Exam Details
Exam Code
:CV0-002Exam Name
:CompTIA Cloud+Certification
:CompTIA CertificationsVendor
:CompTIATotal Questions
:491 Q&AsLast Updated
:Mar 27, 2025
CompTIA CompTIA Certifications CV0-002 Questions & Answers
-
Question 481:
An administrator defines a backup as follows:
One weekly full backup Daily incremental backup
Which of the following BEST describes where the administrator would define this?
A. Backup SLA document
B. Backup orchestration workflow
C. Backup schedule
D. Provisioning schedule
-
Question 482:
A company upgraded a hosted vulnerability scanner to the latest version, and now tickets are not being created to assign critical vulnerabilities. After confirming the ticketing issue, all the scanning services are confirmed to be running on the VM. Which of the following is the MOST likely cause and best method to fix the issue?
A. There was an IP change to the VM. Make changes to the server properties.
B. The upgrade has a bug Reboot the server and attempt the upgrade again.
C. The vulnerability scanner is on a different subnet. Open the ports, and it will reconnect.
D. There is an application compatibility issue. Roll back to the previous working backup.
-
Question 483:
A company has decided to scale its e-commerce application from its corporate datacenter to a commercial cloud provider to meet an anticipated increase in demand during an upcoming holiday. The majority of the application load takes place on the application server under normal conditions. For this reason, the company decides to deploy additional application servers into a commercial cloud provider using the on-premises orchestration engine that installs and configures common software and network configurations. The remote computing