Exam Details
Exam Code
:D-ISM-FN-23Exam Name
:Dell Information Storage and Management Foundations 2023 ExamCertification
:DCA-ISMVendor
:EMCTotal Questions
:60 Q&AsLast Updated
:Nov 15, 2024
EMC DCA-ISM D-ISM-FN-23 Questions & Answers
-
Question 1:
Which statement is true regarding virtual provisioning?
A. Multiple shared storage pools can be created while each pool must be allocated to a unique thin LUN
B. Shared and Thin LUNs can be expanded rapidly with only minor disruptions
C. Virtual provisioning enables more e cient allocation of storage to compute systems
D. Virtual provisioning prevents issues that arise from oversubscription
-
Question 2:
What provides ow control in FCIP?
A. Overlay Flow Control Protocol
B. Transmit Flow Control Protocol
C. Transmission Control Protocol
D. Ethernet Flow Control Protocol
-
Question 3:
If the erasure coding technique used divides data into 12 data segments and 5 coding segments, what is the maximum number of disk drive failures against which data is protected by the con guration?
A. 5
B. 7
C. 3
D. 17
-
Question 4:
What is a bene t of implementing a big data ecosystem?
A. Applies new processing and management methods to derive better business value from unstructured data
B. Implements new technical and analytical methods to derive business value from large object data
C. Applies new processing and management methods to improve large relational database response performance
D. Implements new technical and analytical methods to derive business value from large datasets
-
Question 5:
A Fibre Channel switch has eight ports and all ports must be operational from 8 AM to 8 PM, Monday through Friday. However, a failure of Port 7 occurs in the week as follows:
Monday = 11 AM to 12 PM Wednesday = 4 PM to 9 PM Thursday = 4 AM to 9 AM Friday = 2 PM to6 PM Saturday = 9 AM to 1 PM
What is the availability of Port 7 in that week?
A. 75%
B. 83.3%
C. 80%
D. 68.3%
-
Question 6:
In continuous data protection, what does the amount of journal space determine?
A. Amount of data that can be restored to a speci c point
B. Length of time required to recover the data
C. How far back the data can be recovered
D. Amount of space the source and replica volumes require
-
Question 7:
Which option shows the correct sequence of steps to perform a data recovery operation?
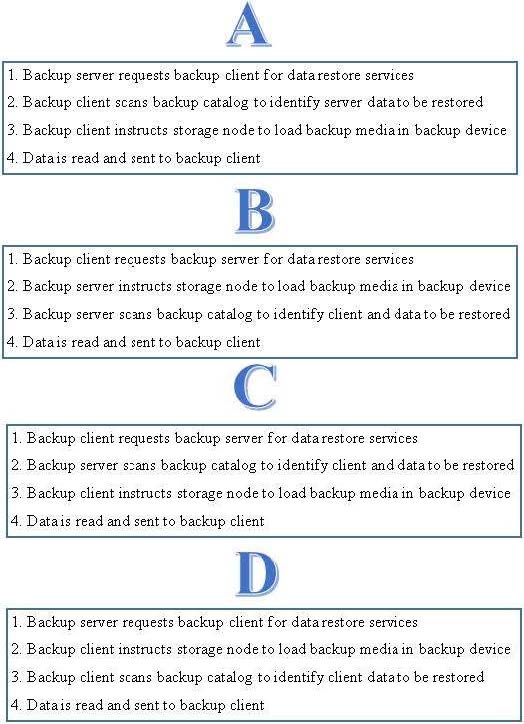
A. A
B. C
C. D
D. B
-
Question 8:
What method does FCIP use to transport Fibre Channel SAN data?
A. FCIP encapsulates and tunnels FC SAN data over Ethernet networks.
B. FCIP encapsulates and tunnels FC SAN data over IP networks.
C. FCIP splits LAN and FC SAN data and tunnels FC SAN data over Ethernet networks.
D. FCIP separates LAN and FC SAN data and tunnels FC SAN data over IP networks.
-
Question 9:
Under the PaaS model, which elements are managed by the consumer?
A. Applications and Data
B. OS and Runtime
C. Middleware and Networking
D. OS and Virtualization
-
Question 10:
An organization wants to replicate their data by extending the local network across a public network. Prior to implementing replication, they need to secure the network. Which security control mechanism is recommended?
A. Virtual storage area network
B. Demilitarized zone
C. Virtual local area network
D. Virtual private network
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only EMC exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your D-ISM-FN-23 exam preparations and EMC certification application, do not hesitate to visit our Vcedump.com to find your solutions here.