's workstation was compromised by malware. After examining the Jogs. the compromised workstation was observed connecting to multiple databases through ODBC. The following query behavior was captured:
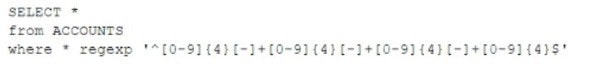
Assuming this query was used to acquire and exfiltrate data, which of the following types of data was compromised, and what steps should the incident response plan contain?
A. Personal health information: Inform the human resources department of the breach and review the DLP logs.
B. Account history; Inform the relationship managers of the breach and create new accounts for the affected users.
C. Customer IDs: Inform the customer service department of the breach and work to change the account numbers.
D. PAN: Inform the legal department of the breach and look for this data in dark web monitoring.
-
Question 510:
A help desk technician just informed the security department that a user downloaded a suspicious file from internet explorer last night. The user confirmed accessing all the files and folders before going home from work. the next morning, the user was no longer able to boot the system and was presented a screen with a phone number. The technician then tries to boot the computer using wake-on-LAN, but the system would not come up. which of the following explains why the computer would not boot?
A. The operating system was corrupted.
B. SElinux was in enforced status.
C. A secure boot violation occurred.
D. The disk was encrypted.
Related Exams:
220-1001
CompTIA A+ Certification: Core 1220-1002
CompTIA A+ Certification: Core 2220-1101
CompTIA A+ Certification: Core 1220-1102
CompTIA A+ Certification: Core 2220-902
CompTIA A+ CertificationCAS-004
CompTIA Advanced Security Practitioner (CASP+)CAS-005
CompTIA SecurityXCLO-001
CompTIA Cloud Essentials+CLO-002
CompTIA Cloud Essentials+CS0-002
CompTIA Cybersecurity Analyst (CySA+)
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only CompTIA exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your CAS-004 exam preparations and CompTIA certification application, do not hesitate to visit our Vcedump.com to find your solutions here.