environment is connected to the on-premises datacenter via a site-to-site IPSec tunnel. The external DNS provider has been configured to use weighted round-robin routing to load balance connections from the Internet.
During testing, the company discovers that only 20% of connections completed successfully.
Review the network architecture and supporting documents and fulfill these requirements: Identify the correct options to provide adequate configuration for hybrid cloud architecture.
Instructions:
If at any time you would like to bring back the initial state of the simulation, please select the Reset button. When you have completed the simulation, please select the Done button to submit. Once the simulation is submitted, please select the Next button to continue.
Simulation
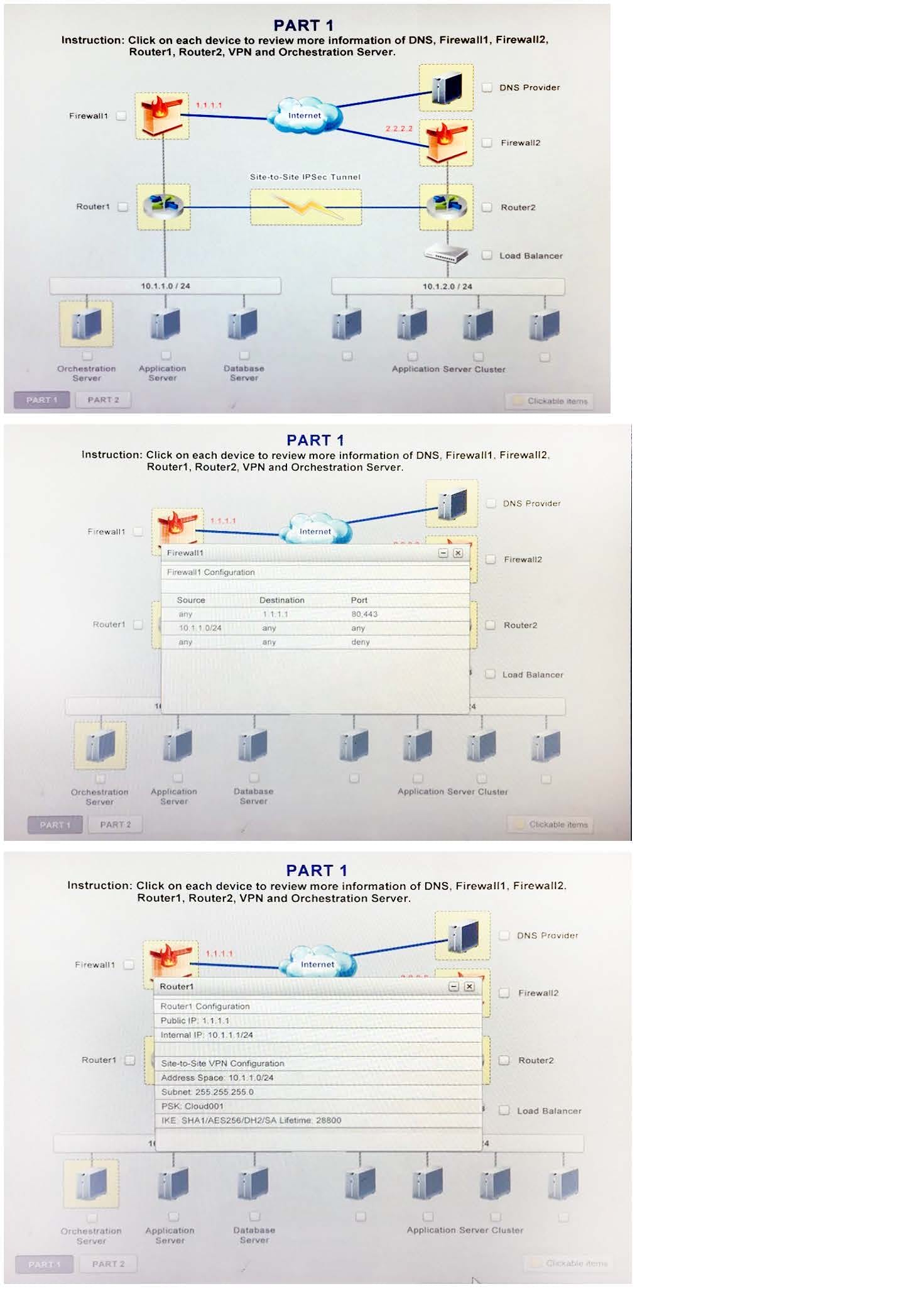
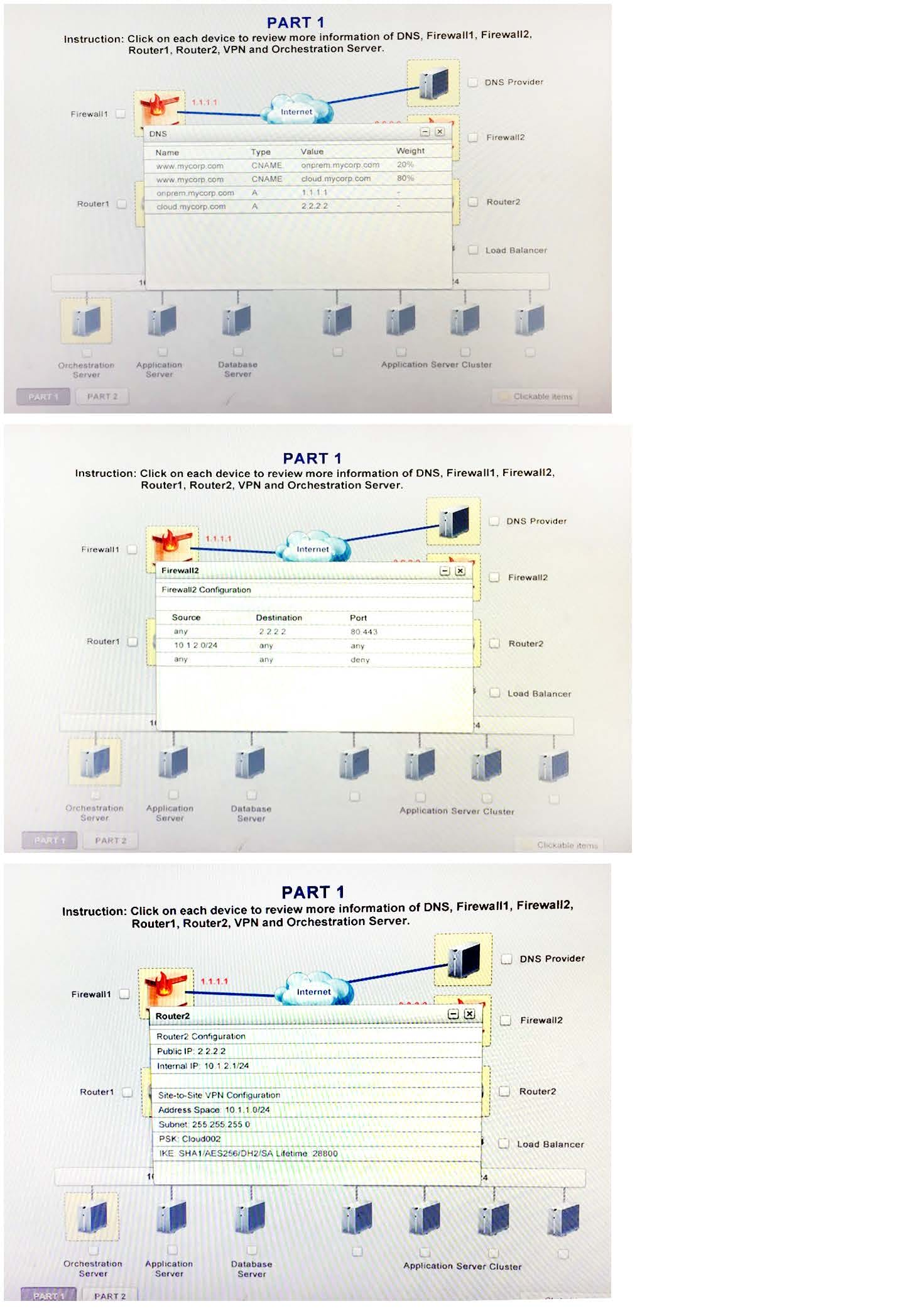
