Exam Details
Exam Code
:CAS-004Exam Name
:CompTIA Advanced Security Practitioner (CASP+)Certification
:CompTIA CertificationsVendor
:CompTIATotal Questions
:743 Q&AsLast Updated
:Apr 15, 2025
CompTIA CompTIA Certifications CAS-004 Questions & Answers
-
Question 581:
A vulnerability assessment endpoint generated a report of the latest findings. A security analyst needs to review the report and create a priority list of items that must be addressed.
Which of the following should the analyst use to create the list quickly?
A. Business impact rating
B. CVE dates
C. CVSS scores
D. OVAL
-
Question 582:
A company security engineer arrives at work to face the following scenario: 1) Website defacement 2) Calls from the company president indicating the website needs to be fixed Immediately because It Is damaging the brand 3) A Job offer from the company's competitor 4) A security analyst's investigative report, based on logs from the past six months, describing how lateral movement across the network from various IP addresses originating from a foreign adversary country resulted in exfiltrated data
Which of the following threat actors Is MOST likely involved?
A. Organized crime
B. Script kiddie
C. APT/nation-state
D. Competitor
-
Question 583:
A security analyst is reviewing the following vulnerability assessment report:
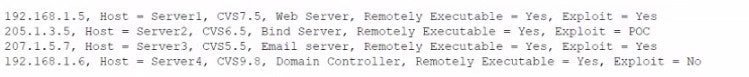
Which of the following should be patched FIRST to minimize attacks against Internet-facing hosts?
A. Server1
B. Server2
C. Server 3
D. Servers
-
Question 584:
An auditor needs to scan documents at rest for sensitive text. These documents contain both text and Images. Which of the following software functionalities must be enabled in the DLP solution for the auditor to be able to fully read these documents? (Select TWO).
A. Document interpolation
B. Regular expression pattern matching
C. Optical character recognition functionality
D. Baseline image matching
E. Advanced rasterization
F. Watermarking
-
Question 585:
A security engineer is reviewing a record of events after a recent data breach incident that Involved the following:
1.
A hacker conducted reconnaissance and developed a footprint of the company s Internet- facing web application assets.
2.
A vulnerability in a third-party horary was exploited by the hacker, resulting in the compromise of a local account.
3.
The hacker took advantage of the account's excessive privileges to access a data store and exfilltrate the data without detection.
Which of the following is the BEST solution to help prevent this type of attack from being successful in the future?
A. Dynamic analysis
B. Secure web gateway
C. Software composition analysis
D. User behavior analysis
E. Web application firewall
-
Question 586:
An attacker infiltrated an electricity-generation site and disabled the safety instrumented system. Ransomware was also deployed on the engineering workstation. The environment has back-to-back firewalls separating the corporate and OT systems. Which of the following is the MOST likely security consequence of this attack?
A. A turbine would overheat and cause physical harm.
B. The engineers would need to go to the historian.
C. The SCADA equipment could not be maintained.
D. Data would be exfiltrated through the data diodes.
-
Question 587:
An auditor Is reviewing the logs from a web application to determine the source of an Incident. The web application architecture Includes an Internet-accessible application load balancer, a number of web servers In a private subnet, application servers, and one database server In a tiered configuration. The application load balancer cannot store the logs. The following are sample log snippets:
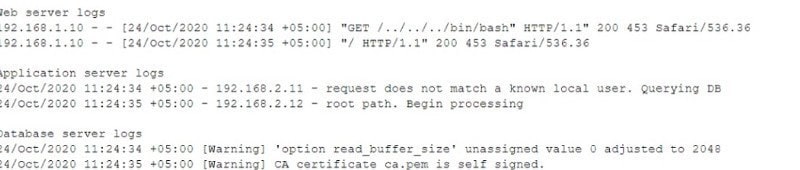
Which of the following should the auditor recommend to ensure future incidents can be traced back to the sources?
A. Enable the x-Forwarded-For header al the load balancer.
B. Install a software-based HIDS on the application servers.
C. Install a certificate signed by a trusted CA.
D. Use stored procedures on the database server.
E. Store the value of the $_server ( ` REMOTE_ADDR ' ] received by the web servers.
-
Question 588:
A security analyst is monitoring an organization's IDS and DLP systems for an alert indicating files were removed from the network. The files were from the workstation of an employee who was authenticated but not authorized to access the files. Which of the following should the organization do FIRST to address this issue?
A. Provide additional security awareness training.
B. Disable the employee's credentials until the issue is resolved.
C. Ask human resources to notify the employee that sensitive files were accessed.
D. Isolate the employee's network segment and investigate further.
-
Question 589:
An organization is designing a network architecture that must meet the following requirements:
1.
Users will only be able to access predefined services.
2.
Each user will have a unique allow list defined for access.
3.
The system will construct one-to-one subject/object access paths dynamically.
Which of the following architectural designs should the organization use to meet these requirements?
A. Peer-to-peer secure communications enabled by mobile applications
B. Proxied application data connections enabled by API gateways
C. Microsegmentation enabled by software-defined networking
D. VLANs enabled by network infrastructure devices
-
Question 590:
An enterprise is deploying APIs that utilize a private key and a public key to ensure the connection string is protected. To connect to the API, customers must use the private key. Which of the following would BEST secure the REST API connection to the database while preventing the use of a hard-coded string in the request string?
A. Implement a VPN for all APIs.
B. Sign the key with DSA.
C. Deploy MFA for the service accounts.
D. Utilize HMAC for the keys.
Related Exams:
220-1001
CompTIA A+ Certification: Core 1220-1002
CompTIA A+ Certification: Core 2220-1101
CompTIA A+ Certification: Core 1220-1102
CompTIA A+ Certification: Core 2220-902
CompTIA A+ CertificationCAS-004
CompTIA Advanced Security Practitioner (CASP+)CAS-005
CompTIA SecurityXCLO-001
CompTIA Cloud Essentials+CLO-002
CompTIA Cloud Essentials+CS0-002
CompTIA Cybersecurity Analyst (CySA+)
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only CompTIA exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your CAS-004 exam preparations and CompTIA certification application, do not hesitate to visit our Vcedump.com to find your solutions here.