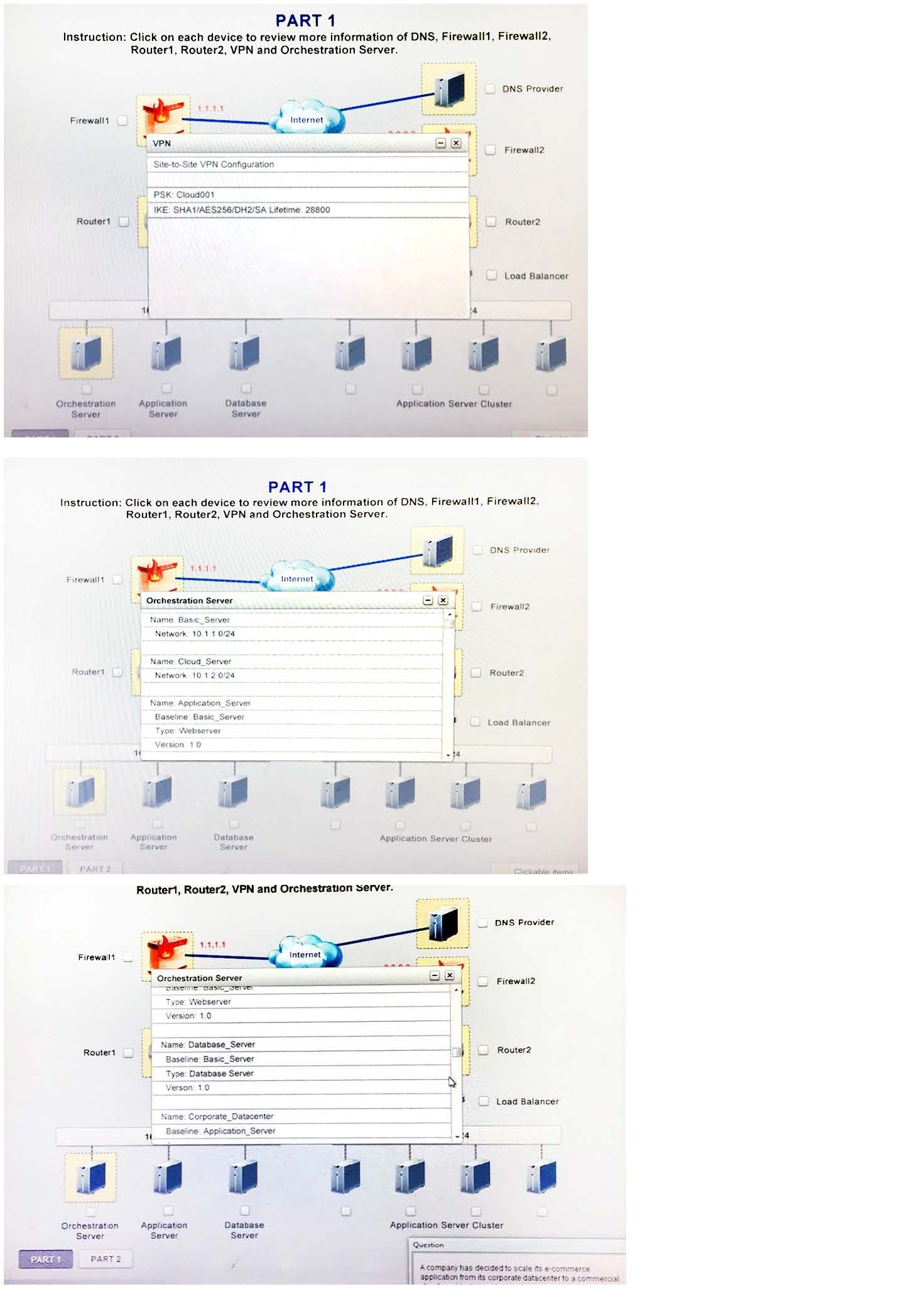
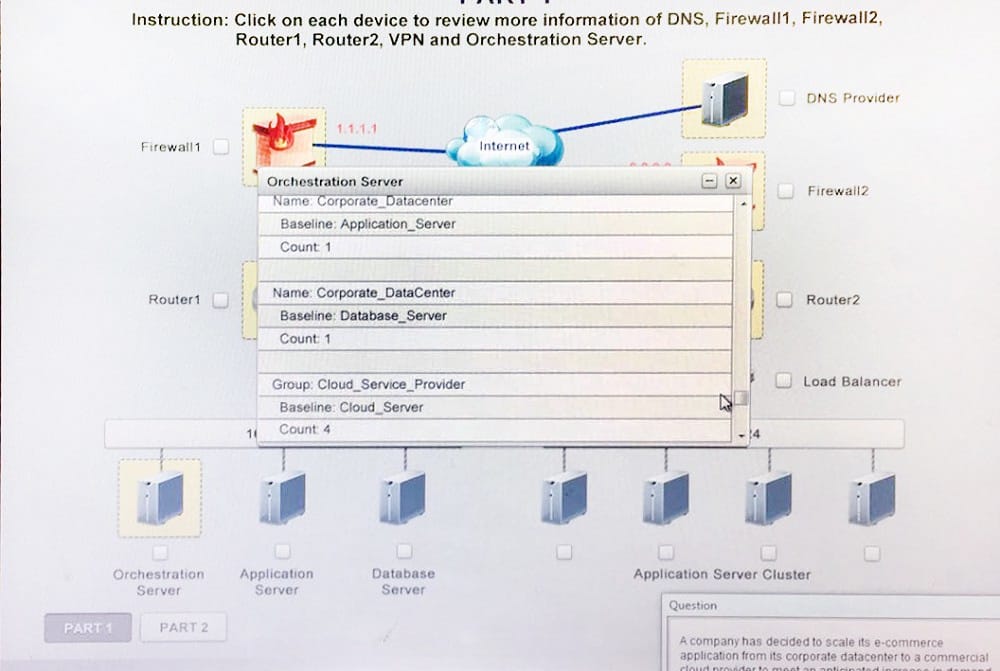
Instruction: Only select a maximum of TWO options from the multiple choice question.
A. Deploy a Replica of the Database Server in the Cloud Provider
B. Update the PSK (Pre-shared key in Router2)
C. Update the A record on the DNS from 2.2.2.2 to 1.1.1.1
D. Promote deny All to allow All in Firewall1 and Firewall2
E. Change the Address Space on Router2
F. Change internal IP Address of Router1
G. Reverse the Weight property in the two CNAME records on the DNS
H. Add the Application Server at on-premises to the Load Balancer
-
Question 484:
Joe, a systems administrator, deployed a computer and storage for a system and took it to the application team. The next day, the application team claimed the database was slow. The deployment request, result, and current utilization data are shown below.
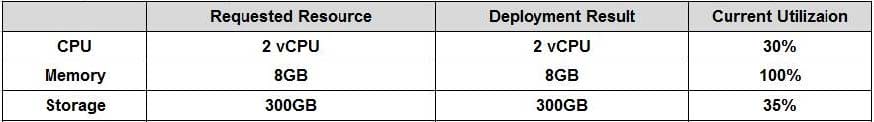
Which of the following descriptions of the situation is correct?
A. The deployment was done with the wrong memory configuration.
B. The deployment was unsuccessful due to the cloud failure.
C. The deployment was successful, but the capacity planning was inaccurate.
D. The deployment was done with the wrong storage parameter.
-
Question 485:
A consultant is helping a large company migrate its development environment to a public cloud provider. The developers are working on a VDI solution. The development tools that employees utilize require greater control of the OS environment. Which of the following cloud types should the consultant implement?
A. SaaS
B. PaaS
C. Bare metal service
D. IaaS
-
Question 486:
Which of the following would be appropriate when considering inbound access security for a web-based SaaS solution?
A. Antivirus/anti-malware
B. IPSec
C. Firewall
D. Obfuscation
-
Question 487:
Due to a competitor's unlimited data plan, a service provider is struggling and wants to transform its business services to be more hosting oriented. A cloud architect is tasked to review current cloud resource capacity and provide recommendations and a plan for better resource utilization. Given the following report:
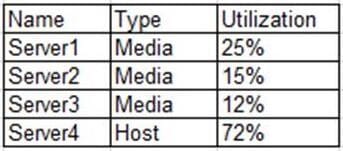
Which of the following is the BEST option for the architect to suggest?
A. Downsize by migrating all media services to one server and decommission two servers.
B. Downsize by decommissioning servers 2 and 3 and reallocate media servers to hosts.
C. Downsize by migrating all media services to one server, add one host server, and decommission one server.
D. Upsize the hosting services by turning server 1 into a host server.
-
Question 488:
A critical new security update has been released to fix an identified zero-day vulnerability with the SSH server process. Due to its severity, all development and staging servers must have this update applied immediately. Which of the following is the FASTEST way for the administrator to apply the patch and ensure all systems are configured consistently?
A. Shut down all servers and use the server provisioning tools to deploy new ones that have the latest patch applied.
B. Create a master inventory list of servers that must be patched. Log in to each server and deploy the patch, making sure to check off each server on the list.
C. Use the existing tooling to clone the existing servers. Update each clone with the latest patch and shut down the original system.
D. Update the set of configuration management scripts to include the latest patch. Execute these scripts against a master inventory of servers.
-
Question 489:
SIMULATION
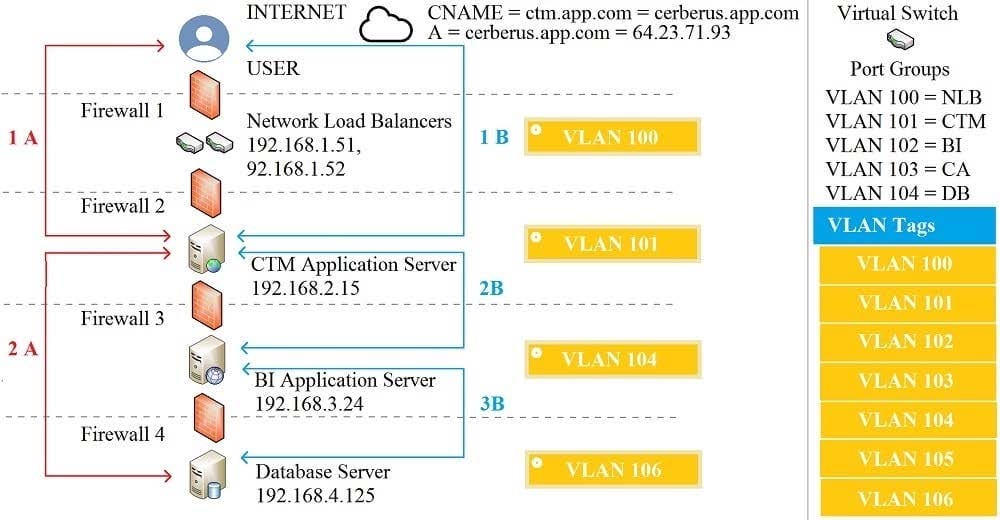
The QA team is testing a newly implemented clinical trial management (CTM) SaaS application that uses a business intelligence application for reporting. The UAT users were instructed to use HTTP and HTTPS.
Refer to the application dataflow:
1A-The end user accesses the application through a web browser to enter and view clinical data.
2A-The CTM application server reads/writes data to/from the database server.
1B-The end user accesses the application through a web browser to run reports on clinical data.
2B-The CTM application server makes a SOAP call on a non-privileged port to the BI application server.
3B-The BI application server gets the data from the database server and presents it to the CTM application server.
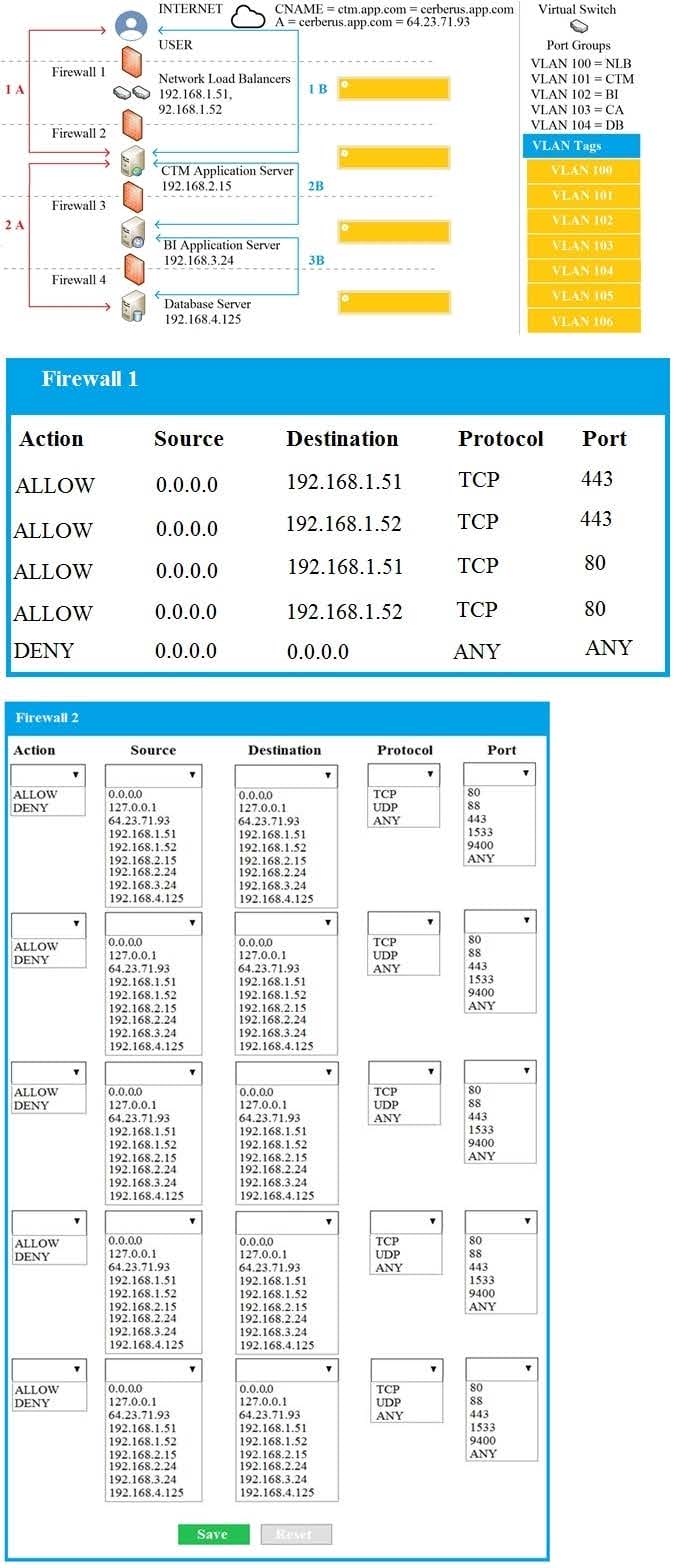
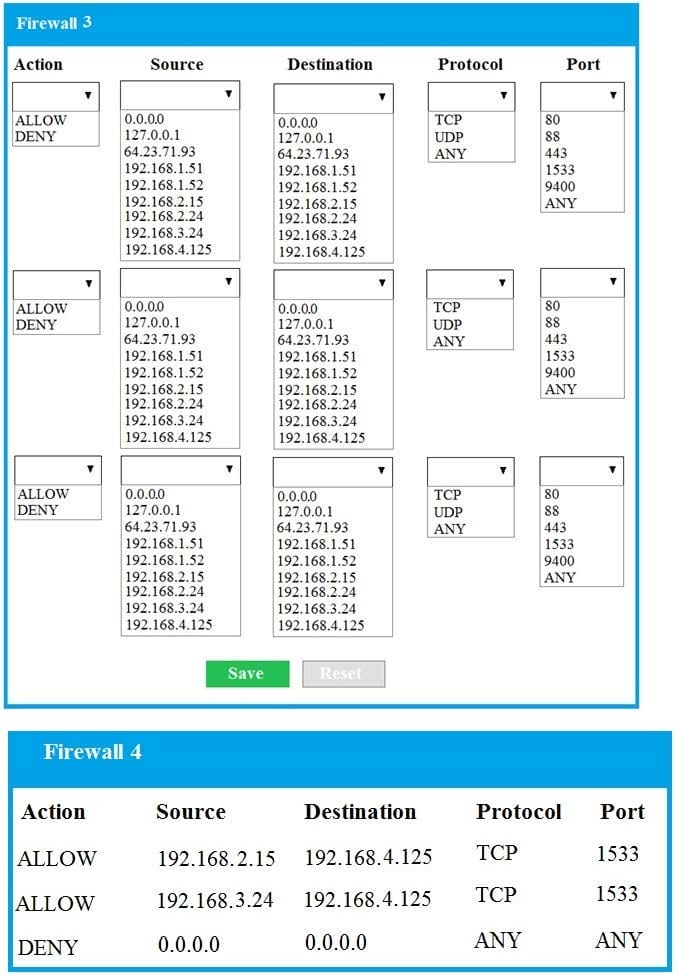
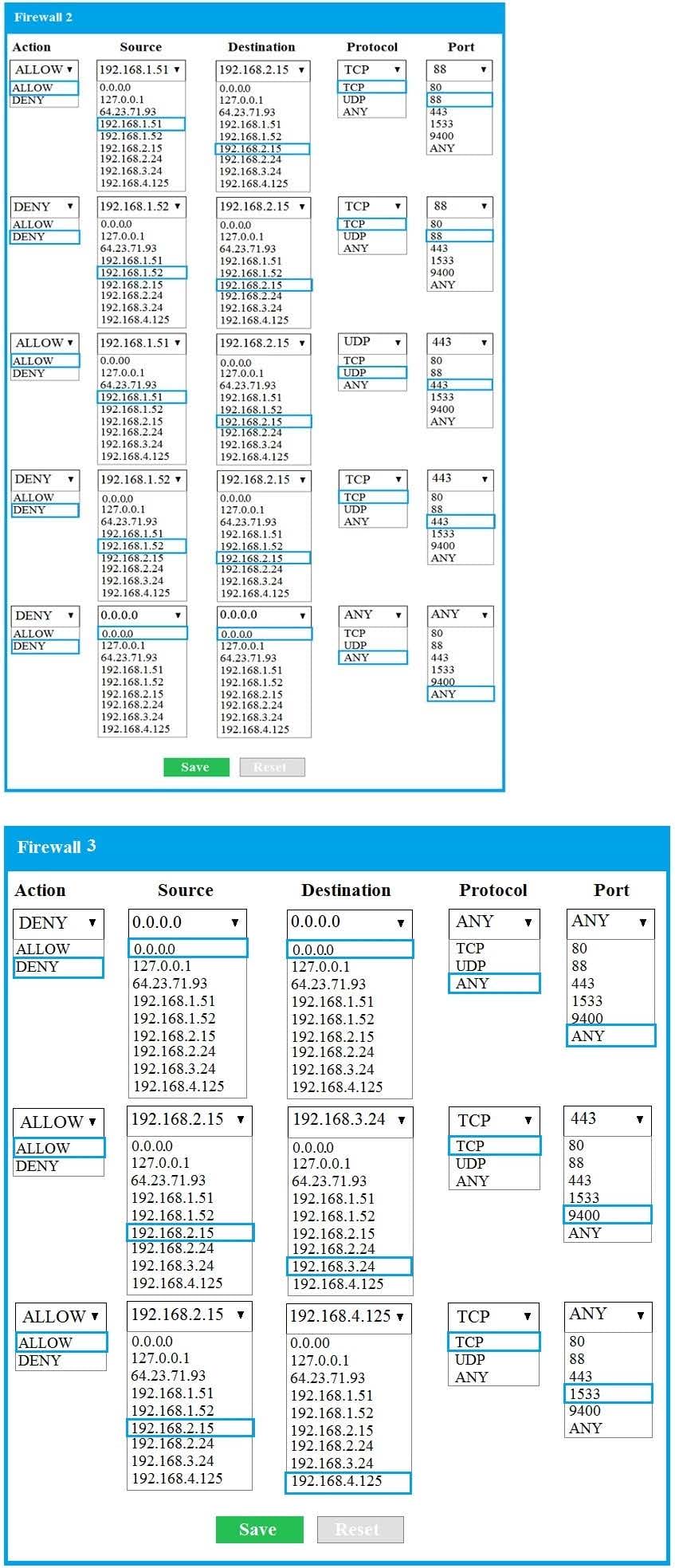
A. See explanation below.
-
Question 490:
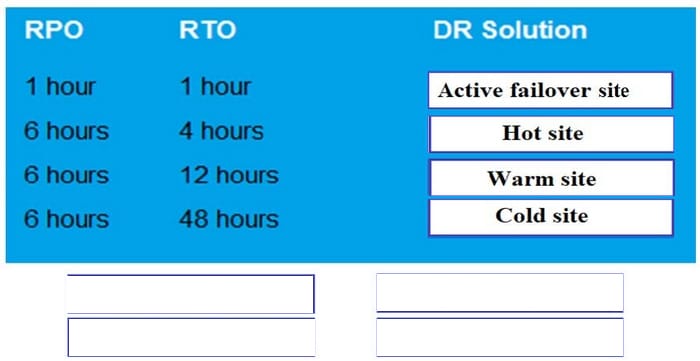
DRAG DROP
Drag and drop each Disaster Recovery Solution need to the corresponding SLA requirement. Options may be used once or not at all.
Select and Place:
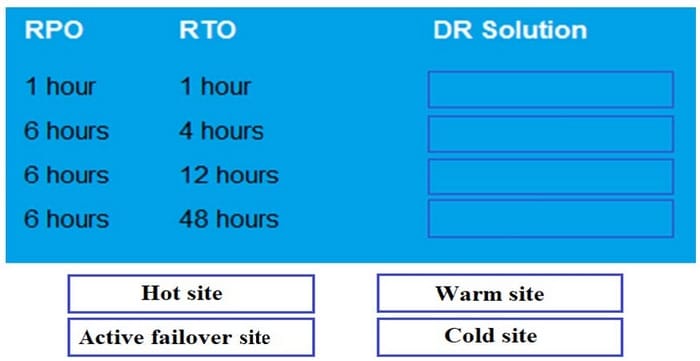
Related Exams:
220-1001
CompTIA A+ Certification: Core 1220-1002
CompTIA A+ Certification: Core 2220-1101
CompTIA A+ Certification: Core 1220-1102
CompTIA A+ Certification: Core 2220-902
CompTIA A+ CertificationCAS-004
CompTIA Advanced Security Practitioner (CASP+)CAS-005
CompTIA SecurityXCLO-001
CompTIA Cloud Essentials+CLO-002
CompTIA Cloud Essentials+CS0-002
CompTIA Cybersecurity Analyst (CySA+)
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only CompTIA exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your CV0-002 exam preparations and CompTIA certification application, do not hesitate to visit our Vcedump.com to find your solutions here.